Manage Your Keys
Learning Objectives
After completing this unit, you’ll be able to:
- Define the key management lifecycle.
- Explain the different approaches to key management solutions (KMS).
Key Management Lifecycle
Now that you’ve learned how to keep your production secrets safe, let’s talk about the key management lifecycle and why it’s equally important for security. While there are many phases to this lifecycle, key management focuses on creating, maintaining, securing, and controlling the use of cryptographic keys. Monitoring this process allows you to assure that the keys are properly created and deployed. There are four phases to the key management lifecycle, which are important to securing production secrets.
- Key Creation and Activation
- Key Revocation
- Key Escrow (Backup)
- Key Deletion (Destruction)
Let’s take a closer look at each.
Key Creation and Activation
A key manager creates the encryption key and stores it in a key storage database along with its attributes: name, activation date, size, and so forth. You can activate keys at creation or set them to activate later.
Key Revocation
Any key administrator can use the key manager to revoke a key. This places the key in an invalidated state and it can no longer be used for cryptographic purposes like encryption and decryption. If needed, you can reactivate revoked keys. An example of this may be when an old key is required to decrypt data previously encrypted with it.
Key Escrow (Backup)
Key escrow allows for keys to be securely archived when they deactivate. Much like key revocation, you can reactivate archived keys if required.
Key Deletion (Destruction)
When a key is no longer necessary or has become compromised, an admin may choose to delete it from the storage database. This removes all or certain instances from the database, making recovery impossible (outside of any stored backups). Should a key become compromised, an admin can immediately delete it, allowing your data to remain secure.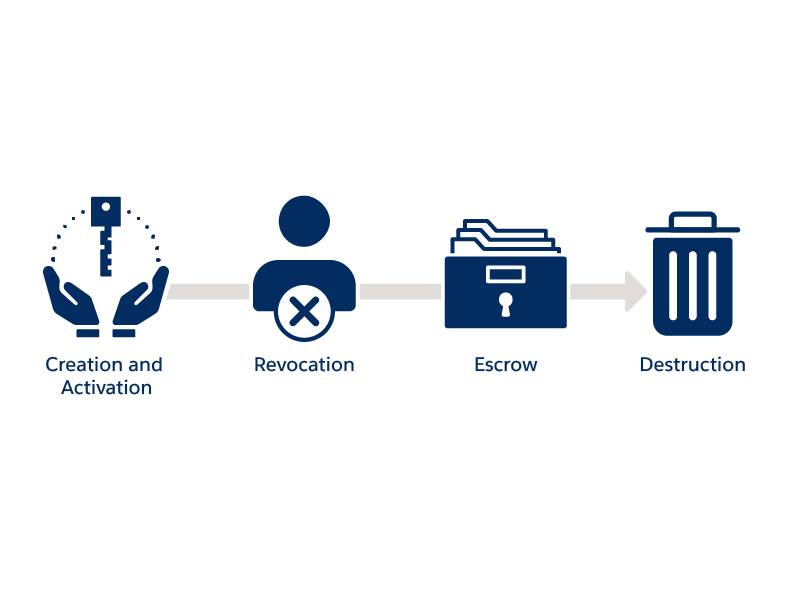
KMS Strategies
An organization can take one of several different approaches when it comes to key management strategies: decentralized, distributed, or centralized.
Manage Your Keys—Decentralized (Local)
A decentralized key management solution (DKMS) or local key management is an approach to key management where no central authority exists. Individuals bear all the responsibility for creating, securing, managing, and destroying cryptographic keys. An example of this is local backup encryption or a local file vault on a computer.
Manage Your Keys—Distributed (Siloed)
Another approach is to use a distributed or siloed key management approach, where you consolidate the management for a particular application or system. A common example of this is full disk encryption that is used in large enterprise organizations. The keys for the disk encryption are all managed by a central application that is used specifically for that one purpose.
Manage Your Keys—Centralized
There is also the option of using a dedicated and centralized KMS (CKMS). Distributed key management solutions become increasingly difficult to manage as your company grows. A CKMS can unify key management across your entire company allowing for scale with the needs of the business. Benefits of a CKMS include providing tamper-evident records for proof of compliance along with streamlining key management processes, automatic key updates, and backup and recovery options.
It’s important to note that all of the above methods are available within the cloud, as well as your company’s on-premise system for key management. However, if scalability, auditing, and security are of high concern, CKMS is ideal. By managing keys in a centralized fashion, you reduce operational burdens and associated costs, while maintaining the confidentiality and integrity of your keys.
Sum It Up
In this module, you’ve been introduced to the phases of the key management lifecycle. You’ve also learned about different approaches to key management. Interested in learning more about cybersecurity best practices? Check out the Cybersecurity Learning Hub on Trailhead.