Evitar la exposición de credenciales en el código
Objetivos de aprendizaje
Después de completar esta unidad, podrá:
- Identificar por qué la exposición de la información secreta puede ser un problema en su organización.
- Explicar cómo prevenir la exposición accidental de la información secreta.
Exposición de credenciales
Una de las vulneraciones más comunes de la seguridad de los datos procede de los datos confidenciales almacenados en el código que se desarrolla. Por este motivo, es necesario aprender a proteger estos datos (incluidas las credenciales, las claves de cifrado, etc.), que podrían permitir a los atacantes poner en peligro los datos confidenciales de su organización si cayeran en las manos equivocadas.
Quien trabaja como desarrollador es responsable del código y los scripts que acceden a pilas tecnológicas como la nube, las aplicaciones y otras herramientas. Todas estas instancias suelen requerir credenciales, y es vital protegerlas para que no queden expuestas.
Muchos grupos que trabajan en desarrollos cíclicos extienden sus plazos de entrega, y, a menudo, se presiona para trabajar a toda velocidad. Puede que los desarrolladores utilicen GitHub u otros repositorios de código abierto para colaborar entre sí y completar proyectos.
El riesgo de exposición de las credenciales surge en los repositorios de código porque, a veces, los desarrolladores ocupados introducen credenciales en su código como acceso directo. Así, cuando se publica el código, las credenciales de la organización pasan a ser de dominio público. Una vez enviado el código, borrarlo no resulta fácil. E incluso si su sistema de control de versiones le permite borrar el código que se ha puesto en peligro, otro desarrollador o servicio puede haber sacado ya una copia de este antes de su eliminación.
Esto significa que cualquiera que sepa trabajar con el control de versiones o haya hecho una copia del código puede extraer estas credenciales, incluso del pasado, y acceder a ellas. Si no se aplican convenciones y prácticas de codificación seguras, los desarrolladores pueden revelar accidentalmente credenciales a personas no autorizadas, lo que les permite acceder a los sistemas centrales.
Es un error fácil y común que cometen los desarrolladores cuando se apresuran a poner su nueva función a disposición de los clientes. Esto significa que debe estar aún más atento para asegurarse de que nunca se incluyan credenciales en el código.
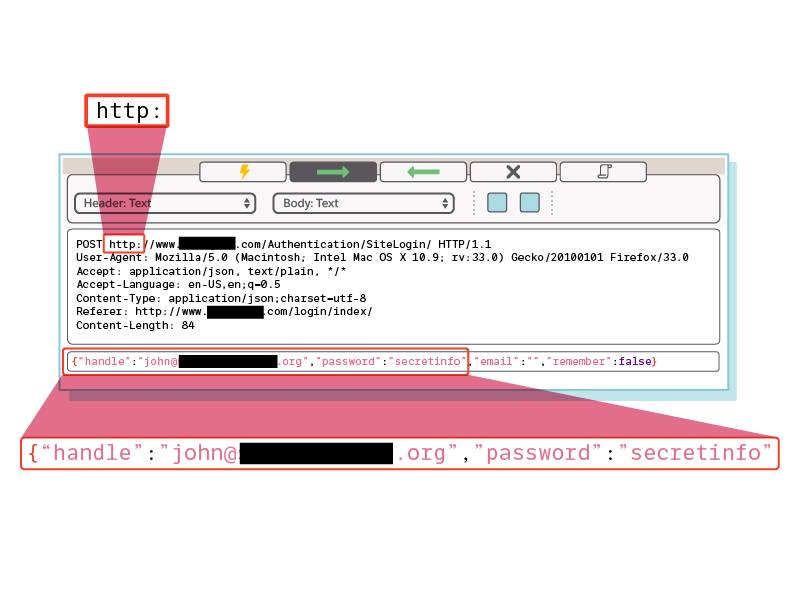
Filtración de credenciales
Hace años que los servicios de seguimiento de software como GitHub, Bitbucket y SourceForge dedican esfuerzos a mitigar el problema de la filtración de credenciales. Algunos de estos servicios incluso alertan al usuario si envía un token de acceso a un repositorio público y revocan esos tokens para que no puedan utilizarse para realizar acciones no autorizadas. A pesar de ello, sigue siendo habitual que los repositorios incluyan por error tokens y claves de interfaces de programación de aplicaciones (API).
Es probable que su organización sea consciente de este problema. Y su equipo de seguridad debe comprobar periódicamente los identificadores de usuario, las claves API, los tokens de acceso, los archivos de bases de datos y otras claves expuestas accidentalmente en el código de repositorios públicos o instancias en la nube.
Cómo evitar la exposición de credenciales
Del mismo modo que es una buena práctica integrar el ciclo de vida del desarrollo seguro en su proceso de desarrollo, también es una práctica recomendada instituir la higiene de la gestión de credenciales en cada paso de sus procesos de codificación. Recuerde dos puntos importantes para mantener su código a salvo de la exposición de credenciales.
- Almacene la información secreta solo en el servicio de gestión de dicha información aprobado por su organización.
- Nunca incluya secretos en su código.
En los módulos siguientes de la ruta de formación Implementar la gestión de información secreta en la organización, que incluye Infraestructura y cifrado de claves públicas y Gestión de claves, abordamos las prácticas recomendadas para ayudarle a gestionar las claves que protegen su información secreta, así como la manera de proteger dicha información cuando se transmite y cuando está almacenada.
Resumen
En este módulo se han presentado métodos para crear y proteger contraseñas seguras, así como las ventajas de los gestores de contraseñas. También ha aprendido a aplicar el principio del mínimo privilegio en la gestión del acceso privilegiado y la importancia de supervisar sus usuarios y cuentas a lo largo del tiempo.
Junto con la información que ha revisado en el módulo de Secretos de la organización, ahora debería entender mejor lo que se necesita para proteger la información secreta de su organización, lo que incluye las credenciales de acceso. En el módulo siguiente, Infraestructura y cifrado de claves públicas, cubrimos los métodos para proteger sus datos en tránsito y en reposo. Para obtener más información sobre prácticas recomendadas de ciberseguridad y escuchar a auténticos profesionales de la seguridad, visite Cybersecurity Learning Hub en Trailhead.