Encrypt Data at Rest
Learning Objectives
After completing this unit, you’ll be able to:
- Define the risks to data at rest.
- Explain encryption best practices to protect data at rest.
What Is Data at Rest?
Data at rest is the data housed on computer data storage in any digital form, whether it's in cloud storage, file hosting services, or databases. Data at rest can even include physical data stored in warehouses, spreadsheets, archives, or tapes. For the purposes of this module, data refers to electronic data.
Depending on the core business of your organization, data at rest can be one of the most valuable assets you have. That’s why this type of data is subject to threats from attackers. To prevent this data from being accessed or stolen, organizations often employ security protection measures such as password protection, data encryption, or a combination of both. Let’s take a closer look at encryption of data at rest.
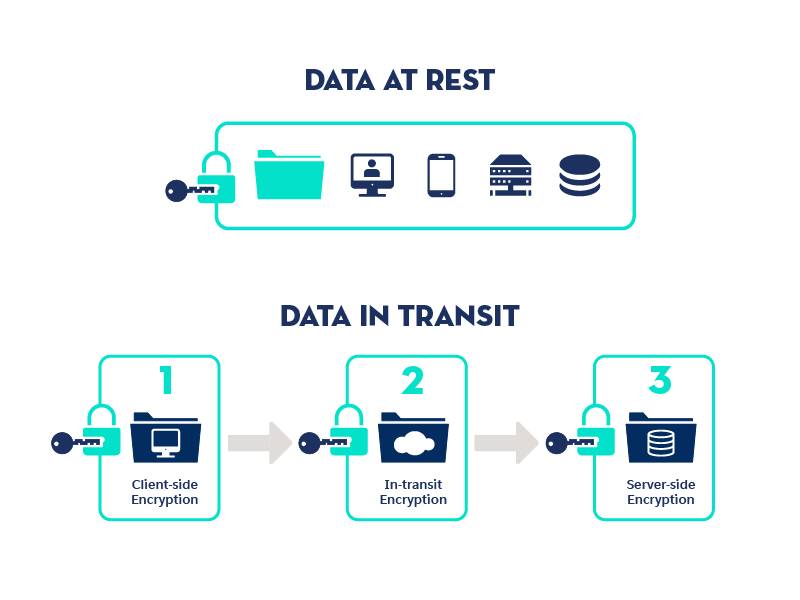
Use Encryption to Secure Organization Data at Rest
Just as it’s crucial to encrypt data in transit, it’s also important to encrypt sensitive data at rest. This is to ensure that you handle private data securely, and that it stays private. Your goal when encrypting data at rest should be to implement a solution that prevents data visibility in the event of unauthorized access or theft.
When protecting data at rest, you want to make sure that encrypted data remains encrypted when other controls fail. Sometimes this is done by combining network segmentation and increasing levels of encryption. Encrypting data on multiple levels is a good way to enhance its safety.
At a minimum, you should:
- Implement cryptography on the database housing the data and on the physical devices where the databases are stored.
- Update data encryption keys on a regular basis.
- Store encryption keys separately from the data.
- Enable crypto-shredding at the end of the data or hardware lifecycle.
- Audit sensitive data at scheduled intervals.
- Store only the minimum amount of sensitive data.
While there are many ways to configure encrypted data at rest systems, here are some basic best practices.
Asymmetric cryptography (also known as public-key encryption) uses the difficulty of certain math problems to give you a pair of keys, each of which can be used to encrypt a message so that only the other key in the pair can decrypt it. That means anyone can use the public key to hide something, and only the holders of the private key can unlock it. The holders of the private key can also “sign” any message, and anyone in the world can use the public key to verify it was really signed by them.
Asymmetric encryption is more secure than symmetric encryption as it uses two keys for the process. In a symmetric key system, the same key is used for both encryption and decryption, while in an asymmetric system, the encryption key is public and distinct from the decryption key, which is kept secret. Asymmetric cryptography tools include authentication tokens, Docker or Java’s JCA.
Hardware security module (HSM) is hardware that holds private keys and it can be used without disclosing them. While it's running, you can put public-key encrypted information on one end and get decrypted information out of the other, and nobody can ever discover the private key.
Defense in depth means applying controls at different layers of your technology stack so that you don’t rely on just one control to protect your data. One way to implement defense in depth when it comes to encryption is to combine your encryption capabilities with asymmetric cryptography and HSM. This means that even if parts of the system are compromised, it is still difficult to access all the data.
Strong encryption methods include Advanced Encryption Standard (AES) or Rivest–Shamir–Adleman (RSA). These are both encryption standards used by governments, technology companies, and other organizations. The difference between them is that AES is a symmetric key system, and RSA is an asymmetric key system. This means that AES uses the same key for encryption and decryption, while RSA uses different keys to encrypt and decrypt data.
Sum It Up
In this module, you’ve learned more about protecting data transmission with TLS and PKI, and encrypting data at rest. Using these methods across the board minimizes the chance that attackers can access it. You can learn more about best practices in cybersecurity from real security practitioners by visiting the Cybersecurity Learning Hub on Trailhead.
Resources
-
External Site: National Institute of Standards and Technology (NIST): Advanced Encryption Standard (AES)
-
External Site: NIST: Measuring and Improving the Effectiveness of Defense-in-Depth Postures