Integrate Security Controls
Learning Objectives
After completing this unit, you’ll be able to:
- Define the relationship between secure information and leadership decisions.
- Explain the value of security controls.
Secure Decision-Making
People with authority, from parents and teachers to CEOs and political leaders, have the power to shape outcomes with their decisions. History has proven that leaders’ decisions matter, and therefore, the information that informs those decisions is equally important.
In today’s digital age, where information processing and delivery relies heavily on interconnected systems and the internet, ensuring the integrity and trustworthiness of data has become critical. This is especially true for leadership decision-making in politics, business, and other positions of power where decisions may have far-reaching consequences.
Consider these examples.
-
Leadership decisions undermined: A hospital’s chief of security has just implemented strict ID badge checks for staff entering restricted areas. However, a security breach in the hospital’s electronic system has bypassed the security checks granting unauthorized access to any individual entering restricted areas. The chief must now work with the hospital CEO and other C-suite executives to manage the hospital’s reporting requirements and other legal or reputational damage that may result from the breach.
-
Leadership decisions compromised: A global financial company made investment decisions based on what appeared to be precise and current market data. However, a malicious cyber intruder had slightly altered the data used to forecast investment outcomes. Use of this data resulted in an unexpected, catastrophic drop in its portfolio’s value, which had severe repercussions for its clients and stakeholders.
-
Leadership decisions delayed: A large logistics company is preparing for a major acquisition that could transform its market standing. However, a ransomware attack disrupts its operations by encrypting critical information essential for evaluating the acquisition’s viability. Faced with this dilemma, the leadership must choose: Proceed with the acquisition using incomplete information risking unforeseen consequences, or postpone and possibly lose a valuable opportunity. Each choice poses a threat to the company's credibility and could lead to significant financial losses.
These scenarios underscore the critical importance of accurate information in leadership decision-making. When information, or its supporting systems are compromised or corrupted, the quality of the leader’s decisions is directly affected. Leaders’ decisions have far-reaching consequences, impacting lives and livelihoods both within and outside organizations. Therefore, it’s imperative to protect and secure information, information technology, and information systems where data is stored, processed, and managed so that crucial information remains accurate, confidential, and available when needed.
The Cost of Cyber Defense
The Center for Internet Security (CIS) recognizes the importance of safeguarding information and has created a guide, The Cost of Cyber Defense, to help businesses establish a strong cybersecurity foundation. The guide emphasizes that securing and protecting critical information doesn’t have to be expensive. It outlines a prioritized set of actions that can be implemented to form an effective cyber defense program starting with Implementation Group 1 (IG1) of the CIS security controls.
A “control” is a best practice recommendation and is intended to influence behavior. For example, when we obey a stop sign, exit through a door marked Exit, or sit in a waiting room, we are responding to controls designed to regulate our behavior in a specific environment. Similarly, in the realm of cybersecurity, security controls such as acceptable use policies, login credentials for accessing websites, and firewall rules are controls, or best practice recommendations, intended to influence behavior on a digital network.
The purpose of the guide is to provide businesses with a picture of how realistic and cost effective it can be to achieve essential cyber hygiene. Represented within 10 control categories, businesses can make a reasonable effort to:
-
Identify (track) what data it has and prioritize which aspects require the greatest protection.
-
Protect what it has commensurate to the harm that could occur if there is an attack.
-
Detect attacks.
-
Respond to attacks to minimize damage to its assets and possible harm to all stakeholders.
-
Recover from attacks.
The CIS guide provides a model for prioritizing security controls and safeguards that are affordable and will help businesses defend themselves against cyberattacks.
It’s crucial for decision-makers to recognize that controls are not just compliance requirements. They’re fundamental components that help an organization operate as intended–much like the essential parts of a car. Just as one would not regard the brakes of a car as optional, cybersecurity controls are integral to the function of every IT system (for example, payroll system, email provider, hiring solution) that supports an organization’s mission.
The Value of Security Controls
Security controls, like financial controls, establish clear rules and parameters for how resources are accessed, used, and shared within an organization. While financial controls ensure responsible fiscal management, security controls promote responsible data and information management.
Consider a simple scenario where a business’s customer database contains sensitive details like names, addresses, and payment information. Without security controls, this information is at risk of exposure to anyone with system access: an employee, a partner, or even a competitor. By implementing a security control like access control lists (ACLs), the business can transform this risk into a strategic advantage.
Access control lists act as digital gatekeepers, ensuring employees only see information relevant to their roles. Sales and billing can only view transaction details. Customer service can only access information to assist clients. Marketing is only given access to information for targeted campaigns. And unauthorized individuals are blocked from accessing the network.
However, security controls aren’t just about implementing security measures to eliminate vulnerabilities or reduce the attack surface of network, systems, and applications. They’re the tools that leaders use to own, intelligently manage, and actively influence how data and information flows within and outside the organization.
To illustrate the strategic value and impact of security controls, the table lists the 10 control categories, their individual impact on critical information, a relatable analogy, and explanations highlighting their impact on the business. A vehicle is the relatable analogy for the 10 control categories because, like a business’s IT systems, it’s a familiar system with many interconnected parts. Each control category can be likened to a specific vehicle component, each playing a crucial role in maintaining smooth operation. This analogy helps illustrate how these controls work together to protect IT systems and the digital information they transmit, process, and store.
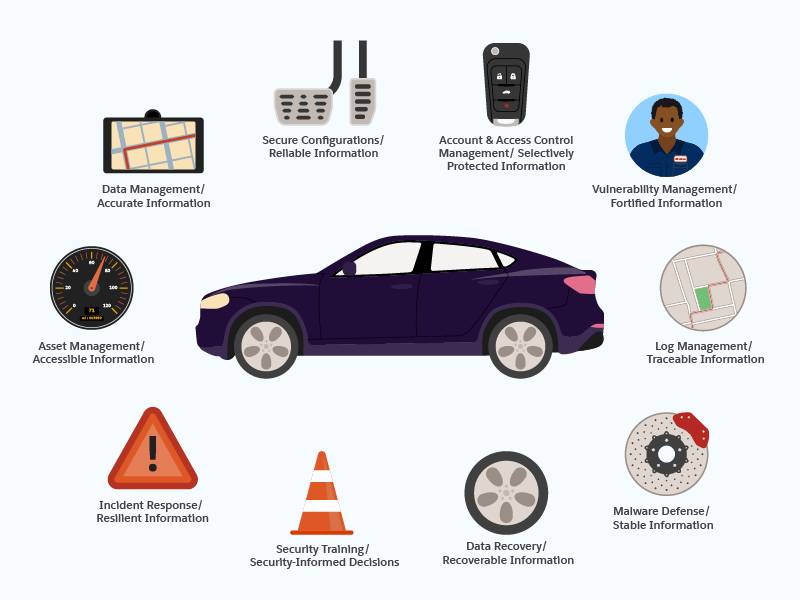
Control Category |
Information Impact |
Business Impact |
Car Example |
|---|---|---|---|
Asset Management |
Accessible Information
|
Asset management ensures you can quickly locate and use the data and information you need for critical decision-making. |
Dashboard of the car provides real-time information at a glance |
Data Management |
Accurate Information |
Data management ensures you have the most accurate and current information to make informed business decisions. |
A navigation system that provides up-to-date map and traffic information |
Secure Configurations |
Reliable Information |
Secure configurations ensure information systems remain secure and predictable. |
Driving with properly adjusted brakes |
Account and Access Control Management |
Selectively Protected Information |
Account and access control management ensures only authorized users can access sensitive information maintaining information integrity and confidentiality. |
Using a secure key fob to operate your car |
Vulnerability Management |
Fortified Information
|
Vulnerability management proactively addresses system weaknesses to prevent exploits, keeping data and information secure and accessible. |
Taking your car in for regular tune ups and fixing recalls |
Log Management |
Traceable Information |
Log management provides an audit trail, enabling quick detection and response to security incidents, ensuring the tracking and traceability of information. |
Using a navigation system to monitor and track your speed, route, and location |
Malware Defense |
Stable Information |
Malware defense preserves the integrity of systems and information by preventing malicious software from modifying, disrupting or taking control. |
Having an anti-lock braking system preventing the wheels from locking up during sudden braking |
Data Recovery |
Recoverable Information |
Data recovery ensures efficient restoration of critical information in case of accidental deletion, system failure, or disaster, maintaining continuous access to information. |
Having a spare tire in your car to ensure you can quickly recover from a flat and continue your journey |
Security Training |
Security-Informed Decisions |
Security training proactively prepares employees to make security-conscious decisions throughout their work day enhancing overall organization safety and security. |
Driver’s education to learn the rules of the road and best practices for optimizing safe driving |
Incident Response |
Resilient Information |
Incident response provides a structured approach to address security incidents, minimize damage, preserve evidence, and quickly restore normal operations, ensuring the integrity and resilience of critical information. |
Using roadside assistance when your car breaks down, ensuring you have support to get back on the road |
As you can see, security controls do much more than prevent and reduce the impact of a security incident. When information technology and information systems are integral to a business's success, well-designed security controls are the tools that provide leaders with the ability to strategically manage information assets aligning them with business goals and risk tolerance. These controls empower leaders to make risk-informed decisions and to decisively use the cybersecurity program as an asset, directly contributing to the organization’s overall growth and resilience.
Now that you understand the role and value of security controls, consider your own business and the information systems you rely on. Reflect on how crucial accurate, stable, and accessible information is to your operations.
Is safeguarding this information worth the investment?
In the next unit, we explore budget-friendly controls that ensure the cybersecurity program upholds integrity and trustworthiness, prioritizing the most pressing security concerns.
Resources
- External Site: Aptien: What is an information asset?
- Trailhead: Cyber Resilience Program Development
- Trailhead: The Center for Internet Security Critical Security Controls
- Blog: SANS: The New Financial Metric for Cybersecurity
- External Site: Dark Reading: Security Is a Revenue Booster, Not a Cost Center
