Manage Operational Risks
Learning Objectives
After completing this unit, you’ll be able to:
- Describe how to manage risks using cost-benefit analysis.
- Explain how to use a risk register to monitor and evaluate operational risk.
- Identify how to manage risks during a cybersecurity incident.
Manage Risks Using Cost-Benefit Analysis
Risk management is a daily activity in cybersecurity, so you need ways to prioritize which risks should be addressed first. You can use cost-benefit analysis, coupled with a risk register, to help you efficiently monitor and communicate risk. This helps you prioritize the most important risks.
When managing cyber risks, you start by considering your most important assets and the impact that would occur if those assets were compromised or unavailable. You assess which types of vulnerabilities exist that could provide an opening for adversaries, and which types of threat actors are interested in gaining unauthorized access or denying availability to your systems and data. You then think about how to manage risk to prevent negative impacts from occurring. You can use policies, financial resources, staff commitments, and technical controls to manage risks.
When you think about how to manage a risk, it’s helpful to consider the cost of doing so versus the benefit. If a given intervention costs more than the value gained from it, you may choose to accept the risk rather than mitigate it, and plan to address it at a later time when a more viable mitigation becomes available.
You might also find that it’s too expensive to mitigate the risk with in-house resources, but that you can transfer the responsibility of mitigating to another party, such as an insurance provider or third-party service provider. As you examine these decisions, your efforts to put a dollar and cents number to the costs and benefits of each risk decision can help your organization better manage risk in ways that make sense to all members of the business. By providing data-driven insights into cybersecurity, you can empower your organization to make better risk-informed decisions and create a more secure technology ecosystem.
Monitor and Evaluate Your Organization’s Cybersecurity Safeguards
Winston Churchill famously said, “However beautiful the strategy, you should occasionally look at the results.” As an executive cyber leader, you lead security monitoring and analytics for your organization across all your information technology (IT) and business assets including endpoints, networks, and cloud environments in order to detect malicious activity and respond. Monitoring describes the process of detecting cyber threats and data breaches, and it’s a crucial part of cyber risk management that enables your organization to detect cyberattacks in their infancy and respond to them before they cause damage and disruption.
Monitoring is key to stopping exploits before they do damage because it enables you to identify vulnerabilities and patch systems to thwart attackers and decrease risk. It allows you to identify unusual patterns of usage or other activities that may appear suspicious.
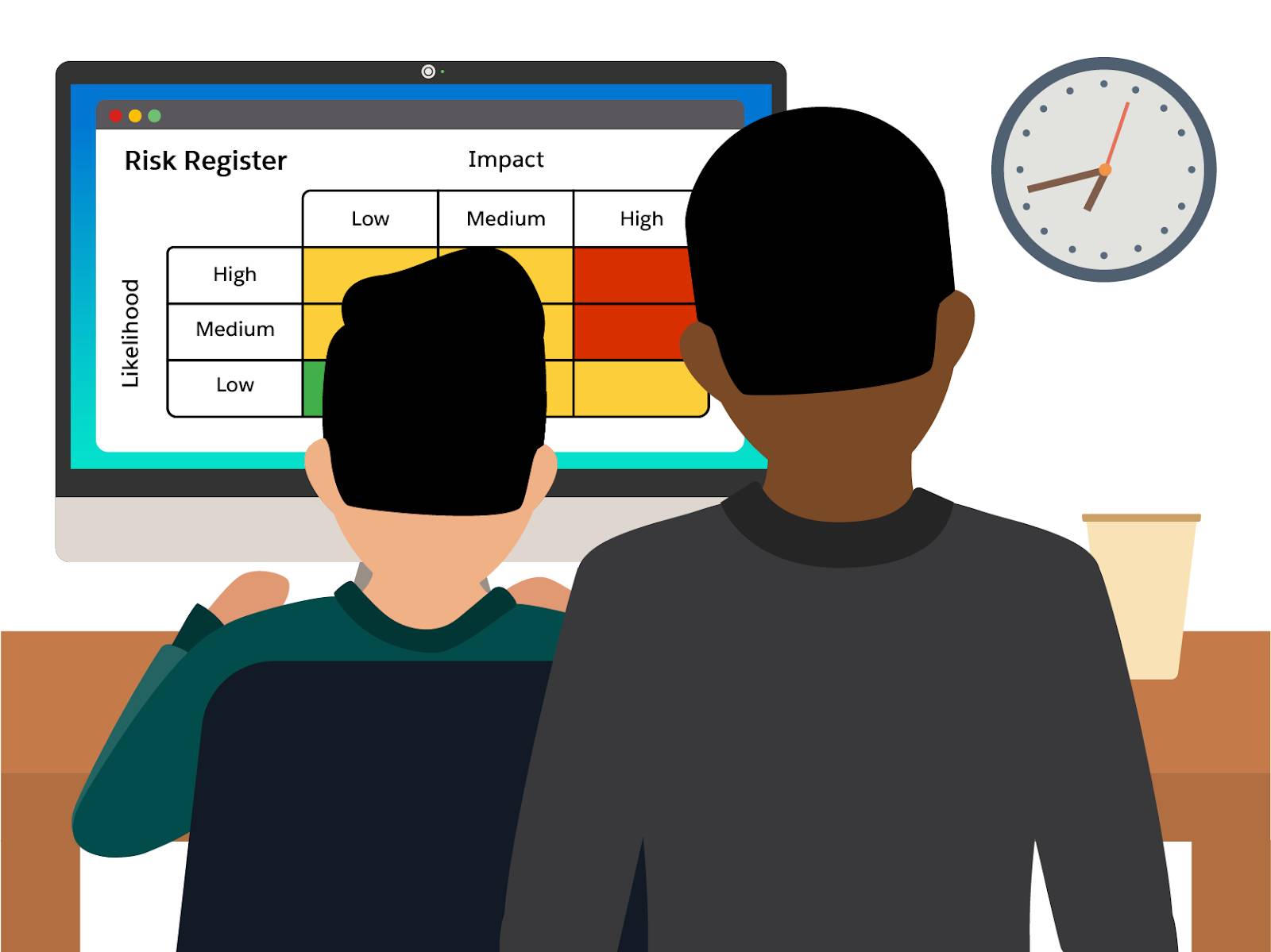
You also monitor and evaluate the effectiveness of the enterprise's cybersecurity safeguards to ensure they provide the intended level of protection, and if needed, you implement new controls. Just as your organization monitors compliance, operational, financial, and reputational risks, you also need to measure, monitor, and manage cyber risks. Risks are best acknowledged and mitigated by using tools that capture and display the likelihood of occurrence and the impact (also known as a risk register).
Using a risk register allows you to track and visualize risk to better communicate with your organization’s senior leadership. It serves as a central repository for the organization's risk information and allows for the information that results from the risk management process to be sorted, standardized, and merged for relevance to the appropriate level of management. You can then use this information to report on program effectiveness to internal and external stakeholders.
Manage Risk During an Incident
Cyberincidents are bound to occur within your organization. Whether you’re building a new response process or making improvements to your existing program, your security team needs to establish a resilient and scalable incident response plan (IRP). IRPs empower you to contain the scope of an incident while reducing the risk to your organization and IT assets. This allows you to return to normal operations as quickly as possible.
An IRP provides a step-by-step approach on how to respond to a variety of incidents and includes escalation requirements and procedures when warranted. As the cyber executive leader, you work with your incident response lead to set up an IRP that’s capable of identifying and detecting malicious and suspicious events across various levels of criticality.
During incident response, it’s important that you capture and effectively manage your organization's risk. Doing so provides insight into the root causes of your risks, and ensures that incidents are dealt with promptly and effectively. Let’s take a closer look.
Capture Key Incident Information
To help you better capture risk that results from an incident, you should gather all the pertinent details in an incident reporting or ticketing system. This system should be accessible across the organization so that anyone can report a suspected cyberincident or event.
Link Incidents to Risk
Your organization likely has a team responsible for incident response through incident recovery. However, merely resolving an incident doesn’t prevent it from recurring. You need to identify the root cause to find out why it occurred. Answering questions such as, “Was the incident a result of an internal or external threat?” or “Did the incident occur due to a system failure or business disruption?” allows you to categorize the incident for easy reporting or aggregation of similar incidents.
Once you’ve identified the cause, you can relate the incident to one or more specific organizational risks. This paints the picture of where within your organization risk is realized, and allows you to then strengthen mitigations.
Strengthen Risk Mitigations and Reporting
You’ve captured key incident information, identified the root cause, and linked this information to your organization's risk. Now you need to strengthen security controls to help mitigate the risk. You look to see if there’s something missing in a process or technology, or if there’s lack of specialized expertise. Identifying this information and possible solutions reduces the likelihood of future incidents occurring.
Finally, you should put in place a process for reporting about the incident, risk, mitigation, and any changes in technology, processes, and policies moving forward. This helps your organization spot and share trend information with key stakeholders for determining how vulnerable the organization is to a specific risk (risk exposure) and for strengthening your cybersecurity posture moving forward.
Meet Jamie and Matheo
Let's see this process in action. Jamie is the chief information security officer (CISO) at an independent wealth management firm. In this role, he partners with various senior managers throughout the organization. One of his direct reports is Matheo, a director of security operations and incident response. Matheo works with the firm's security operations center (SOC) to manage insider threat risks.
Recently, Matheo has been alerted that an employee within the firm has been sending privileged and confidential financial data to a personal email account using their corporate email. Matheo’s team has shared with him the incident report about the risks involved. After reviewing the initial report and subsequent updates throughout the response process, Matheo combs through the firm's incident reporting tool to look for any other instances with this employee or others where they’ve used email to send out this type of information.
Noticing no discernible pattern, Matheo checks the firm's risk register for any risk associated with theft of information by using the firm's digital resources. While an IT risk does exist, the firm considers this risk to have a low likelihood and low impact—but Matheo decides that this risk needs reevaluation.
In Matheo’s weekly check-in with Jamie, he brings up the risk resulting from the incident, noting that this is an organizational-wide risk that could have dire consequences. Jamie works with Matheo to investigate further and identify the cost and benefit of possible mitigations. Jamie then presents their findings to the firm’s chief risk officer (CRO) and CEO, and recommends that they implement technical controls to prevent employees from sending confidential data to their personal email. Jamie explains how administering these controls will limit potential financial and reputational harm, and he gains buy-in from the CRO and CEO to spend funds and staff time implementing the controls. As a result, the firm is better positioned to mitigate future risks related to this incident.
Sum It Up
In this module, you’ve been introduced to how to inform risk decisions with cost-benefit analysis, and how to monitor risks using a risk register. You’ve also learned your role in mitigating risks during an incident from an executive’s perspective.
Along with the information you’ve reviewed in the Executive Cyber Leadership module, you should now have a better understanding of what it takes to be an executive cyber leader. Interested in learning more about cybersecurity careers? Head on over to the Cybersecurity Learning Hub to explore other roles and hear from real security practitioners.
Resources
- External Site: Global Cyber Alliance: What to Do in Case of a Data Breach
- External Site: Fortinet: Incident Response