Use AWS Services to Stay Compliant
Learning Objectives
After completing this unit, you’ll be able to:
- Explain how to use AWS compliance services.
- Explain the features of AWS Artifact.
- Describe AWS Penetration Testing.
Depending on your industry, there may be certain guidelines or policies that you’re required to follow in order to remain compliant with industry-wide standards. Let’s follow a few scenarios to explain how AWS compliance services work.
Scenario #1
You work at AnyCompany Health, a healthcare provider. You use AWS to maintain millions of member health records and are required to comply with the Health Insurance Portability and Accountability Act of 1996 (HIPAA) and the Health Information Technology for Economic and Clinical Health Act (HITECH).
Scenario #2
Your friend works at AnyCompany Payments, the insurance side of the company that specializes in processing payment transactions. They’re also required to comply with the Payment Card Industry Data Security Standard (PCI DSS). They want to learn more about the latest reports of AWS compliance with PCI DSS.
In both of the above scenarios, there are industry-specific guidelines that need to be followed. Your company might require guidelines related to data protection, or follow a set of norms and procedures in order to reduce potential security threats.
In this unit, you learn about two different actions that can help you maintain compliance on AWS.
- Accessing compliance reports through AWS Artifact
- Conducting penetration tests on your AWS environment
AWS Artifact

AWS Artifact is a free service that provides on-demand access to AWS’s security and compliance reports and select online agreements.
There are two main sections of Artifact.
- AWS Artifact Agreements
- AWS Artifact Reports
AWS Artifact Agreements
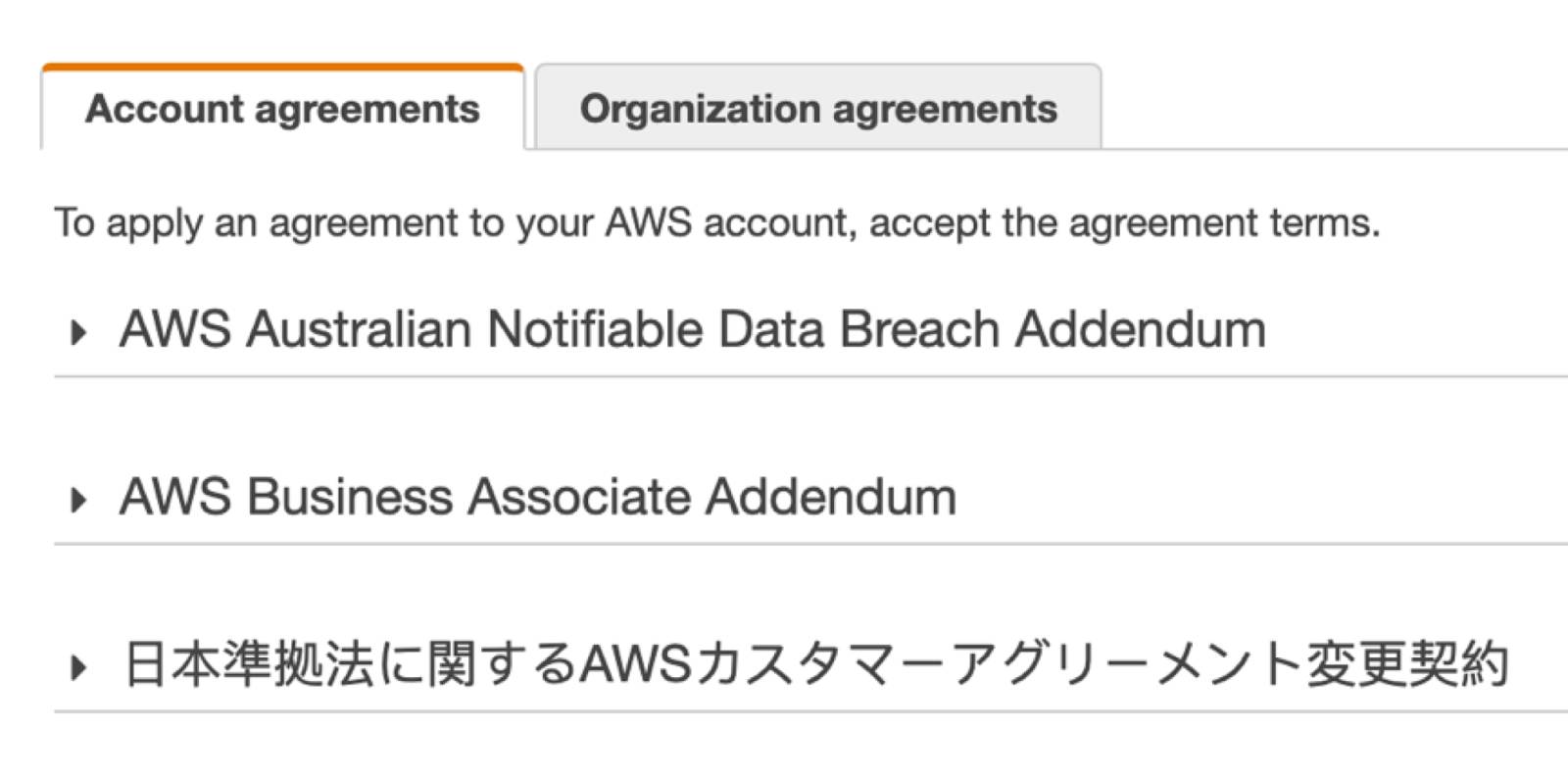
AWS Artifact Agreements allows you to review, accept, and manage agreements between you and AWS, for either an individual account or for accounts that are part of an AWS Organization. AWS Artifact Agreements contains different types of agreements to address the needs of customers who are subject to specific regulations.
In Scenario #1, you use AWS Artifact Agreements to access documents related to HIPAA compliance. Before accepting any agreement terms, you make sure to review them with AnyCompany Health’s legal, privacy, and/or compliance teams. You also use IAM to grant access to the agreement stakeholders (such as members of the legal, privacy, and/or compliance teams) so that they can download, review, and accept agreements.
AWS Artifact Reports
In Scenario #2, your friend navigates to AWS Artifact Reports to understand AnyCompany Payments’s responsibility for complying with the requirements outlined in the PCI DSS regulatory standard. Each report includes the reporting period for which the document is valid. For example, in the screenshot below, the PCI DSS report is valid from 12/13/2019 to 12/12/2020.
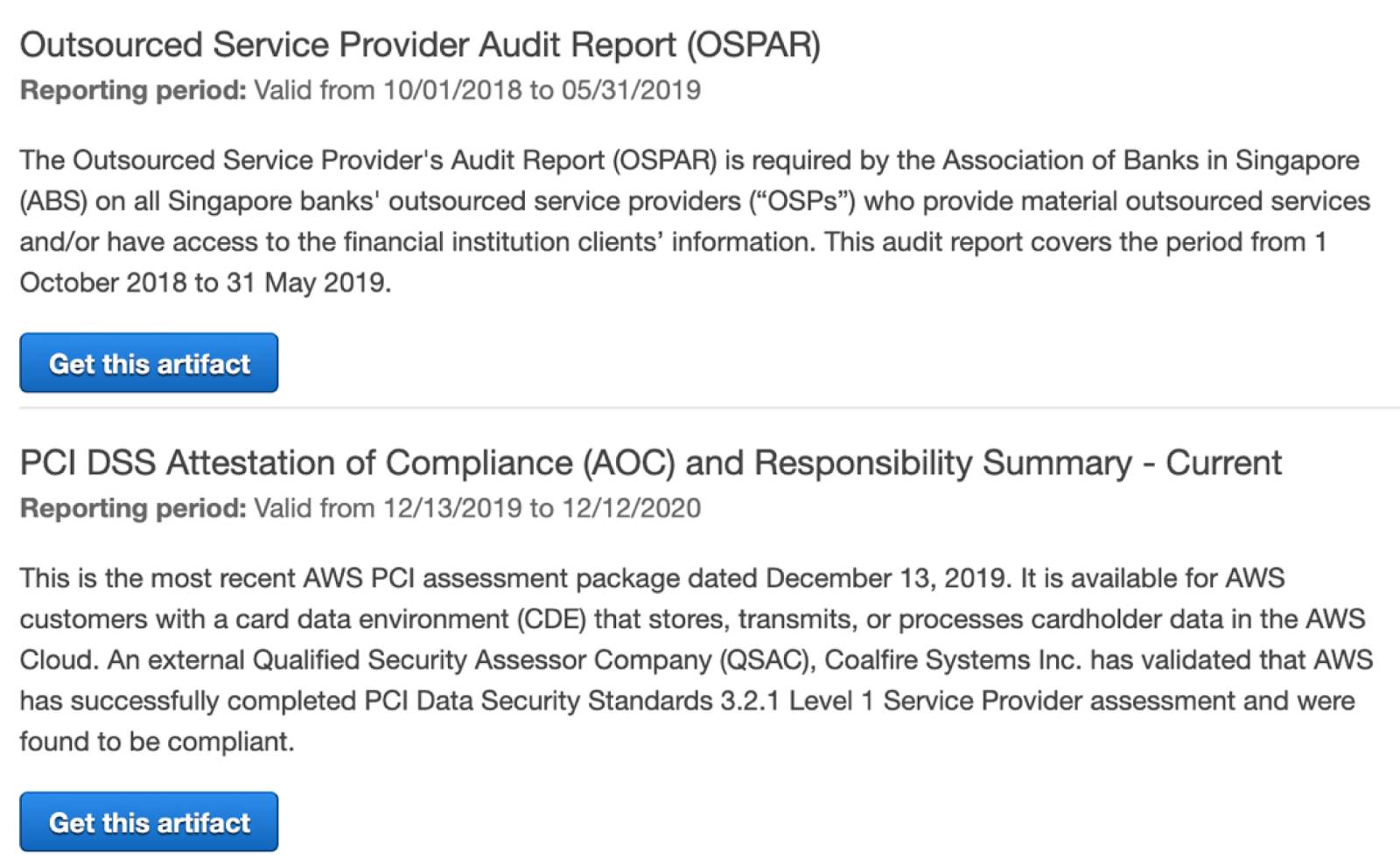
AWS Artifact Reports provides several compliance reports from third-party auditors who have tested and verified AWS’s compliance with a variety of global, regional, and industry-specific security standards and regulations.
AWS Artifact Reports remains up to date with the latest reports as they are released. You can provide the AWS audit artifacts to your auditors or regulators as evidence of AWS security controls. In addition, you can use the responsibility guidance provided by some of the AWS audit artifacts to securely design your cloud architecture.
Conduct Penetration Testing on AWS

Penetration testing is the process of checking a system or application for vulnerabilities by attempting to exploit them. Some common vulnerabilities that can be discovered through penetration testing include security misconfigurations, weak permission settings, and sensitive data exposure. This is often a recommended or required part of compliance standards.
In Scenario #2 for payment management, your friend refers to the PCI DSS documentation for guidance on penetration testing requirements. They find details such as the penetration testing components, methodologies, reporting guidelines, and qualifications of a penetration tester.
AWS customers can conduct penetration testing against their AWS infrastructure for the following services and resources.
- Amazon Elastic Compute Cloud (EC2) instances, NAT Gateways, and Elastic Load Balancers
- Amazon Relational Database Service (RDS)
- Amazon CloudFront
- Amazon Aurora
- Amazon API Gateways
- AWS Lambda and Lambda Edge functions
- Amazon Lightsail resources
- Amazon Elastic Beanstalk environments
Any vulnerabilities or other issues that are the direct result of AWS’s tools or services must be conveyed to AWS Security within 24 hours of completion of testing.
When conducting penetration tests for the purposes of compliance, make sure that your tests do not violate AWS’s policy regarding the use of security assessment tools and services.
Stay Compliant and Secure with AWS Artifact and Penetration Testing
AWS provides many resources to help your company remain compliant with internal and external security guidelines. Use AWS Artifact and penetration testing to ensure that your AWS-implemented controls are operating effectively and that you have designed your cloud architecture securely.
In the next module, you learn about AWS pricing and support.