Balance Integrity and Trust in Security Decisions
Learning Objectives
After completing this unit, you’ll be able to:
- Explain the role of integrity in secure decision-making.
- Identify industry-specific security controls.
In today’s digital age, ensuring the accuracy of information is vital for maintaining customer trust and business effectiveness. In this unit, we explore how leaders, specifically in the financial, manufacturing, and healthcare sectors, can use security controls to embed integrity and trust into their organizational frameworks. But before delving into industry-specific priorities, let’s recap key concepts from the previous unit.
Knowledge Check
Ready to review what you’ve learned? The following knowledge check isn’t scored—it’s just an easy way to quiz yourself. To get started let’s review what you’ve learned by matching each security control category to the applicable business owner’s statement. When you finish matching all the items, click Submit to check your work. If you’d like to start over, click Reset.
Apply Integrity and Trust
The CIA triad–Confidentiality, integrity, and availability–is a cornerstone of cybersecurity. Each security objective guides the protection of information.
- Confidentiality refers to protecting information from unauthorized access.
- Integrity refers to ensuring information remains complete, trustworthy and unaltered.
- Availability refers to ensuring information is accessible to authorized users when needed.
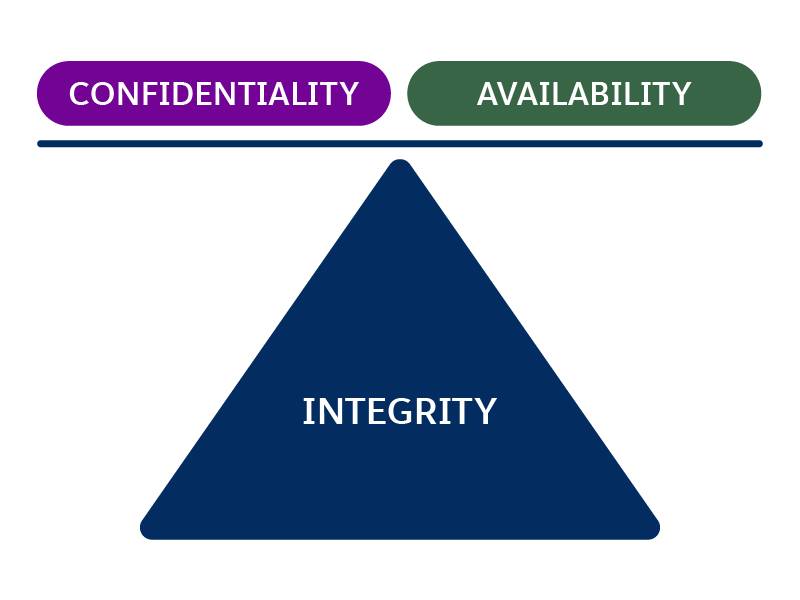
Among these, integrity is the objective that actively safeguards the accuracy, consistency, and trustworthiness of information. Without integrity, information might not be reliable, even if it’s confidential and available. Therefore, integrity is fundamental for building trust and enhancing stakeholders’ confidence in digital systems.
Trust includes transparency, accountability, fairness, privacy, safety, and security. The World Economic Forum’s Digital Trust Framework, described in Digital Trust in the Software Development Lifecycle, offers guidelines to help businesses embed trust into their digital operations emphasizing that trust goes beyond just the technologies used. It's also about the decisions that leaders make.
We began the previous unit with scenarios of leaders whose decisions were undermined, compromised, and delayed due to corrupted information and information systems. Leaders can proactively mitigate this risk by using security controls as integral components in the design of their information systems and decision-making processes, enabling informed and confident choices that benefit the entire organization.For example, strict access controls prevent unauthorized modifications to sensitive information, protecting personal and confidential data, and ensuring compliance with legal standards. Encryption plays a crucial role as well, safeguarding information in storage and during transmission. These measures accomplish several objectives.
-
Upholds the integrity of data by protecting it from unauthorized and accidental tampering
-
Builds trustworthiness by ensuring the data remains reliable and secure under all circumstances
-
Empowers leaders with reliable information, enabling them to make strategic decisions confidently and responsibly
In this way, security controls are protective mechanisms and meaningful tools that create an environment where risk-informed decisions and trust are foundational to the organizational framework. This is especially important for organizations that are targeted because they possess valuable assets, sensitive data, and critical infrastructure that can be exploited for financial gain, competitive advantage, or disruption. Let’s look more closely at examples of those industries that may serve as high-risk targets.
Industry-Specific Priorities
In the table are three sectors–financial, manufacturing, healthcare–with their descriptions, top vulnerabilities, and corresponding control categories with explanations.
Sector |
Sample Companies |
Top Vulnerabilities |
Top Three Control Categories |
|---|---|---|---|
|
Financial Sector This sector includes institutions and companies that provide financial services to individuals, businesses, and governments. |
|
|
|
|
Manufacturing Sector This sector includes companies involved in the production of physical goods, transforming raw materials or components into finished products. |
|
|
|
|
Healthcare Sector This sector includes organizations that provide medical services, manufacture medical equipment or drugs, and offer health insurance. |
|
|
|
In this module, we’ve explored the costs of cyber defense, the role of security controls, and the strategic prioritization of these controls. With this knowledge, you can protect your organization’s information assets effectively.
By enabling the proactive identification and mitigation of risks, a well-designed cybersecurity program can save a company significant financial losses and legal liabilities. It’s a proactive approach that protects the company’s bottom line while instilling confidence and trust in stakeholders and customers. Remember, prioritizing security in your business design and decision-making is not an expense: It’s a data informed strategic investment that delivers tangible value in the short- and long-term.
Resources
- External Site: CISA: Financial Services Sector
- Trailhead: Digital Trust in the Software Development Lifecycle
- External Site: NIST: Cybersecurity Resources for Manufacturers
- External Site: CISA: Healthcare and Public Health Cybersecurity
- External Site: EC-Council University: Which Industries Are the Most Vulnerable to Cyberattacks?