Prevent Credential Exposure in Code
Learning Objectives
After completing this unit, you’ll be able to:
- Identify why secrets exposure may be a problem at your organization.
- Explain how to prevent accidental secrets exposure.
Credential Exposure
One of the most common breaches of data security comes from sensitive data stored in the code you develop. Because of this, you need to learn how to protect this data (including credentials, encryption keys, and more), which could allow attackers to compromise your organization’s sensitive data if it fell into the wrong hands.
If you're a developer, you’re responsible for code and scripts that access technology stacks such as the cloud, applications, and other tools. All these instances typically require credentials, and it is vital that you protect those credentials from exposure.
Many development groups who are working on cyclical development set stretch goal dates and there is often pressure to work at speed. Developers may use GitHub or other open-source code repositories as a means to collaborate with each other and complete projects.
The risk of credential exposure arises in code repositories because sometimes busy developers hard code credentials into their code as a shortcut. Then, once the code goes public, the organization’s credentials become available in the public domain. Once you commit and push code, it can't easily be deleted. And even if your version control system allows you to delete the commit of the compromised code, another developer or service may have already pulled a copy of the compromised code prior to the deletion.
This means that anyone who knows how to work with version control or has made a copy of the code can pull up these credentials, even from the past, and gain access to them. Without applying secure coding conventions and practices, developers may accidentally reveal credentials to unauthorized individuals, enabling them to access core systems.
It’s an easy and common mistake that developers make when they’re rushing to get their new feature out to customers. This means that you must be even more vigilant about making sure you never include credentials in code.
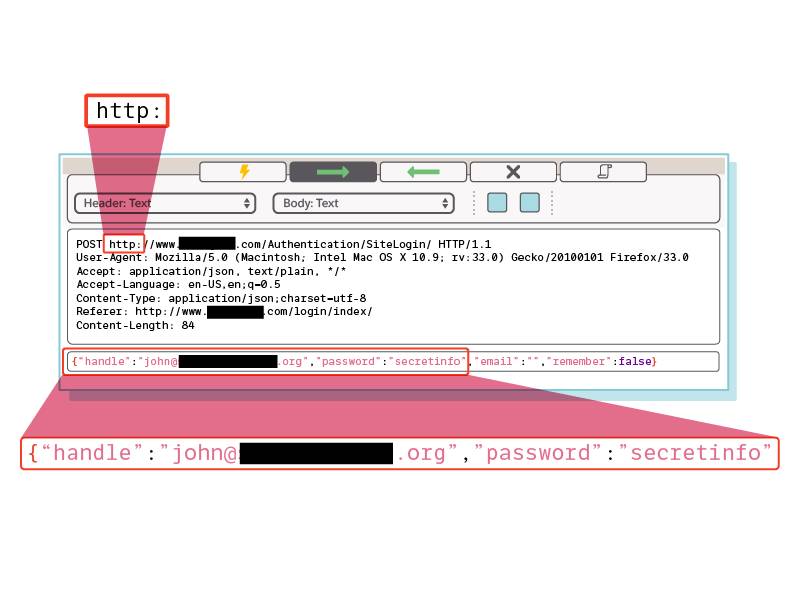
Leaked Credentials
Software tracking services like GitHub, Bitbucket, and SourceForge have been working for years to mitigate the problem of leaked credentials. Some of these services even alert the user if they push an access token to a public repository, and revoke those tokens so they can’t be used to perform any unauthorized actions. Despite this, it’s still common for repositories to mistakenly include application programming interface (API) tokens and keys.
Your organization is likely aware of this problem. And your security team should check at a regular cadence for User IDs, API keys, access tokens, database files, and other keys accidentally exposed in code in public repositories or cloud instances.
How You Can Prevent Credential Exposure
Just as it's best practice to integrate the secure development lifecycle into your development process, it's also best practice to institute credential management hygiene into every step of your coding processes. Remember two important points in order to keep your code safe from credential exposure.
- Store secrets only in your organization’s approved secrets management service.
- Never include secrets in your code.
In the following modules of the Implement Secrets Management at Your Organization trail which include Public Key Infrastructure and Encryption and Key Management, we cover best practices to help you manage the keys that protect your secrets, as well as how to protect those secrets in transmission and at rest.
Sum It Up
In this module, you’ve been introduced to methods for creating and protecting strong passwords, as well as the benefits of password managers. You’ve also learned about how to implement the principle of least privilege when performing privileged access management, and about the importance of monitoring your users and accounts over time.
Along with the information you reviewed in the Organizational Secrets module, you should now have a better understanding of what it takes to protect your organization’s secrets, including its access credentials. In the next module, Public Key Infrastructure and Encryption, we cover methods for protecting your data in transit and at rest. You can learn more about best practices in cybersecurity and hear from real security practitioners by visiting the Cybersecurity Learning Hub on Trailhead.