Learn How Web Application Firewalls Protect APIs
Learning Objectives
After completing this unit, you’ll be able to:
- Identify how web application firewalls (WAFs) deliver application programming interface (API) protection.
- List how WAFs help organizations meet compliance rules.
- Define how advanced WAF capabilities can help your organization protect data from modern threats.
- Describe how to choose a WAF product.
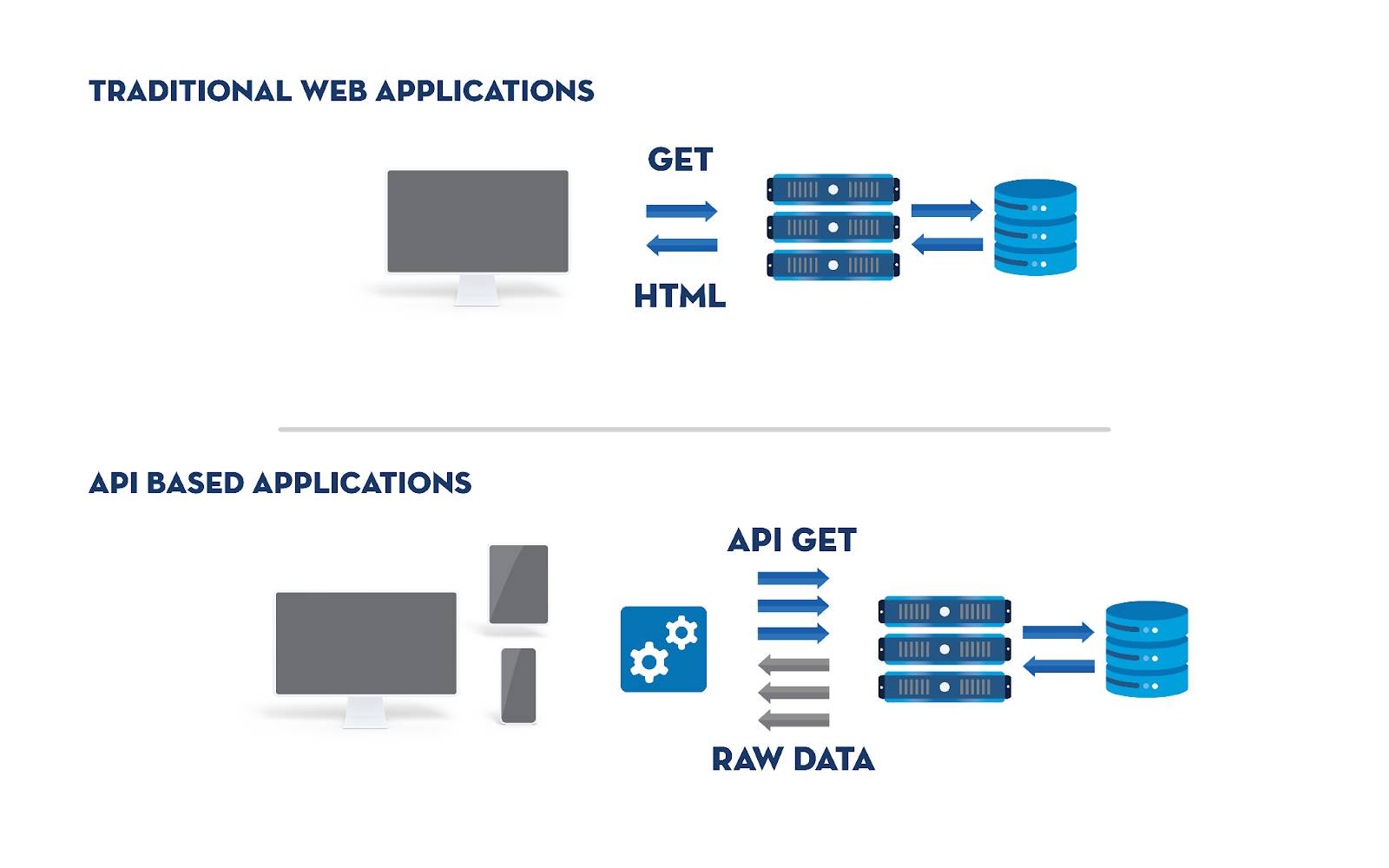
How WAFs Deliver API Protection
The days of basic websites serving up simple Hypertext Markup Language (HTML) pages have passed. Traffic has become more sophisticated. Web applications today deliver mission-critical services using APIs that provide richer, more responsive experiences by letting the client process raw data instead of just rendering simple HTML.
These API tools also support the mobile applications that users in the community need to access. When the client has access to a large amount of application data, the impact of an attacker exploiting the API's rules when a WAF isn't in place can be significant. These tools require a WAF to ensure they are protected from OWASP Top 10 threats. WAFs can protect against file inclusion vulnerabilities and others seeking to take advantage of internet traffic, a server plugin, or other vulnerabilities.
WAFs for Compliance
Making the data that web applications rely on available to the application often comes with compliance obligations. WAFs help organizations meet compliance rules as well. Regardless of your service provider, compliance needs to be your primary priority.
Payment Card Industry Data Security Standard (PCI DSS), for example, defines a set of application security standards that organizations handling credit cards must comply with. PCI 6.6 specifically will often come up when discussing web application firewall technologies designed to keep traffic and assets secure. The standard requires inspection of traffic to web applications that interact with card data. To comply with the standard, organizations have two options.
- Web application code reviews (which can slow down deployments)
- Deploying WAFs between the client and the web application.
In a world where organizations are expected to frequently and rapidly deploy code changes as they adopt software development and IT operations (DevOps) methodologies, a robust WAF will often be a better solution for meeting these types of compliance rules while protecting the organization from OWASP Top 10 threats.
Advanced Capabilities of Web Application Firewalls
Let’s take a look at some advanced WAF capabilities, such as machine learning, for delivering both accurate detection and reduced management overhead.
Machine Learning
Traditional web application learning techniques require manual tuning and are prone to false positives. Tuning applications every time there is a change and remediating false positives drives up administrative overhead for teams and others in the organization's community that may already be overburdened.
WAFs can use machine learning to update their protection model automatically as the web application evolves. This means application security teams and others in the IT department spend less time manually tuning the web application firewalls according to traffic and creating exceptions based on false positives.
Advanced Reporting
WAFs can provide organizations full visibility into event details. They can generate attack logs that include the critical information that security operations center (SOC) analysts need, such as the Hypertext Transfer Protocol (HTTP) body information, and clear indications on why security rules require an application request to be blocked.
Choosing a WAF Product
In choosing a WAF product, organizations should look for one that includes the following capabilities.
- Backed by threat intelligence
- OWASP Top 10 protection
- API WAF management
- Bot mitigation
- DDoS protection
- File protection
- Information leak prevention
- Cross site request forgery (CSRF) protection
- Web socket security
- API security
You should also consider the infrastructure used to deliver the WAF, whether it can be easily integrated with your sandbox and other security solutions, whether it includes a content delivery network (CDN), and whether its attack logs can be easily exported to your external Security Information and Event Management (SIEM) tool.
Knowledge Check
Ready to review what you’ve learned? The following knowledge check isn’t scored—it’s just an easy way to quiz yourself. To get started, drag the description in the left column next to the matching term on the right. When you finish matching all the items, click Submit to check your work. If you’d like to start over, click Reset.
Sum It Up
In this module, you’ve been introduced to WAFS, and learned why they are an effective security strategy for business success. You’ve also learned about advanced capabilities of WAFs, and the importance of having a WAF solution that also provides its own API for managing the WAF itself. You now have the knowledge you need to implement WAFs at your organization.
Interested in learning more about cybersecurity roles and hearing from security professionals? Check out the Cybersecurity Career Path on Trailhead.
Resources
External Site: Fortinet: What Is WAF? Web Application Firewall Explained
