Get to Know Incident Response
Learning Objectives
After completing this unit, you’ll be able to:
- Define incident response terms.
- List incident response phases.
- Describe the goals, tasks, and constraints of incident response.
- Explain the benefits of incident response.
Incident Response Glossary
As an incident responder, you are a cyber first-responder, responsible for providing a rapid response to reported IT security threats, incidents, or cyberattacks. Let’s take a look at some terminology before we dig deeper.
Term |
Definition |
|---|---|
Chain of Custody |
A process that tracks evidence through its collection, safeguarding, and analysis lifecycle by documenting each person who handled it, and the date/time it was collected or transferred |
Containment/Triage |
The process of limiting the damage from an incident and preventing any further damage from happening |
Event |
Any observable occurrence in an IT network or system |
Incident |
A violation or imminent threat of violation of computer security policies, acceptable use policies, or standard security practices |
Incident Response/Handling |
The mitigation of violations of security policies and recommended practices |
Indicator of Compromise (IOC) |
A sign that an incident may have occurred or may be currently occurring |
Jump Kit |
A portable physical case that contains materials that the responder may need during an investigation |
Malware |
A virus, worm, Trojan horse, or other code-based malicious entity that is designed to infect a host |
Ransomware |
A type of malware that encrypts or locks files and demands payment to access them |
Risk |
The potential level of impact on organizational operations, organizational assets, or individuals that is posed by a threat |
Risk Appetite |
The level of risk that an organization is prepared to accept before it deems action is necessary to reduce the risk |
Threat |
The potential source of an adverse event |
Incident Response Phases
The National Institute of Standards and Technology (NIST) describes four phases of incident response.
- Preparation
- Detection and Analysis
- Containment, Eradication, and Recovery
- Post-Incident Activity
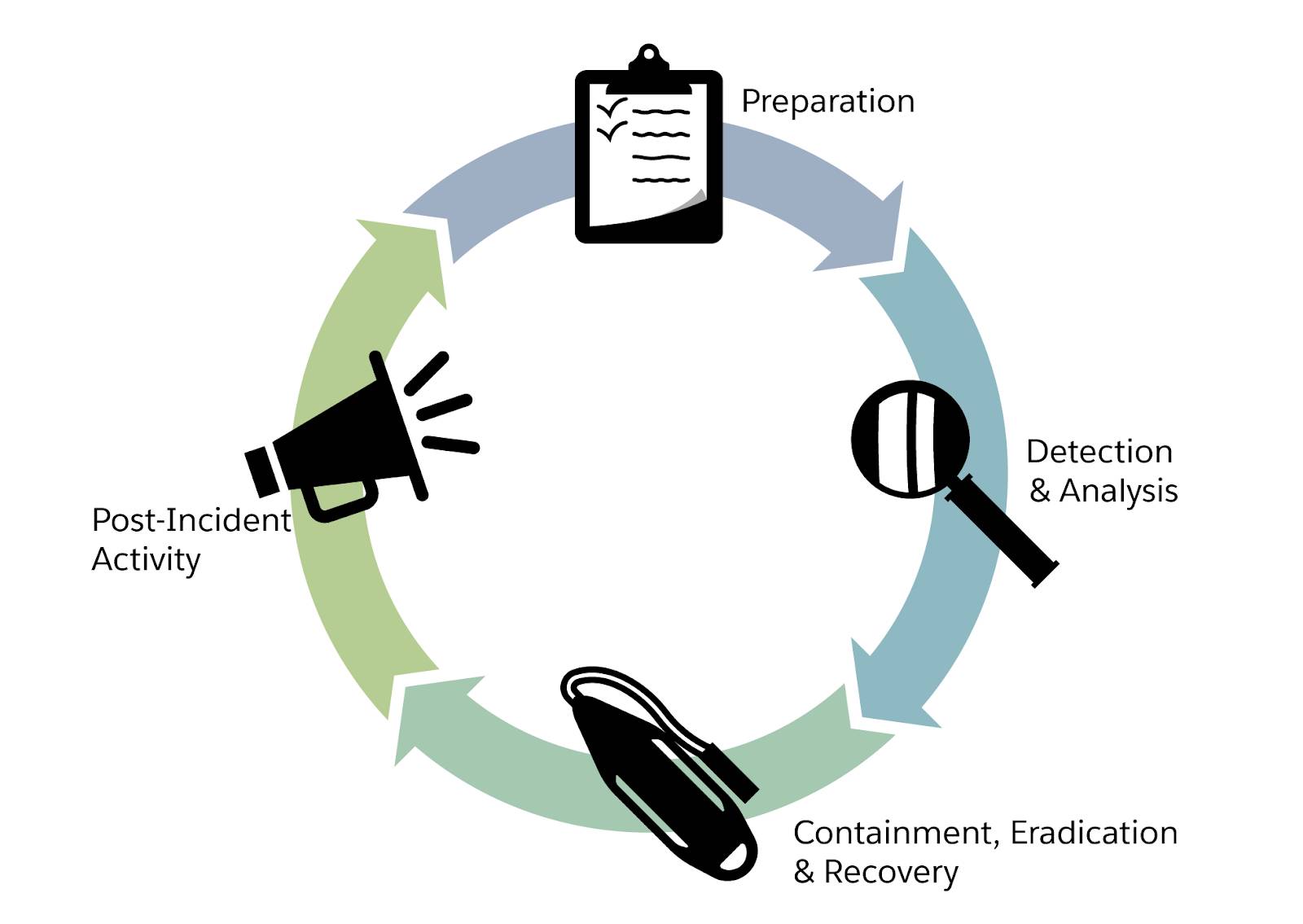
Phase |
Tasks |
|---|---|
Preparation |
Establish an incident response capability so that the organization is ready to respond to incidents. This includes the development and maintenance of policies, procedures, plans, playbooks, metrics, and other governing documentation. Practical preparation may also include the execution of tabletop exercises (TTX). |
Detection and Analysis |
Monitor IT systems to detect deviations from normal operations and see if they represent actual security incidents. When an incident is discovered, collect additional evidence and establish its type and severity. |
Containment, Eradication, and Recovery |
Isolate the network segment or computer system that is under attack; investigate and remove malware from all affected systems; identify the root cause of the attack; and take action to prevent similar attacks in the future, ensuring any compromised assets, accounts, or systems have been remediated. |
Post-Incident Activity |
Perform a retrospective of the incident. Prepare complete documentation of the incident, investigate the incident further, and understand what was done to contain it. The Post-Incident Activity should feed continuous improvement and inform the Preparation phase. |
Goals, Tasks, and Constraints of Incident Response
Goals of Incident Response
As an incident responder, you’re responsible for enabling an organization to quickly detect and respond to attacks. You minimize the damage of an attack by limiting the success of the attacker, mitigating the impact, and resolving incidents to reduce downtime to the business. By doing so, you lower costs associated with an incident and save time after a security breach. Incident response also helps organizations prevent recurrence of attacks.
Incident Response Tasks
Incident response helps organizations identify a suspected cybersecurity incident by monitoring evidence of unusual occurrences and assessing possible trigger points. For example, an organization could receive an alert that a user who usually logs in from the United States is now logging in from Mexico and downloading an unusual amount of files. This unusual activity triggers an alert, which an analyst in the organization’s security operations center investigates. The analyst determines that the alert may represent malicious activity and investigates further to determine whether or not a legitimate user is using the IT asset to access the data.
Establishing the objectives of any investigation and cleanup operations through incident response can help organizations quickly analyze all available information related to a potential cybersecurity incident, and determine what has actually happened. Incident response can help identify what systems have had their confidentiality, integrity, or availability compromised.
Incident responders also work out how the incident happened. For example, how did the attacker gain entry to the system? Did they send a phishing email, use brute force to guess a credential, or access the system from another internal system? Incident responders also determine the potential business impact of the cybersecurity incident and conduct a detailed investigation, using computer forensic capabilities.
Constraints of Incident Response
When conducting incident response, you may face some of the following constraints.
Constraint |
Example |
|---|---|
Available Data |
There may not be enough data to attribute the attack to a specific perpetrator. In addition, the data may be encrypted or otherwise unavailable. The availability of the data also depends on how much an organization logs its IT assets. |
Finding the Needle in the Haystack |
As an incident responder, you have to search for little things that don't always stand out. A good hacker leaves little to no breadcrumbs to follow. You may need to comb through copious logs to find one small anomaly. |
Available Tools |
You often have to use specialized tools for more in-depth analysis. Depending on what tools are available to you at your organization, your task may be more difficult. |
Human Error |
As an incident responder, you also depend a lot on the person who initially observed the potential incident to rely on their memory, which may not always be reliable. As incident response is a defensive position, responders have to be right 100% of the time, while an attacker can opportunistically wait for an organization to make even the slightest mistake. |
Time |
When an incident occurs, it’s important to act with urgency in a timely manner to protect your business operations and related digital assets. |
Benefits of Having an Incident Response Plan
There are several benefits to having an incident response plan. Let’s dig into a few.
Christoph is an incident responder at a government organization. He’s worked with the IRT to develop an incident response plan with clear post-incident instructions, assignment of responsibilities, and incident response management guidelines.
Improve Response to Incidents
Having a plan in place enables Christoph to respond consistently and confidently when incidents arise. He follows the instructions and knows who to involve and what steps to take.
Mitigate Damage After an Incident
Christoph knows that having a sound plan helps him quickly understand the nature of an attack, how to investigate particular indicators of compromise, and what is at risk. With their incident response plan in hand, the security team can prioritize response actions. They take concrete and appropriate steps for mitigation and remediation, thereby reducing the impact of the incident on their organization.
Proactively Improve Cybersecurity
Christoph uses an incident response plan to identify appropriate stakeholders, understand notification requirements, and follow a defined continuous feedback loop to ensure lessons learned from one incident drive meaningful change. Proactively planning for an incident also enables him to follow a systematic methodology when responding.
Maintain Customer and Public Trust
Christoph knows that a cyber incident at his organization can cause damage to relations with his partners, customers, and regulators. If the organization fails to communicate promptly with those impacted by the incident, it is likely that the organization will lose customer trust, and may even face legal or financial penalties. Christoph follows the communications process within the incident response plan to interface promptly and effectively with customers and stakeholders during crises, and to quickly recover compromised data.
Reduce Downtime
The objective of an incident response plan is to minimize the number of systems affected by a breach and the amount of time attackers have access to a corporate network. Christoph uses his incident response plan to reduce downtime following an incident. The faster his organization can detect and respond to a data breach or even security incidents, the less likely it will have a significant impact on its data, customer trust, reputation, and a potential loss in revenue. He creates detailed action plans for multiple possible situations. This ensures that if an incident does occur, he’s able to quickly get systems back online and minimize the impact to his organization's operations. This directly reduces the risk posed by such incidents, because the vulnerability is quickly patched, and the threat actors are blocked.
Remain in Compliance
As an employee at a government organization, Christoph ensures that he complies with relevant local, state, and federal laws and regulations governing incident response and breach notifications to impacted parties. In the incident response plan, he details relevant reporting requirements and timelines, and he ensures his team knows who needs to be notified of what.
Sum It Up
Now you understand more about incident response terms, phases, and goals. In the next unit, you learn more about the responsibilities of an incident responder and discover the skills that help incident responders succeed.
Resources
- External Site: NIST: Risk
- External Site: Fortinet: Incident Response
- PDF: National Institute of Standards and Technology (NIST): Incident Response Recommendations and Considerations for Cybersecurity Risk Management
