Build Your Foundation
Learning Objectives
After completing this unit, you’ll be able to:
- Discuss risk management as the foundation of cybersecurity.
- Identify valuable risk management certifications.
Cybersecurity and Risk Management
Cybersecurity is the practice of protecting digital systems, networks, and data from digital attacks, damage, or unauthorized access, through the effective management of risk. In today’s interconnected world, the proliferation of cybersecurity risks poses a significant threat to individuals, organizations, infrastructure, governments, cities, and beyond. By dedicating themselves to this profession, cybersecurity experts play a crucial role in safeguarding systems and networks, thereby protecting people, organizations, and vital aspects of society. The impact of their work is far-reaching, as it creates a secure foundation for individuals to navigate the digital landscape and allows organizations to operate with confidence. In addition to technical expertise, cybersecurity professionals require strong business skills to effectively communicate and collaborate across teams, understand organizational objectives, and make strategic decisions in alignment with business goals. These skills are used to identify potential threats and vulnerabilities, implement appropriate security measures to counter risks, and continuously monitor and update security measures.
Risk management is a powerful force that empowers individuals and organizations to navigate uncertainty and achieve remarkable success. It goes beyond fear and avoidance, inviting us to embrace the unknown with courage and resilience. By understanding and anticipating potential risks, we can turn obstacles into stepping stones and transform adversity into opportunity. Risk management is a gateway to growth and innovation, where calculated risks become strategic advantages. Cybersecurity and risk management are essentially one in the same.
The following scenario demonstrates cybersecurity in action.
Meet John. He has just purchased his dream house, nestled on a hilltop overlooking a serene lake. The house holds many of his cherished belongings. John knows the house’s location and value could attract unwanted attention from burglars. Thinking about the potential threats, he decides to take measures to protect his house, balancing the risk of a potential burglary against the cost and potential inconvenience of certain security measures.
John begins by assessing the vulnerabilities of his house. He walks around the property and notices various points of entry—the front and back doors, several ground floor windows, and a balcony door upstairs. First, John decides to invest in high-quality smart locks for all doors. They are sturdy, offer a high level of protection, and are within his budget. He decides that the cost is reasonable, considering the reduced risk of a potential break-in. He also considers installing a smart home alarm system that would allow him to monitor his home via his smartphone, tablet, or personal computer. He knows that it would provide a higher level of security, but it would be costly. After weighing the pros and cons and considering the many options available, he chooses to install the smart home alarm system.
Next, John considers getting a dog to help him guard his properties. But he quickly realizes that this would be a huge monetary and time expense and might even disturb his peaceful home environment, so he decides against it. Lastly, John considers motion sensor lights. The lights can illuminate any person who moves close to the house, deterring potential burglars and alerting John or his neighbors to unexpected movement. He decides to install the lights.
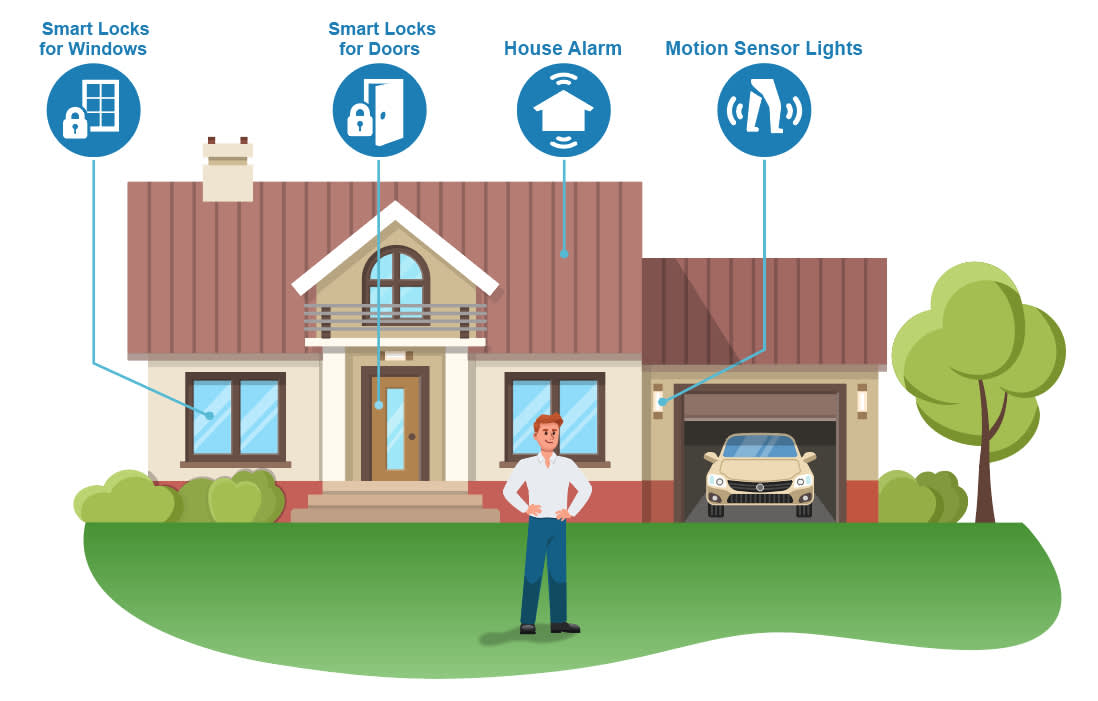
After implementing these security measures, John doesn’t just forget about them. He frequently updates the smart alarm and smart locks and tests the sensitivity of the motion sensor lights. He is also always on the lookout for any new threat or vulnerability, ready to revise his home security setup.
This story of John’s house is an illustration of risk management’s role in cybersecurity. Just like John, cybersecurity professionals must assess the vulnerabilities of a system, implement security measures, balance the risk versus cost, and keep updating their defense mechanisms and safeguards as new threats emerge.
Cybersecurity doesn’t aim for absolute security, which is often unrealistic and cost-prohibitive, but instead aims to manage and reduce the risk to a level that the organization deems acceptable. This acceptable risk level is determined by considering various factors such as the potential consequences of a security breach, the cost of implementing security measures, the operational impact these measures would cause, and the organization’s overall risk tolerance.
The Risk Management Framework
Risk management plays a pivotal role in shaping cybersecurity processes and decisions.
It is a structured approach to identifying, assessing, and prioritizing risks followed by the coordinated deployment of resources to minimize, monitor, and control the probability or impact of adverse events. As businesses address increasing cybersecurity threats, risk management efforts aid in shielding against the following risks:
-
Financial risk involves potential monetary losses due to fines or cost of incident recovery.
-
Operational risk involves disruption to business operations due to failed internal processes, systems, people, or external events.
-
Reputational risk involves potential loss of revenue or customers, or decreased investor trust.
-
Regulatory risk involves the potential for legal penalties, fines, or sanctions due to noncompliance with laws and regulations.
Cybersecurity reduces financial risks by reducing likelihood of breaches that can lead to theft. It mitigates operational risks by protecting systems against unauthorized access and enabling efficient recovery, which reduces disruptions. It reduces reputational risks by demonstrating a strong commitment to cybersecurity, which helps maintain customer trust and public confidence. Finally, by ensuring compliance with data protection laws, cybersecurity diminishes regulatory risks.
With cybersecurity intricately woven into all business risks, structured risk management becomes crucial. Here, frameworks and methodologies such as the National Institute of Standards and Technology (NIST) Risk Management Framework (RMF) and the Center for Internet Security Risk Assessment Method (CIS RAM) prove invaluable. These tools guide cybersecurity professionals through activities such as preparing the organization, categorizing systems and information, selecting and implementing controls, assessing their effectiveness, authorizing the system, and continuously monitoring risks.
Understanding risk management is crucial across all cybersecurity roles. Technical professionals need to identify vulnerabilities and implement safeguards, while nontechnical roles often shape risk management policies and orchestrate responses to risks.
Risk management training and certifications
Let’s explore several areas that help develop the knowledge, skills, and experience necessary to effectively assess, mitigate, and manage cybersecurity risks.
Activity |
Description |
|---|---|
|
Informal and formal education
|
|
|
Professional certifications
|
|
|
Training and workshops
|
|
|
Hands-on experience
|
|
|
Collaboration and networking
|
|
By combining these practical approaches, individuals can develop a well-rounded skill set in cybersecurity risk management and enhance their ability to assess, mitigate, and manage risks effectively in any cybersecurity role.
Practice
Let’s review a practical exercise to apply your understanding of cybersecurity certifications and risk management.
Activity Description: In this exercise, your task is to conduct a risk assessment for a hypothetical organization and recommend appropriate cybersecurity certifications to enhance the organization’s risk management capabilities.
- Select one to three distinct functions within your hypothetical organization. For example:
-
Information Systems Management function: They look after the organization’s technology such as computers, networks, and databases.
-
Data Privacy Compliance function: They ensure the organization follows laws and rules about handling people’s personal data.
-
Incident Response function: They handle security problems, finding and fixing them, and make plans to deal with future issues.
- For each function, research and propose relevant cybersecurity certifications that can bolster the understanding and management of cybersecurity risks. Consider the alignment of these certifications with the roles and responsibilities of each function and their contribution to the organization’s overall risk posture.
- Using the NIST RMF, the CIS RAM, or another risk assessment tool as a guideline, carry out a simplified risk assessment for a hypothetical system within each function to identify potential vulnerabilities and suggest appropriate mitigation strategies. Sample hypothetical systems include:
- A customer relationship management (CRM) system that manages the organization’s interactions with potential and current customers.
- A data loss prevention (DLP) system that prevents potential data breaches by monitoring, detecting, and blocking sensitive data while in use, in motion, and at rest.
- A security information and event management (SIEM) system that provides real-time analysis of security alerts generated by applications and network hardware.
- Evaluate how the proposed certifications can enhance each function’s capability to identify, assess, mitigate, and monitor the risks outlined in your assessment.
Skills Used: Risk assessment, critical thinking, understanding of security controls, understanding of cybersecurity certifications, familiarity with risk management frameworks/methodologies, written communication, strategic alignment of certifications with risk management objectives
In this unit, we’ve discussed how a comprehensive understanding of risk management is essential in every cybersecurity role, and how certifications can help enhance this understanding. We’ve proposed a practical exercise to help you apply this knowledge in a hypothetical scenario. In the next unit, we will turn our attention to further developing your cybersecurity skill set.
Resources
-
Trailhead: Cybersecurity Risk Management
-
Trailhead: Learn the Skills of a Cybersecurity Risk Manager
-
Trailhead: The Center for Internet Security’s Risk Assessment Method
-
Trailhead: The Emerging Future of Cybersecurity
-
External Site: NIST: NIST Risk Management Framework
-
External Site: World Economic Forum: Innovation-Driven Cyber-Risk to Customer Data in Financial Services
-
External Site: Fortinet: What Is Cybersecurity Management?
-
External Site: NIST: NIST IR 8286: Integrating Cybersecurity and Enterprise Risk Management (ERM)