Protect the AWS Root User
Learning Objectives
After completing this unit, you will be able to:
- Describe the AWS root user.
- Follow AWS best practices when creating an AWS account.
In the previous unit, you created an AWS account and learned the differences between authentication and authorization. This unit discusses the first actions you need to take before creating any resources for your cat photo application or working with any additional AWS services.
What Is the AWS Root User?
When you first create an AWS account, you begin with a single sign-in identity that has complete access to all AWS services and resources in the account. This identity is called the AWS root user and is accessed by signing in with the email address and password that you used to create the account.
Understand the AWS Root User Credentials
The AWS root user has two sets of credentials associated with it. One set of credentials is the email address and password used to create the account. This allows you to access the AWS Management Console. The second set of credentials is called access keys, which allow you to make programmatic requests from the AWS Command Line Interface (AWS CLI) or AWS API.
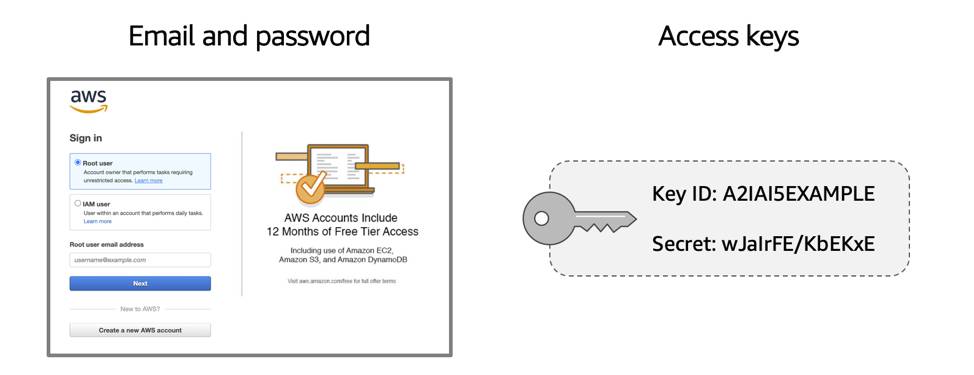
Access keys consist of two parts:
- An access key ID, for example, A2lAl5EXAMPLE
- A secret access key, for example, wJalrFE/KbEKxE
Similar to a username and password combination, you need both the access key ID and secret access key to authenticate your requests via the AWS CLI or AWS API. Access keys should be managed with the same security as an email address and password.
Follow Best Practices When Working with the AWS Root User
Keep in mind that the root user has complete access to all AWS services and resources in your account, as well as your billing and personal information. Due to this, securely lock away the credentials associated with the root user and do not use the root user for everyday tasks.

To ensure the safety of the root user:
- Choose a strong password for the root user.
- Never share your root user password or access keys with anyone.
- Disable or delete the access keys associated with the root user.
- Do not use the root user for administrative tasks or everyday tasks.
When is it OK to use the AWS root user? There are some tasks where it makes sense to use the AWS root user. Check out the Resources to read about them.
Delete Your Keys to Stay Safe
If you don't already have an access key for your AWS account root user, don't create one unless you absolutely need to. If you do have an access key for your AWS account root user and want to delete the keys:
- Go to the My Security Credentials page in the AWS Management Console and sign in with the root user’s email address and password.
- Open the Access keys section.
- Under Actions, click Delete.
- Click Yes.
Wrap Up
The AWS root user is a powerful tool, but because of its far reach, it can be dangerous if it gets in the hands of a bad actor. To prevent security exploitation of your AWS account (and eventually, your cat photo application), it is important that you lock down the root user.
In the next unit, you learn how to further secure the AWS root user with MFA.