Explore the NICE Framework
Learning Objectives
After completing this unit, you’ll be able to:
- Discuss the National Initiative for Cybersecurity Education (NICE) Workforce Framework for Cybersecurity.
- Explain the NICE Framework’s global influence.
- List ways the NICE Framework can be used by various groups.
Discover the NICE Framework
As organizations increase their reliance on information technology, network connections, and digital applications to achieve their goals, the need for skilled professionals who can manage and secure digital systems continues to grow. To help meet this need, resources like the NICE Workforce Framework for Cybersecurity (NICE Framework) have emerged, offering a common approach to identifying the knowledge and skills required for different cybersecurity work roles.
For example, Wyatt, a self-taught cybersecurity enthusiast, was unsure about which path to pursue within cybersecurity. Similarly, Sarah, an employer at a community college, needed to fill a critical role on her IT team. Both found solutions through the NICE Framework: Wyatt matched his skills and interests with the Digital Evidence Analysis work role, while Sarah identified the need for a Network Operations professional to manage the growing IT demands at her organization.
The framework provided them with clear direction—Wyatt in finding his career path and Sarah in recruiting and selecting the right talent for the community college.
Overview of the NICE Workforce Framework for Cybersecurity
The NICE Workforce Framework for Cybersecurity (NICE Framework) is an international resource from the National Institute of Standards and Technology (NIST) that standardizes cybersecurity knowledge and skill to help any industry build a strong cybersecurity workforce. It’s an advisory document that can be used to inform an organization’s recruitment, hiring, and training, and it supports career discovery, education, and development. In addition, the NICE Framework outlines how organizations can flexibly apply defined Work Roles or even create their own work roles to meet unique needs and contexts.
At the heart of the NICE Framework are detailed Task, Knowledge, and Skill (TKS) statements for each Work Role. These statements clearly define cybersecurity work for defined roles. The framework’s flexibility allows a candidate’s knowledge and skills to be applied across different job functions.
Keep in mind that the work roles listed in the NICE Framework are not synonymous with job titles or occupations. They’re broad descriptions of responsibilities that can include different job titles across various organizations. For example, in a restaurant, the “food preparation” work role requires knowledge of food safety and skill in preparing meals. Depending on the business, this work role could be listed in a job description for a pastry chef, sous chef, or even an executive chef. Additionally, a single job can be responsible for one or more work roles.
NICE Framework Work Role Categories
The NICE Framework organizes cybersecurity work into seven high-level categories. In the table, the categories are grouped based on whether the work roles are primarily technical or nontechnical as described in the Trailhead module A Career in Cybersecurity.
-
Nontechnical work roles focus on administrative and operational tasks that set and maintain the organization’s cybersecurity direction, such as developing policy and conducting security awareness training.
-
Technical work roles focus on using software and digital systems to implement the policies and practices set by those in nontechnical roles, such as configuring a firewall to only allow specific types of traffic.
Keep in mind, although categorized as nontechnical or technical, knowledge and skills for any specific work role will likely require a combination of technical and nontechnical knowledge and skills.
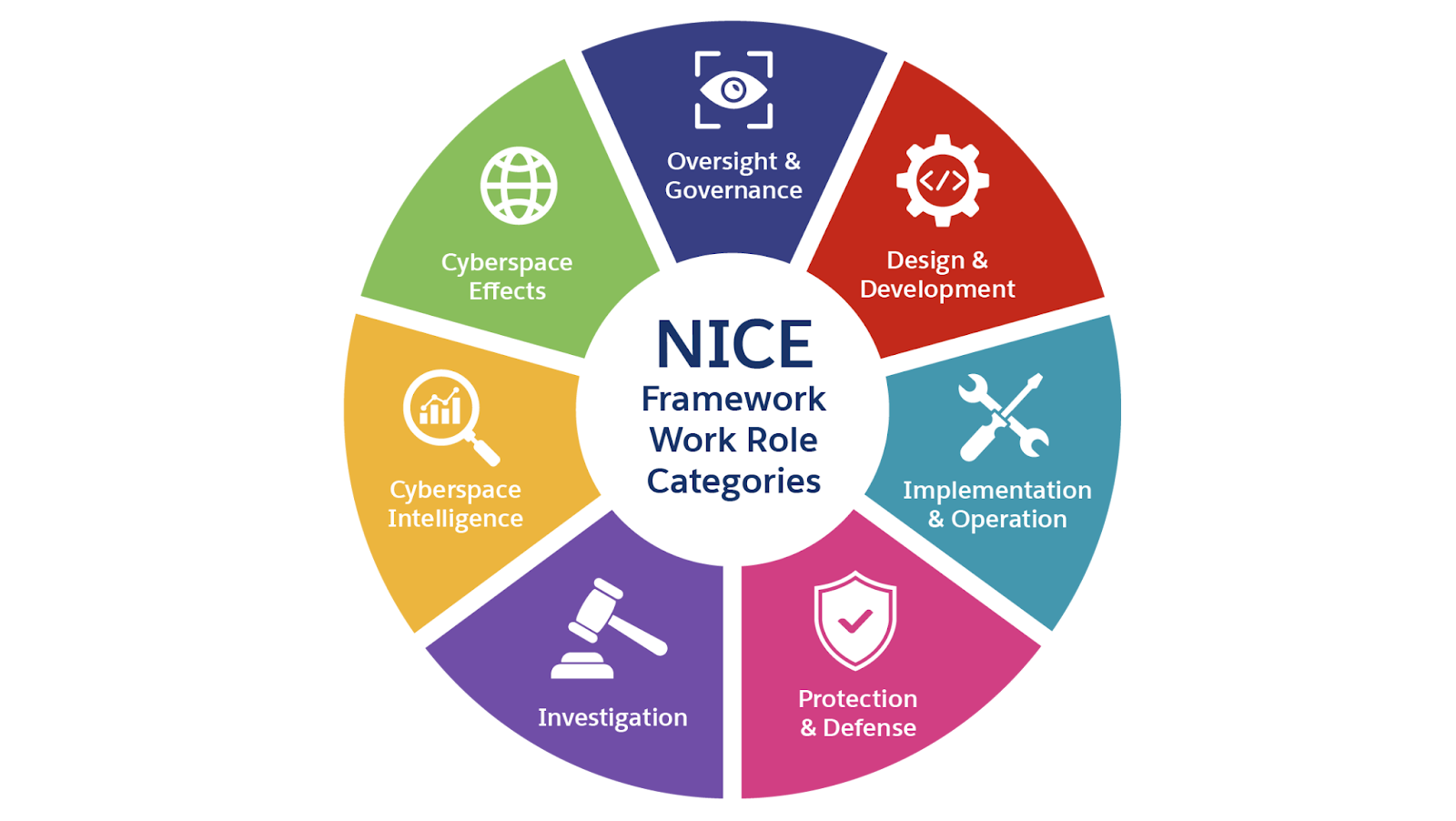
Work Role Category |
Primarily Technical or Nontechnical |
Sample Work Roles |
|---|---|---|
Oversight and Governance (OG) |
Nontechnical |
Cybersecurity Policy and Planning Cybersecurity Curriculum Development Secure Project Management |
Design and Development (DD) |
Technical |
Secure Software Development Systems Testing and Evaluation Technology Research and Development |
Implementation and Operation (IO) |
Technical |
Network Operations Knowledge Management Data Analysis |
Protection and Defense (PD) |
Technical |
Insider Threat Analysis Vulnerability Analysis Digital Forensics |
Investigation (IN) |
Technical |
Cybercrime Investigation Digital Evidence Analysis |
Cyberspace Intelligence (CI) |
Non-Technical |
Multi-Disciplined Language Analysis Cyber Intelligence Planning All-Source Analysis |
Cyberspace Effects (CE) |
Technical |
Cyber Operations Planning Exploitation Analysis Partner Integration Planning |
Again, while work roles can be categorized as nontechnical or technical, the knowledge and skills required for any specific work role often span both domains. Every role within a category exists on a continuum, blending technical and nontechnical expertise to varying degrees depending on responsibilities and context. For example, the Secure Project Management work role requires technical skill in configuring systems and nontechnical skill in performing administrative planning activities.
Also, while the NICE Framework doesn't specifically list workplace/soft skills within the work roles, it does acknowledge the importance of workplace skills in cybersecurity work roles. Explore the specific tasks, knowledge, and skills outlined in the NICE Framework to fully understand the scope of a given work role.
Adapt the NICE Framework
The research and best practices that inform the NICE Framework have given it far-reaching influence. Other national and international organizations have adapted its principles and content to create frameworks tailored to their specific needs. These frameworks, while drawing inspiration from the NICE Framework, offer unique contributions to the global cyber profession. Review some key examples included in the following table.
Framework |
Unique Perspectives |
|---|---|
Includes work roles related to data science and artificial intelligence (AI), like data steward and AI risk and ethics specialist, reflecting the growing importance of AI in defense. |
|
Lists business skills as “key skills” in several cybersecurity profiles. For example, key skills for a chief information security officer (CISO) include the ability to influence, lead, communicate, cooperate, and collaborate. |
|
Maps cybersecurity skills to the proficiency level required to perform in a specific role. For example, an Incident Responder at Level 1 (Novice), “Can explain the basic principles of incident management, investigation and response” while at Level 6 (Practitioner) is “experienced in handling major cybersecurity incidents…” |
|
Singapore’s Operational Technology Cybersecurity Competency Framework (OTCCF) |
Specifically created to attract and develop cybersecurity talent in Singapore’s Operational Technology (OT) sector. Occupations include: OT cybersecurity maintenance specialist, OT threat analyst, and OT penetration tester. |
Includes unique work roles like cybersecurity human capital manager and red team specialist. |
Build a Cohesive Cybersecurity Workforce
The NICE Framework is a valuable resource for many groups within the cybersecurity field. When different groups use the NICE Framework, it creates a cohesive process to build knowledge and skills across the industry. Here are examples of how each of the groups below can contribute to a unified approach.

-
Educators and training providers can use the task, knowledge, and skill (TKS) statements to create curricula and training aligned with work roles.
-
Aspiring cybersecurity professionals can use the framework to explore and select a desired work role, assess their knowledge and skills, then plan their training and education to close any gaps.
-
Employers can use the TKS statements to upskill and reskill existing employees and to develop job descriptions that lead to more effective recruitment and selection.
-
Current cybersecurity professionals can use the framework to create updated career development plans that inform their competitive skill set enabling them to advance in their careers.
By using the NICE Framework, these groups work together to contribute to a capable and adaptable national cybersecurity workforce capable of addressing current and future cybersecurity challenges.
Sum It Up
In this unit, we explored the NICE Framework, examining its purpose, structure, global influence, and ways it supports various cybersecurity professionals and organizations. We also discussed how the updated task, knowledge, and skill statements reflect the latest cybersecurity needs, with task statements specifically highlighting what candidates do on the job.
In the next unit, we explore how the NICE Framework’s task-oriented approach can be applied to create proficiency-based projects and training. These types of projects align with the growing trend of skills-based hiring, helping cybersecurity professionals and employers obtain the practical experience needed to meet real work requirements.