Identify Threats
Learning Objectives
After completing this unit, you’ll be able to:
- Describe how to determine possible threats to your organization's most critical assets.
- Explain the intelligence lifecycle.
- Explain how information-sharing groups and information exchanges can assist in keeping up with emerging trends.
Determine Threats to Critical Assets
As a threat intelligence analyst you provide various services to meet the needs of customers. You support the organization’s cyber risk management process, helping determine threats to critical assets, and providing context to help the organization understand the distance between its desired security level and the actual level. You take into account system characterization, threat identification, vulnerability identification, and other factors. These factors help you form a picture of cybersecurity risk. The basic equation for risk is simple: If an adversary or threat can exploit a vulnerability to harm an asset, then you have risk.
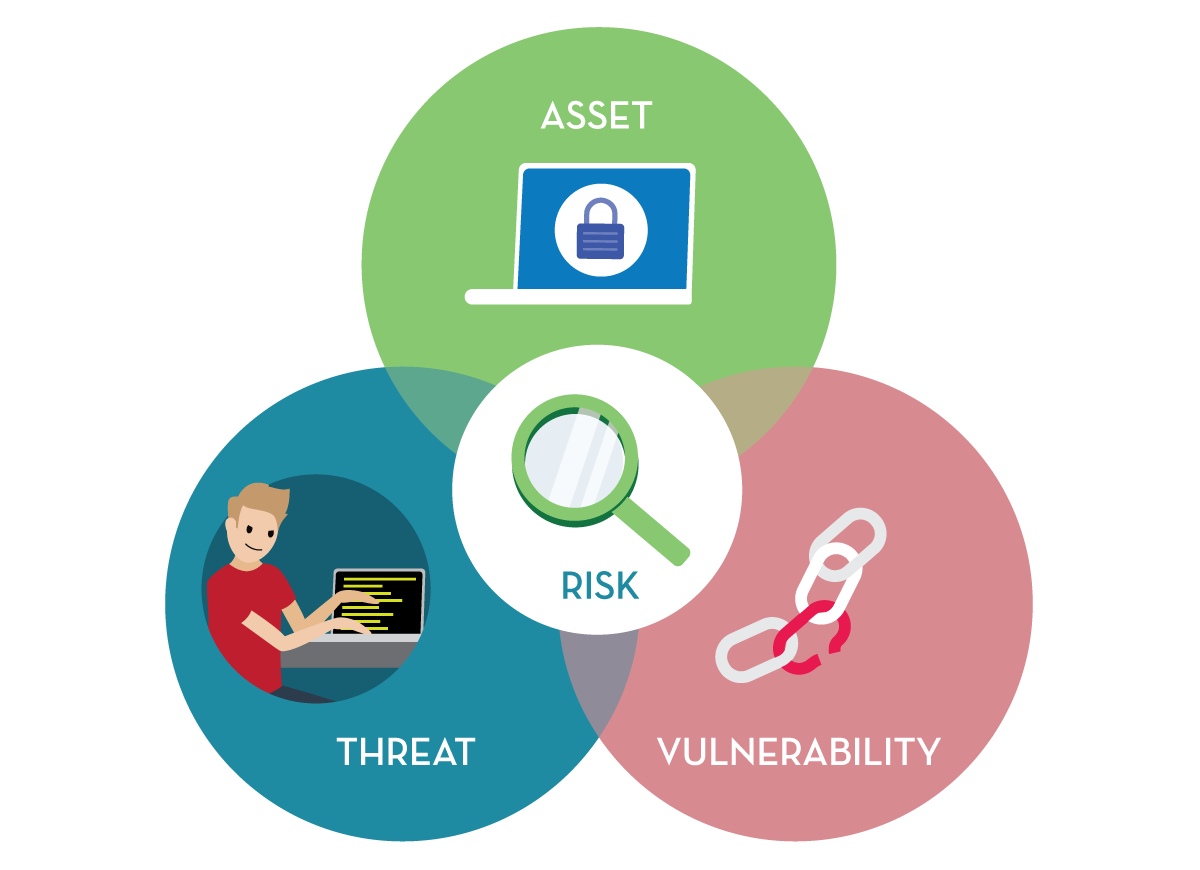
In determining threats to critical assets, as a threat intelligence analyst, you follow what is called the intelligence lifecycle. Let’s take a closer look.
What Is the Intelligence Lifecycle?
The intelligence lifecycle is a process first developed by the U.S. Central Intelligence Agency (CIA) that follows six steps: direction, collection, processing, analysis and production, dissemination, and feedback. This iterative and adaptable process, through which raw data becomes finished intelligence, is fundamental to the success of a threat intelligence program. Let’s take a look at what each piece of this lifecycle entails.
-
Direction: Defining the objectives of why we need this particular intelligence and identifying the essential elements of information that need to be included.
-
Collection: Gathering data from multiple internal and external sources, including human intelligence, electronic sources, and publicly available sources.
-
Processing: Structuring data from disparate sources and integrating it into existing technology solutions.
-
Analysis and Production: Using human and technical tools, such as machine learning, to connect the dots and create assessments and reports that summarize the data for decision makers.
-
Dissemination: Delivering information through reports and presentations, and tailoring the message to the audience.
-
Feedback: Following up with stakeholders to ensure the information they received let them take action and gather further information to produce more accurate, relevant, and timely assessments based on the success of previous intelligence.
Now that you understand more about the steps you as a threat intelligence analyst follow to produce intelligence, let’s next look at one of the primary tools in your arsenal against adversaries: threat modeling.
Threat Modeling
Meet Danielle. Danielle Goode takes on many technical roles for Thoughtful Software Corporation, a software company located in Tampa, FL. One of her roles is to use threat modeling to identify threat vectors and types of security threats. While many defenders wait behind their firewalls for attackers, Danielle knows that effective organizations model the threats to their network and gather intelligence on possible adversaries proactively.
Danielle works to identify types of threat actors and their motives. A threat actor is the person behind the event. Danielle knows threat actors can include terrorists who aim to disrupt systems, cybercriminals who aim to steal customer data for financial gain, insiders who are performing espionage for a competing company, advanced persistent threats (APT) sponsored by rival nation states, or hacktivists seeking to disrupt services they don’t agree with.
Once Danielle identifies potential actors, she next identifies the actions they may take, seeking to better understand the tactics an adversary may use to compromise an asset. For example:
-
Malware: Installing malicious software, ransomware, or backdoors on a system.
-
Exploit: Hacking a server or perpetrating a denial of service attack to prevent legitimate users from being able to use a website or application.
-
Social engineering: Influencing behavior by exploiting natural human response to fear of loss, desire for gain, or wanting to help. Common tactics include phishing to steal credentials, spear phishing to install malware, and voice, text, and email impersonation to perpetrate fraud, steal data, and take over accounts.
-
Misuse: Misuse is when a person uses a computer system, account, or data in the wrong way or for the wrong purpose. Examples include privilege abuse by insiders, account takeovers impersonating a privileged user, and privilege escalation by a non-privileged user.
-
User error: A user error is an error made by the human user of a system in interacting with it. This usually includes loss of a device or data, misdelivery, and misconfiguration.
Next, Danielle considers threat vectors, or the method by which the threat source will impact the target. She looks at possible entry points, such as a USB flash drive used to deliver malware, a network firewall that’s not properly configured, allowing an adversary to hack a server, or weaknesses in policies or procedures, such as a failure to prevent users from reusing passwords across accounts.
Danielle also takes into account potential human errors, such as sending an email containing sensitive data to the wrong customer. She considers whether technical controls are in place to mitigate these errors, such as a data loss prevention tool. This tool would flag the email to the sender as possibly containing sensitive information that should not be shared.
Armed with an in-depth understanding of potential threat actors, actions, and vectors, Danielle lastly considers how these security threats manifest themselves in specific ways to Thoughtful Software Corporation’s core business activity. She knows that each IT system is unique. She considers both threats that are common to all organizations with public-facing web portals and threats that are specific to her company.
Danielle knows being proactive about threat modeling enables her to help Thoughtful Software Corporation develop strategies to minimize its exposure to potential threats. Knowing who the potential threat actors are, what actions the organization can take, and the vectors it can use provides the organization with ways to thwart and intercept these actors before they cause serious harm.
Share Threat Intelligence
As Thoughtful Software Corporation works to better identify and take action against threats, Danielle remembers the old saying, “There is strength in numbers.” She knows this applies to her job as a threat intelligence analyst as well. Whatever threats her company is facing, it is likely that others in her industry are facing similar ones. For this reason, Danielle recommends to her boss that the company join information-sharing groups to keep up with emerging threats.
Danielle knows that Thoughtful Software Corporation cannot see all malicious activity. She understands that her company can learn something from its peers. Being part of a threat community can particularly help her detect low-frequency attacks, such as a threat posed by an APT working for a rival nation state seeking to steal company financial information from several software companies in the US.
Examples of information exchanges Danielle can tap into include:
- The Cyber Security Information Sharing Partnership (CISP) in the UK.
- The National Council of Information Sharing and Analysis Centers (ISACs), which provides resources on sector-based information sharing initiatives to maximize information flow across the private sectors and with the government. For example, the IT-ISAC, is a source of security information impacting the IT Sector.
- The National Cyber Forensics Training Alliance (NCFTA), which is a nonprofit partnership between private industry, government, and academia.
-
InfraGard, which is the FBI’s private sector information exchange.
-
OASIS Cyber Threat Intelligence TC, which defines a set of information representations and protocols to address the need to model, analyze, and share cyber threat intelligence.
Sharing threat intelligence helps Danielle tackle cybersecurity challenges by generating connections and ideas. Sharing information enables collaboration and challenges her biases, helping her look at a problem from new angles. Sharing information on a regular basis builds the connections needed to deal with a crisis, before an incident happens. In order to make information sharing most effective, Danielle focuses on relevant information, aligns sharing goals with Thoughtful Software Corporation’s business needs, and tracks useful metrics to improve performance over time.
In the next unit, we'll use intelligence requirements and tactics, techniques, and procedures (TTPs) to investigate adversaries. Let’s go!
Resources
- External Site: Centre for the Protection of National Infrastructure: Identify the Threats
- External Site: National Institute of Standards and Technology (NIST) Guide to Cyber Threat Information Sharing