Explore Admin Tasks for B2C Commerce
Learning Objectives
- List three tasks that a Salesforce B2C Commerce administrator performs.
- Explain the importance of assigning roles in Business Manager.
- List three Business Manager functions an admin uses to manage data and code.
- List three actions an administrator performs using Control Center.
What Does an Admin Do?
Linda Rosenberg is the new B2C Commerce administrator at Cloud Kicks, a company that specializes in high-end custom sneakers. Her job is to make sure that the Cloud Kicks ecommerce site runs smoothly and provides a great online shopping experience. Linda’s also responsible for setting up Cloud Kicks users so they can do their jobs effectively. That’s just as important!
In her first week, Linda’s manager gives her an overview of her general responsibilities as a B2C Commerce admin. Later on, she asks Linda to perform some basic user maintenance tasks.
In her new job, Linda is responsible for:
- Managing roles and permissions for Business Manager users.
- Managing storefront data and code using import/export, jobs, and replication.
- Setting site or global preferences and creating custom preferences.
- Monitoring and controlling B2C Commerce instances.
- Performing standard system backups.
Business Manager is the Salesforce B2C Commerce online tool for configuring and managing B2C Commerce storefronts. A storefront is your online ecommerce site powered by B2C Commerce. A single instance can include multiple storefronts. Another important B2C Commerce tool is Account Manager, which administrators like Linda use to manage B2C Commerce accounts, users, and roles.
Account Manager and Business Manager roles are not the same. Account Manager roles pertain to actions within Account Manager actions, while Business Manager roles pertain to actions within Business Manager.
Users and Roles
At Cloud Kicks, Business Manager users include developers, merchandisers, and administrators. Linda learns that she can assign these users to one or more Business Manager roles. Each role grants a set of permissions. Using predefined roles improves her efficiency and her site’s data security because only users who need to access data to perform their jobs are permitted to do so.
Linda uses Account Manager to create user records and assign users to Account Manager roles. For example, she has the Business Manager Administrator role, which grants her administrator access to Business Manager. Business Manager also has roles ... and permission requirements to access those roles. Here are the permissions that Linda needs.
| Task | User's Module | Roles and Permissions Module |
|---|---|---|
| Manage roles and permissions | ✓ | |
| Assign roles to users | ✓ | ✓ |
Fortunately, Salesforce automatically gives these permissions to the admin role. We talk about roles in a later unit, but it’s worth mentioning here that each new B2C Commerce site comes with a user account named admin. The admin user has a predefined administrator role; this role can’t be deleted. The system makes sure that the admin user retains all access permissions.
Linda is happy to learn that with the administrator role, she can reset any user’s password except the admin user. That’s going to come in handy.
Only B2C Commerce Support can change the admin user password.
Best Practice: We recommend having just one administrator who’s responsible for the passwords of all instances.
Manage Storefront Data and Code
Linda has a lot to get up to speed on in her first week. Data management is a big part of her role. She learns that she can manage data and code using the following Business Manager functions.
- Import/export: Manually triggered or batch processes that move storefront data in and out of the B2C Commerce system.
- Jobs: Scheduled processes that can move and process data and code.
- Read-only price books: High-speed processes that import price books from an external product information management system (PIM).
- Data and code replication: Processes that copy data and code from one instance to another.
- Site import/export: Processes that copy site configuration and setting data from one instance to another, typically to bring a new developer sandbox instance online.
- Catalog feeds: Processes that handle third-party files, such as for Certona.
Certificates
Linda is responsible for managing her site’s client certificates. Client systems use these certificates to make authenticated requests to the B2C Commerce servers for the following types of transactions.
- To upload code to a staging instance using B2C Commerce TLS/SSL certificates that are stored locally.
- For secure third-party system interactions. The site makes secure calls over HTTPS to a web service or third-party system using TLS/SSL certificates that are stored in Business Manager.
- For secure interactions using a SOAP web service that encrypts or decrypts communication. Business Manager stores the certificates for easy expiration management.
During her first week, she learns where Business Manager stores client certificates so she can keep track of them.
Multi-Factor Authentication
As security threats grow increasingly common, Linda knows how important it is to implement strong security measures to protect Cloud Kicks customers and business. Here's what she does.
- Run health checks after every release.
- Stay up to date with required and suggested security functionality.
- Drive company-wide security standards and adoption.
- Protect sensitive customer data.
Linda wants to know more about multi-factor authentication (MFA)—what it is and how she can use it. Multi-factor authentication is where a user is granted access only after successfully presenting two or more pieces of evidence to an authentication mechanism. MFA relies on:
- Something you know, such as login credentials
- Something you have, such as an authenticator app, a bank card, or a Yubikey
- Something you are, such as a fingerprint, eye iris, voice, typing speed, or a pattern in key press intervals.
- Somewhere you are, such as a connection to a specific computing network or using a GPS signal to identify the location.
Two-factor authentication is a type of multi-factor authentication.
B2C Commerce provides enhanced security protection beyond a username and password. It uses MFA to increase protection against threats such as:
- Phishing attacks
- Malicious code injections
- Account takeovers
- Magecart
- Data loss.
Settings, Preferences, and Architecture
Linda learns about configuring settings in B2C Commerce. She can apply settings to one or more sites or across the entire organization. Let’s take a quick look at the B2C Commerce architecture to see what we mean by sites and organizations.
Merchants work within what’s called a realm. Typically, merchants have a single realm that’s just for them. (They can also have multiple realms.) A realm contains instances on which they develop, test, and deploy their online storefronts. A realm includes a primary instance group (PIG) and a secondary instance group (SIG). The B2C Commerce PIG includes staging, development, and production instances, and each of those instances has one or more sites. The sites on a particular instance together are considered an organization.
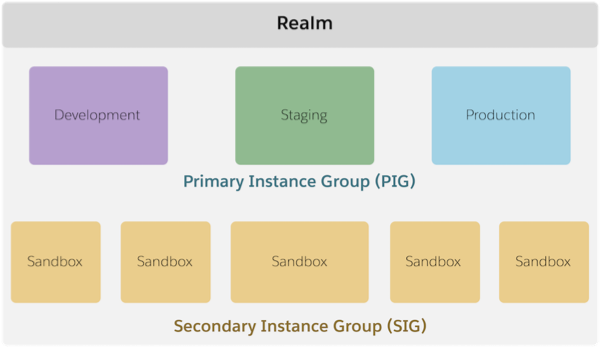
See the Trailhead: Architecture of Salesforce B2C Commerce for more information.
System Management
Linda’s manager gives her login access to Control Center. Control Center is where she can monitor the state of her instances and perform actions such as:
- Initialize instances.
- Start, stop, and restart instances.
- View usage data.
- View the audit log.
She also has access to Account Manager, a tool for managing her Business Manager and Control Center credentials. In the first week, her manager shows her the key Control Center data to watch.
Backups
By the end of her first week, Linda is starting to feel comfortable with the scope of her job. Before she leaves for the weekend, together she and her manager run through the instance backup process she will use every day.
Next Steps
Linda has a long list of responsibilities, but she's ready to get started. In the next unit, we watch as she sets up some new users and tackles basic user maintenance tasks.
Resources
- Salesforce Help: B2C Commerce Security Guide
- Trailhead: Architecture of Salesforce B2C Commerce
- Trailhead: Salesforce B2C Commerce for Developers
- Trailhead: Salesforce B2C Commerce Storefront Security Strategies
- Salesforce Help: Administering Your Organization
- Salesforce Help: Control Center
- Salesforce Help: Global Preferences
- Salesforce Help: Site Preferences