Define the Center for Internet Security Critical Security Controls
Learning Objectives
After completing this unit, you’ll be able to:
- Define the Center for Internet Security, Inc. (CIS®) Critical Security Controls® (CIS Controls®) Version 8.
- Describe how the CIS Controls were developed.
- Identify ways to use the CIS Controls.
- Explain why the CIS Controls matter.
- List the most important areas to focus on for Implementation Group 1.
The Center for Internet Security Critical Security Controls Version 8
What are the most common and important real-world cyberattacks that can affect your organization every day? What actions can defenders take to protect your organization? Where should your organization focus its attention?
If you’ve ever asked yourself these questions or heard your organization’s leadership ask them, you’re not alone. CIS is a nonprofit working with the global information technology (IT) community to safeguard public and private organizations against cyberthreats. They offer tools, guidelines, and services to bolster cyber defenses and foster global collaboration in cybersecurity. Organizations in many diverse sectors, including education, finance, government, retail, and technology, use the CIS Controls to help them deliver secure technology solutions.
The CIS Controls Version 8 (v8) were developed to help organizations establish awareness of and explore protections against cyberthreats. The CIS Controls are a set of recommended actions to thwart the most pervasive cyberattacks. They can help your organization:
- Identify and share insights into attacks and attackers.
- Implement tools to strengthen defenses.
- Align your cybersecurity program with regulatory and compliance frameworks.
V8 of the CIS Controls follow these design principles.
Principle |
Description |
|---|---|
Offense-Informed |
Prioritize CIS Controls based on data and on specific knowledge of attacker behavior and how to stop it. |
Focused |
Help defenders identify the most critical things they need to do to stop the most common attacks, and avoid attempts to solve everything. |
Feasible |
Implement specific and practical recommendations. |
Measurable |
Simplify CIS Controls, verify they’re measurable, and create thresholds where necessary. |
Aligned |
Create CIS Controls aligned with other governance, regulatory, and process management, schemes, frameworks, and structures, including the National Institute of Standards and Technology (NIST), Cloud Security Alliance (CSA), MITRE ATT&CK, and more. |
The CIS Controls Navigator is a tool that assists organizations in customizing, implementing, tracking and managing the CIS Controls, offering guidance and collaborative features for effective cybersecurity management.
Risk managers can use the CIS Controls Navigator to effectively implement tailored security controls.
Evolution of the CIS Controls
In 2008, a group of experts gathered together to share and discuss best practices in cybersecurity and created the CIS Controls. CIS developed the earliest version of the CIS Controls by using a standard list of publicly known attacks and coupled this with recommendations on preventing them. Starting in 2013, CIS worked with the Verizon Data Breach Investigations Report (DBIR) team to map the results of their large-scale data analysis directly to the CIS Controls, to match their summaries of attacks into a standard program for defensive improvement.
CIS’s Security Best Practices are more than a checklist of “good things to do” or “things that could help.” Instead they’re a prescriptive, prioritized, highly focused set of actions. It’s best to think of this list as a starting point. As you think through it, ask yourself these questions.
- Where can I get training, complementary information, explanations?
- How have others implemented and used these recommendations?
- Is there a marketplace of vendor tools and services to choose from?
- How will I measure progress or maturity?
- How does this align with the regulatory and compliance frameworks that apply to me?
To answer some of these questions, CIS maintains complementary information, working aids, and other support materials, including:
- Mappings from the CIS Controls to a wide variety of formal risk management frameworks
- Use cases for adoption
- A list of ongoing references to the CIS Controls in national and international standards, as well as state and national legislation
Implementation Groups
CIS created CIS Controls Implementation Groups (IGs) as a recommended new guidance to prioritize implementation. The CIS Controls IGs are self-assessed categories for organizations. Each IG identifies a subset of the CIS Controls that are applicable to an organization with a certain risk profile and resources. Specifically, IG1 focuses on essential cyberhygiene, the foundational set of cyberdefense Safeguards that every organization should apply to defend against the most common attacks. Safeguards are recommended individual defensive actions to protect against attacks.

An IG1 organization is small to medium-sized, with limited IT and cybersecurity expertise to dedicate toward protecting IT assets and personnel. We use the term enterprise throughout this module to refer to these organizations. Each IG then builds upon the previous one: IG2 includes IG1, and IG3 includes all CIS Safeguards in IG1 and IG2.
In this module, we focus on the CIS Controls in IG1. Even if your organization falls into another IG, learning about the implementation of the CIS Controls in IG1 is a good start, because these represent the foundational set of cyberdefenses all organizations should have.
Why the CIS Controls Matter
Implementing the CIS Controls in IG 1 defends against the five most prevalent attacks from the MITRE ATT&CK framework.
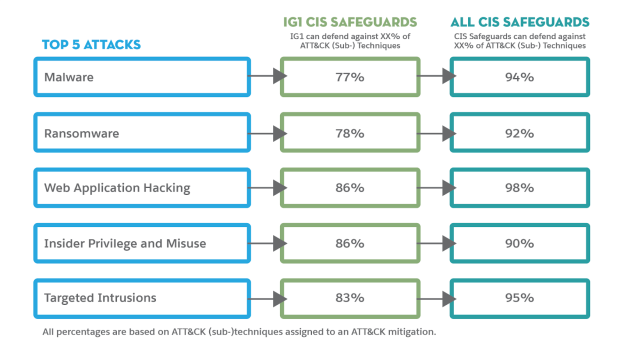
You should be aware of where your organization stands on essential cyberhygiene in order to defend against these attacks. Ask your business, IT, and security managers these questions.
- Do we know what assets we have and what is connected to our systems and networks?
- Do we know what’s running (or trying to run) on our systems and networks?
- Are we limiting and managing the number of people with administrative privileges to change, bypass, or override the security settings on our systems and networks?
- Do we have in place continuous processes backed by security technologies that would allow us to prevent most breaches, rapidly detect all that do succeed, and minimize damage to our business and our customers?
- Can we demonstrate that we have an effective monitoring strategy in place to our Board, our shareholders, and customers today?

If your organization can’t say yes to all these questions, you may still be compliant with regulations, but your data and customers may not be secure. The CIS Controls can help you create a prioritized list of business- or mission-critical processes, and inventory the information and computing assets that map to those processes. They can also help you compare existing security controls against the CIS Controls for each business- or mission-critical asset.
The Most Important Areas to Focus On for IG1
The CIS Controls for IG1 are as follows.
- Inventory and Control of Enterprise Assets
- Inventory and Control of Software Assets
- Data Protection
- Secure Configuration of Enterprise Asset and Software
- Account Management
- Access Control Management
- Continuous Vulnerability Management
- Audit Log Management
- Email and Web Browser Protections
- Malware Defenses
- Data Recovery
- Network Infrastructure Management
- Security Awareness Skills and Training
- Service Provider Management
- Incident Response Management
Each CIS Control includes Safeguards, which will be discussed in further detail in the following units.
Knowledge Check
Ready to review what you’ve learned? The following knowledge check isn’t scored—it’s just an easy way to quiz yourself. To get started, drag the description in the left column next to the matching term on the right. When you finish matching all the items, click Submit to check your work. If you’d like to start over, click Reset.
Great work!
Sum It Up
You now have a better understanding of the CIS Controls v8. In the next unit, you learn more about implementing Safeguards related to inventorying, controlling, and configuring assets, and protecting data.
