Use Field-Level, Event Bus, and Search Encryption
Learning Objectives
After completing this unit, you’ll be able to:
- Enable encryption for standard fields.
- Select standard fields for encryption.
- Enable encryption for event bus data.
- Enable encryption for search.

Go Deeper with Shield Platform Encryption
Zephyrus has seen how easy it is to enable Database Encryption and encryption for files and attachments. The company has done some encryption analyzing and confirmed that everything in the transactional database–standard and custom fields, metadata, and more–is being encrypted with the 256-bit DEKs. Large files and attachments are also protected. Ernesto and Calvin meet about the results. Ernesto points out that for some compliance policies, some specific fields with sensitive data need to have their own encryption traceability. Other sources of sensitive data, like event logs and search indexes, must also be protected. They decide to enable these features and continue testing.
Enable Encryption for Standard Fields and Select Fields for Encryption
To encrypt standard and custom fields, you need a tenant secret. Calvin created the first tenant secrets in Unit 3, so he can start encrypting other data, too. In his Developer Edition org, Calvin’s going to encrypt a few standard fields, like Description, Phone, and Email. He can choose standard or custom Text fields.
- From Setup, in the Quick Find box, enter
Platform Encryption, and then select Encryption Settings.
- Calvin’s going to test probabilistic encryption first. This is the default. Later, he’ll enable deterministic encryption on a few fields to maximize sorting on popular fields. The Deterministic Encryption toggle in Advanced Encryption Settings will let him enable deterministic encryption.
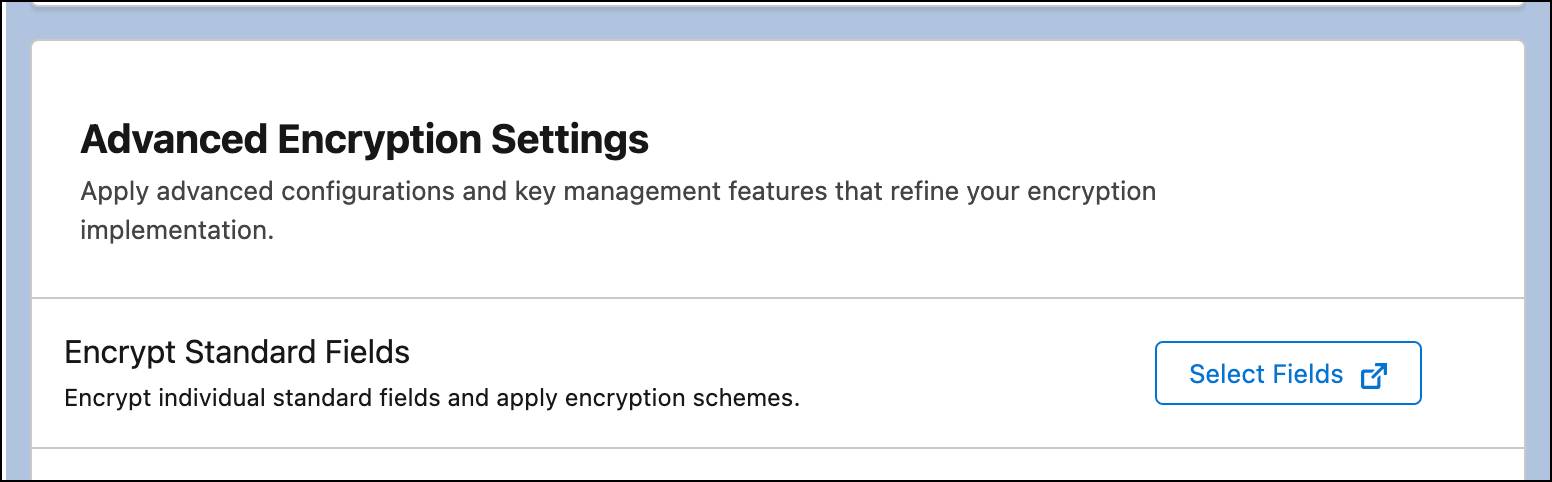
- In Advanced Encryption Settings, next to Encrypt Standard Fields, click Select Fields.
- Click Edit.
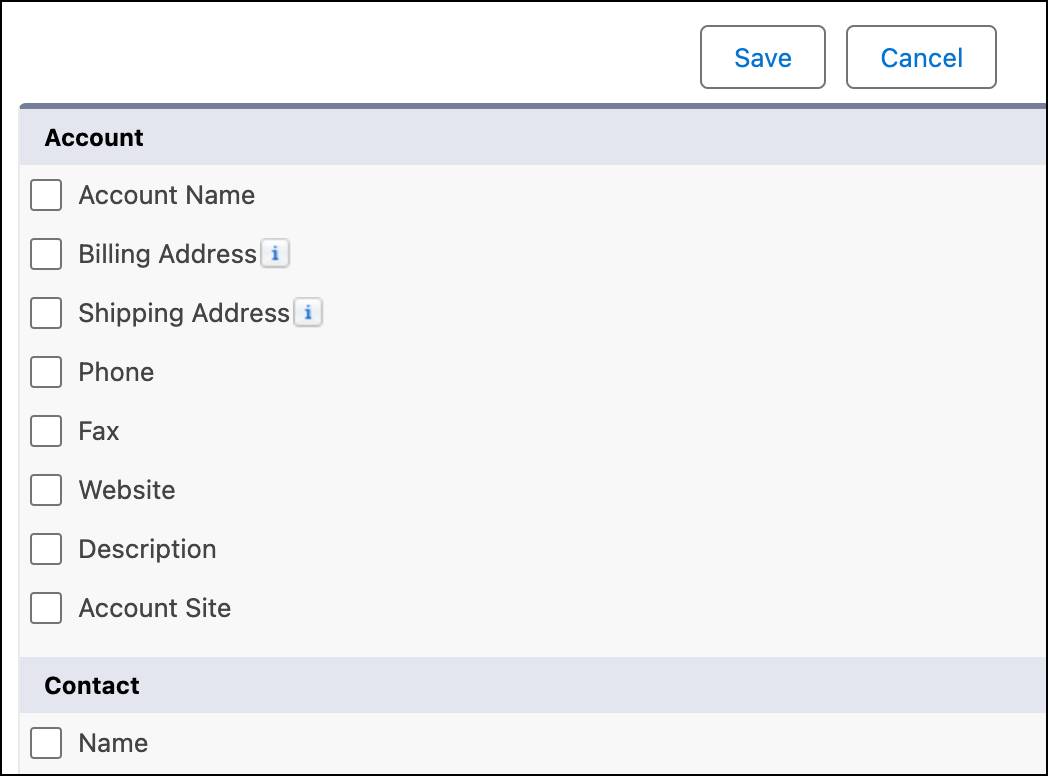
- In the Account section, select Phone, Fax, Description, and any other fields you want to encrypt, and click Save.
The automatic validation process checks all your org settings and sends you an email. If any settings block or prevent encryption, you receive instructions for fixing them. No blockers? Super! You’re all set. Field values are encrypted only in records created or updated after encryption is enabled. New data in the selected fields is encrypted automatically. And you can use the Encryption Statistics and Data Sync page to encrypt existing data in these fields.
Remember, encryption doesn’t take the place of field-level access controls. At runtime, encrypted data looks just like unencrypted data from the user’s point of view. Calvin makes sure that he assigns the appropriate field-level access only to those people who should see the plaintext data.
You can also encrypt custom fields, but we won’t do that here. Check out Set Up Field-Level Encryption in Salesforce Help.
Encrypt Event Bus Data
As a Salesforce admin, Calvin sees many events generated by data integrations, application communications, and audit trails. These event streams often contain a hacker’s treasure trove of sensitive data, from customer contact information and financial details to proprietary business insights. By enabling Shield Platform Encryption for the event bus, he knows he can ensure that this valuable and confidential information remains protected when at rest.
As for fields and files, encryption event data requires a tenant secret. The tenant secret for event data is also created when you create your first tenant secrets. So all that’s needed is to enable the feature.
- From Setup, in the Quick Find box, enter
Platform Encryption, and then select Encryption Settings.
- In the Encryption Policy section, enable Encrypt Change Data Capture Events and Platform Events.
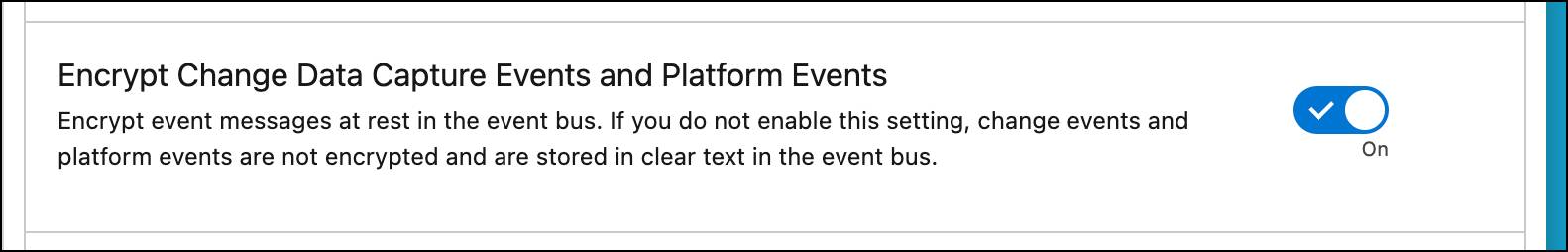
With this feature enabled, all new event data is encrypted. You can use the Encryption Statistics and Data Sync page to encrypt existing event bus data.
Encrypt Search Indexes
The last feature that Ernesto and Calvn are looking at is Search Index Encryption. Why encrypt search indexes?
Well, even if the data in your fields and files is beautifully encrypted at rest, the search index holds a readily accessible summary of that data to make searching fast and efficient. If you don’t encrypt the index, snippets of sensitive information can be exposed through search results, even to users who don’t have access to the underlying encrypted records.
Think of it like this: You might lock the doors to your house (encrypting fields and files), but if you leave easily readable notes about your great-grandmother’s silverware lying in your front yard (unencrypted search index), you’re still vulnerable. Encrypting the search index ensures that even those “notes” are scrambled and unreadable to anyone who shouldn't read them.
Enable Search Index Encryption
Unlike fields, files, attachments, and event bus data, Search Index Encryption uses a root key. You learned about root keys in Unit 1, Get Started with Shield Platform Encryption. Instead of using a KDF to derive the DEK, Salesforce creates a root key and a DEK. These are both visible on the Key Management page. The root key wraps the DEK until it is needed. Learn more at Encrypt Search Index Files with a Root Key. In the meantime, let’s enable Search Index Encryption.
- From Setup, in the Quick Find box, enter
Platform Encryption, and then select Encryption Settings.
- In the Encryption Policy section, enable Encrypt Search Indexes.

With this feature enabled, all new current indexes are encrypted. You can use the Encryption Statistics and Data Sync to encrypt existing indexes.
Next Steps for Zephyrus
Carolyn, Ernesto, and Calvin had an easy time enabling the various Shield Platform Encryption features for testing. They’ll continue to test with more people and more content. They’ll need to learn more about key rotation, external key management (EKM), and bring your own keys (BYOK). And as with any application that affects the entire company, they’ll need a comprehensive strategy for deploying Shield Platform Encryption to their production org.
Resources
- Salesforce Help: Set Up Field-Level Encryption
- Salesforce Help: Encrypt Search Index Files with a Root Key
- Salesforce Help: Sync Data with Self-Service Background Encryption
- Salesforce Help: Key Management and Rotation