Restrict Access with Field-Level Security, Permission Sets, and Sharing Settings
Create Permission Sets
Permission sets grant additional permissions to specific users, on top of their existing profile permissions, without having to modify existing profiles, create new profiles, or grant an administrator profile where it's not necessary.
Create a new permission set for hiring managers.
- From Setup, enter
Permission Setsin the Quick Find box, and select Permission Sets.
- Click New, and enter the details.
- Label:
Hiring Manager - Description:
Temporary permission set for those Hiring Managers that need to interview candidates for positions in their department
- License: Salesforce
- Click Save.
- Click Assigned Apps in the Apps section, then click Edit.
- Select Recruiting from the Available Apps list and click Add.
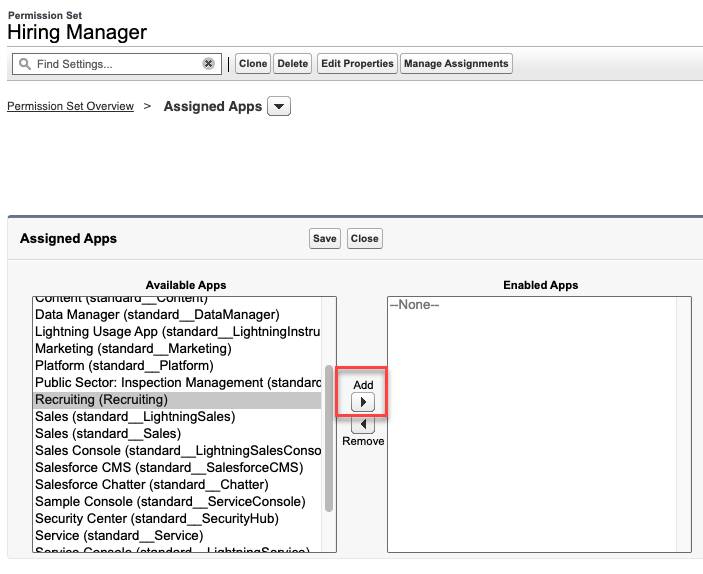
- Click Save.
- Click
 next to Assigned Apps and select Object Settings.
next to Assigned Apps and select Object Settings.
- Click Interviewers from the object list, and click Edit.
- Select Visible under Tab Settings.
- Select Read, Create, and Edit in the Object Permissions list.
- Click Save.
- Repeat steps 8-11 for the Job Applications, Job Postings, Job Posting Sites, Positions, and Reviews objects. Set the permissions to reflect what is shown in this table provided by Ling Wu.
Object |
Tab Setting |
Read |
Create |
Edit |
Delete |
|---|---|---|---|---|---|
Interviewers |
Visible |
✓ |
✓ |
✓ |
|
Job Applications |
Visible |
✓ |
|||
Job Postings |
✓ |
||||
Job Posting Sites |
Visible |
✓ |
|||
Positions |
Visible |
✓ |
✓ |
✓ |
|
Reviews |
✓ |
✓ |
✓ |
✓ |
Modify Field-Level Security
All standard objects have a predefined set of fields to capture common business information. While they can’t be deleted, field-level security can make them invisible. Field-level security controls which fields a profile or permission set can view and edit, overrides any less-restrictive field access, and controls settings in page layouts and search layouts.
Field-level security is universally enforced regardless of how a user is accessing Salesforce—page layout, related lists, report, and so forth. For this reason, field-level security is the preferred way to secure sensitive and confidential information, like salary ranges HR recruiters and hiring managers work with in their app.
Start by setting field-level security for the Salary Range field.
- From Setup, click Object Manager, and click Position.
- Click Fields & Relationships, then click Salary Range.
- Click Set Field-Level Security.
- For HR Recruiter and System Administrator, select Visible. (Ensure Visible is deselected for all other profiles.)
- Click Save.
Now set permissions.
- From Setup, enter
Permission Setsin the Quick Find box, and select Permission Sets.
- Click Hiring Manager.
- Click Object Settings in the Apps section.
- Click Positions in the list of object names, then click Edit.
- Under Field Permissions, select Read Access and Edit Access for Salary Range.
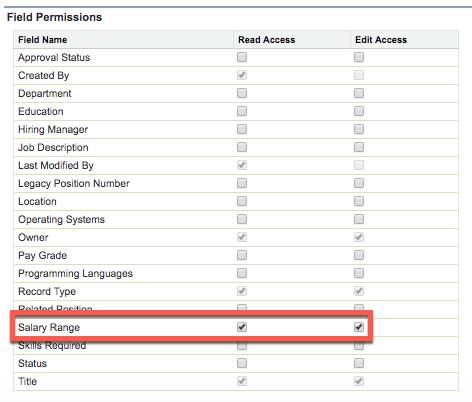
- Click Save.
Create Sharing Settings
To access a record, users must have the appropriate object permission on their profile or a permission set. By changing sharing settings from the organization-wide defaults, you set the default level of access users have to records they don't own in each object.
Ling Wu would like job postings to be the only HR custom object with public access. Achieve this by changing the organization-wide default sharing settings.
Set the organization-wide defaults for Recruiting app objects.
- From Setup, enter
Sharing Settingsin the Quick Find box and click Sharing Settings.
- Click Edit in the Organization-Wide Defaults section.
- Ensure that the Default Internal Access setting for the Candidate, Interviewer, Job Application, and Position objects is set to Private.
- Set the Default Internal Access for the Job Posting Site object to Public Read Only.
- Click Save.
By creating a custom profile, creating permission sets, updating field-level security, and modifying organization-wide default sharing settings, you’ve made AW Computing’s recruiting app a more secure tool. Ling Wu can rest easy knowing that her team—and anyone else accessing the app—will only see the data they’re authorized to see.
