Connect Resources with AWS Networking
Learning Objectives
After completing this unit, you’ll be able to:
- Describe the function of networking with AWS.
- Describe the benefits and features of Amazon VPC.
- Explain the benefits of Amazon Route 53.
- Explain the benefits of AWS Direct Connect.
With AWS Networking services, you can quickly grow your network capacity to deliver apps and content anywhere in the world, while maintaining management of your workloads.
Set Up Amazon Virtual Private Cloud (Amazon VPC)

Amazon VPCs are isolated portions of the AWS Cloud where customers deploy their AWS infrastructure—for example, they may deploy an Amazon Elastic Compute Cloud (Amazon EC2) instance or an Amazon Relational Database Service (Amazon RDS) instance.
VPCs are virtual networks.
- They support multiple subnets, routing, and fine-grained security.
- You have complete control over the selection of your own IP address range, creation of subnets, and configuration of route tables and network gateways.
- You can use both IPv4 and IPv6 in your VPC for secure and easy access to resources and applications.
Simple VPC Setup
In the simplified VPC diagram below, setup follows this process.
- list-style-type: inherit;
- Select an AWS Region.
- Create a VPC within that region, and then specify the full IP address range for all resources that will be hosted.
- Create subnets and choose whether they’ll allow connections to the public Internet or remain private.
- Launch your AWS resources, such as Amazon EC2 instances, into your VPC.
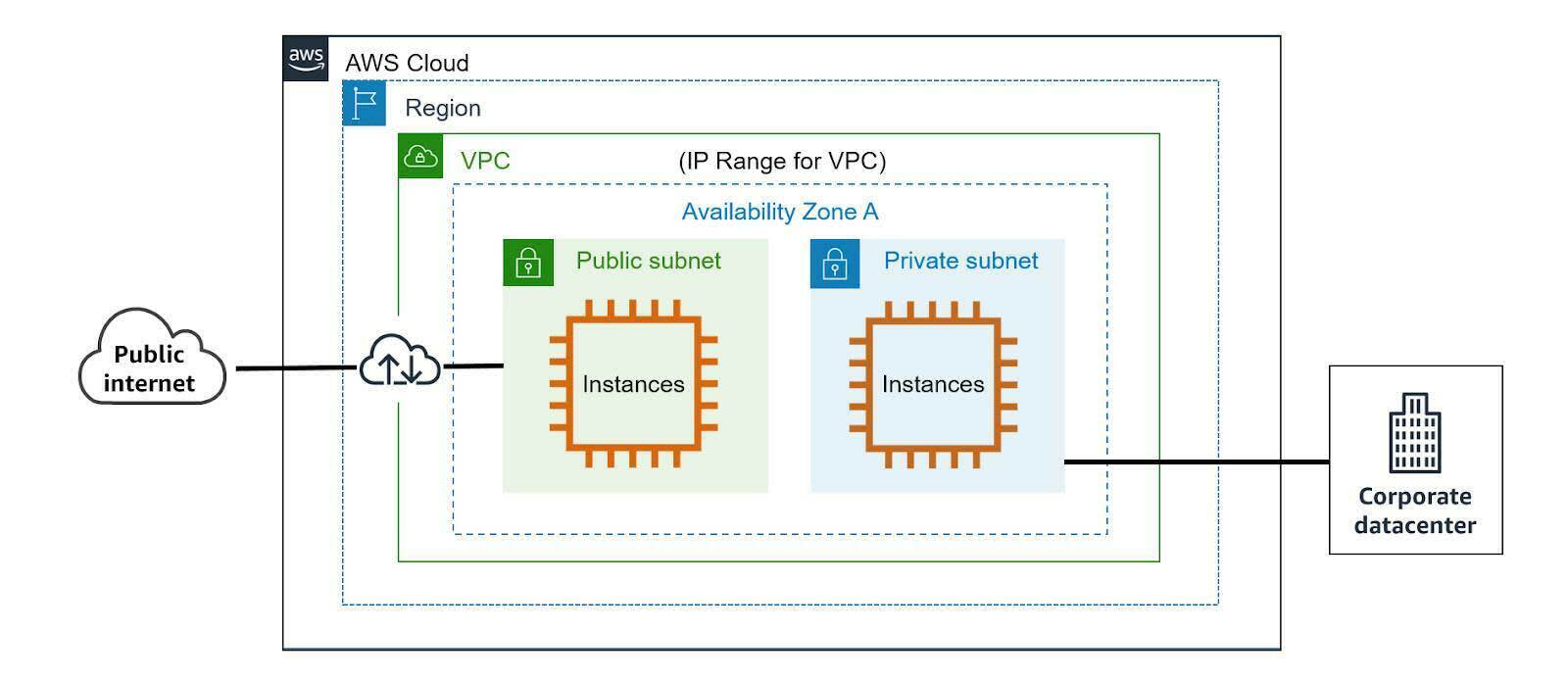
Some things to note when you set up your VPC.
- The VPC can include resources in any or all Availability Zones within the region.
- Every AWS account has one default VPC for each AWS Region. If you don't specify a subnet when you create a resource, it’s launched into your default VPC. You can launch resources into your default VPC without needing to know anything about Amazon VPC.
- Alternately, you can create your own VPC and configure it as you need.
- VPCs exist within a single AWS Region with up to five VPCs per Region.
Control Traffic with Security Groups
A security group acts as a virtual firewall for your instance to control inbound and outbound traffic. Security groups act at the instance level, not the subnet level. This means each resource in your VPC (whether it’s an EC2 instance, S3 bucket, or a database) could be assigned to a different set of security groups. If you don’t specify a particular group at launch time, the instance is automatically assigned to a default security group for the VPC.
For each security group, you set up rules that control the inbound traffic, and a separate set of rules that control the outbound traffic. By default, security groups allow no inbound traffic from any source and allow outbound traffic to all possible IPs.
Instances associated with a security group can’t talk to each other unless you add rules allowing the traffic (exception: the default security group has these rules by default).
Here are some additional details to keep in mind when creating security groups.
- You can specify allow rules, but not deny rules.
- You can specify separate rules for inbound and outbound traffic.
- When you create a security group, it has no inbound rules. No inbound traffic from another host is allowed until you add inbound rules to the security group.
- By default, a security group includes an outbound rule that allows all outbound traffic. You can remove this and add outbound rules that allow specific outbound traffic only. If your security group has no outbound rules, no outbound traffic originating from your instance is allowed.
- Security groups are stateful—if you send a request from your instance, the response traffic for that request is allowed to flow in, regardless of inbound security group rules. Responses to allowed inbound traffic are allowed to flow out, regardless of outbound rules.
VPC Multi-Tier Security Group
Below is an example of a classic AWS multi-tier security group. In this architecture, multiple different security group rules have been created.
- Starting at the web tier, there is a rule set up to accept traffic from anywhere on the Internet on port 80/443 by selecting the source of 0.0.0.0/0.
- Next, in the app tier, there is a security group that only accepts traffic from the web tier, and similarly, the database tier can only accept traffic from the app tier.
- Finally, there has also been a rule created to allow administration remotely from the corporate network over SSH port 22 (10.0.16.0/20).

Add More Security with Network Access Control Lists (NACL)
A network access control list (NACL) is an optional layer of security for your VPC. It acts as a firewall for controlling traffic in and out of one or more subnets. NACL rules automatically apply to all instances in the subnets it is associated with, so it can provide an additional layer of defense if security group rules are too permissive.
NACLs differ from security groups in several ways.
- They operate at the subnet level.
- They support both allow and deny rules.
- NACLs are stateless, so return traffic must be explicitly allowed by rules.
- They process rules in number order when deciding whether to allow traffic.
- NACLs are applied to all instances in the subnets they are associated with.
Go Further with Domains Using Amazon Route 53

Amazon Route 53 is a highly available and scalable Domain Name System (DNS) web service. You can use Route 53 to perform three main functions.
- Register domain names for websites or applications, such as example.com.
- Route Internet traffic to the resources for your domain name (example.com) or subdomain name (apex.example.com).
- Automatically check the health of your resources, such as web servers, to verify they are reachable, available, and functional.
You also can choose to receive notifications when a resource becomes unavailable and choose to route Internet traffic away from unhealthy resources.
With Route 53, you can register your domain name and route Internet traffic for the domain, or you can use Route 53 to route Internet traffic for a domain that you registered with another domain registrar.
Increase Bandwidth with AWS Direct Connect

AWS Direct Connect enables you to establish a private, dedicated network connection from your data center to AWS. In many cases, this capability can reduce your network costs, increase bandwidth throughput, and provide a more consistent network experience than Internet-based connections.
AWS Direct Connect links your internal network to an AWS Direct Connect location over a standard Ethernet fiber-optic cable. One end of the cable is connected to your router, the other to an AWS Direct Connect router. With this connection, you can create virtual interfaces directly to public AWS services (for example, Amazon S3) or to Amazon VPC, bypassing Internet service providers.

Core AWS Services Wrap-Up
In this module, you learned about AWS products and services and how they enable you to set up the best architecture for your business.
- How to use the Six Pillars of the AWS Well-Architected Framework to effectively meet your business needs.
- Amazon Elastic Compute Cloud (Amazon EC2) instance types, and Amazon Elastic Block Store (Amazon EBS), which provides block storage for Amazon EC2, enabling server functionality in the cloud.
- Storing and securing your data with services such as Amazon S3 (general-purpose storage) and Amazon Glacier (archiving and long-term storage), as well as Amazon Elastic File System (Amazon EFS) (NFS file system).
- The difference between relational (SQL) databases like Amazon Aurora and key-value or non-relational (NoSQL) databases like Amazon DynamoDB.
- Other database options like Amazon Neptune (graph database), Amazon Redshift (data warehouse), and Amazon DocumentDB (document database).
- How to use Amazon ElastiCache as an in-memory data store or cache to improve application performance.
- Using networking components, such as Amazon VPCs and subnets, securing your hosted instances with tools such as security groups, routing traffic with Amazon Route 53, and securely connecting directly to cloud services with AWS Direct Connect.
In the next module, dive into delivering content faster with the content delivery network, maintaining availability with Elastic Load Balancing and Auto Scaling, application integration, and how to manage and monitor your AWS resources.
Resources
-
External Site: Networking and Content Delivery on AWS
-
External Site: Security Groups for Your VPC
-
External Site: Amazon VPC Quotas
-
External Site: Getting Started with Route 53 Resolver
-
External Site: AWS Direct Connect
