Use a Secure Development Lifecycle
Learning Objectives
After completing this unit, you’ll be able to:
- Describe the OWASP secure development lifecycle (SDL) stages.
- Identify your responsibilities in each stage.
What Is the Secure Development Lifecycle (SDL)?
The secure development lifecycle (SDL) integrates security throughout all stages of the system/software development process. From requirements to design, coding to test, the SDL strives to build security into a product or application at every step.
There are several secure development lifecycle frameworks out there including:
- NIST Secure Software Development Framework
- Carnegie Mellon University Secure Software Development Lifecycle Processes
- Cisco Secure Development Lifecycle
- Synopsys Secure Software Development Lifecycle Phases
- US-Cert Secure Software Development Lifecycle Processes
In the past, security was often addressed late in the development cycle as part of the testing stage. Secure development allows you to identify bugs, flaws, and other vulnerabilities early in the development cycle giving you time to fix them before release. This can significantly minimize costs, prevent attacks, and protect your organization’s and customers’ most valuable asset: their data. This thorough approach ensures that your products and services continue to earn your customers’ trust.
The Five Stages of the OWASP SDL
For this module, we'll focus on the Open Worldwide Application Security Project's (OWASP) comprehensive framework for integrating security into the system/software development process. By following their five stages and performing the specific security activities at each stage, organizations can develop software that is secure from the outset and better protect their systems and data from potential security threats
Learning and implementing these stages will help you prioritize security throughout the entire development lifecycle. One way to remember how the SDL works is to remember that it typically has five stages. These stages form a structured process that creates a cycle.
|
Stage |
Question we are answering |
What You Can Do |
|
Plan |
What are the security requirements? |
Identify and document security requirements then use them as a basis for developing secure software. |
|
Design |
How will security requirements be implemented in the design? |
Create the software design with security in mind. The design should address the security requirements identified in the previous stage, and any security risks or threats that were discovered. Security controls are designed and implemented to mitigate potential vulnerabilities and ensure the software is secure. |
|
Implement |
How will security be implemented in the code? |
Develop the software using the secure design created in the previous stage. You follow secure coding practices, and implement security controls as planned. |
|
Test |
Are there security vulnerabilities or weaknesses in the system/software? |
Thoroughly test the software to identify any security vulnerabilities or weaknesses. This includes automated, manual, and penetration testing, to simulate real-world attack scenarios. Before release, a final security review is conducted to ensure that the software is secure. |
|
Release |
Is the system/software ready for deployment? |
The software is deployed into the production environment. Ongoing maintenance and monitoring of the software is also performed to ensure that any future security issues are promptly identified and addressed. |
In a cyclical development model, the design, implement, and test stages are all iterative processes. You don’t just design, implement, and test once—you cycle through these steps repeatedly as you build your product or service. For instance, you might build a product and realize in the test stage that it doesn’t quite meet the security acceptance criteria you defined during the design stage. That’s when you cycle back and tweak it some more to meet all stakeholder requirements.
Learning and executing these stages will help you prioritize security throughout the entire development lifecycle.
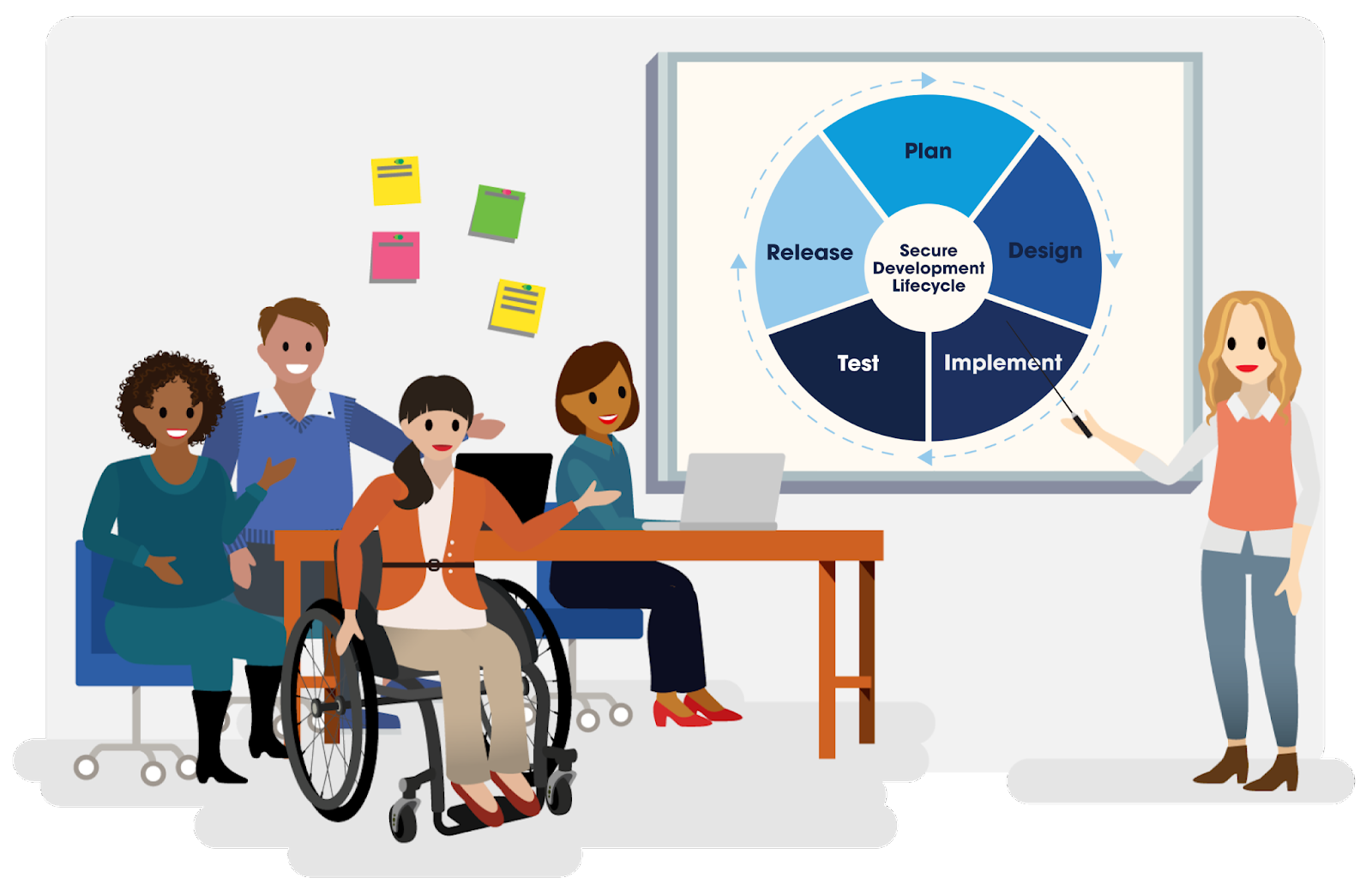
Now that you understand what the secure lifecycle development cycle is, and why it's so important, let’s take a look at how to implement it.
Resources
- External Site: Open Web Application Security Project (OWASP) Foundation: OWASP in SDLC
- Trailhead: Application Security Basics
- External Site: CISA.gov: Securing the Software Supply Chain: Recommended Practices for Developers
Quiz Scenario
Omar, a developer at a government agency that deals with space exploration, has taken his agency’s secure development lifecycle (SDL) training and is feeling confident about building security into each of the seven stages of his current project.