Start a Career in Automotive Cybersecurity
Learning Objectives
After completing this unit, you’ll be able to:
- Explore training, certifications, and activities to become an automotive cybersecurity professional.
- Prepare a plan to start a career in the automotive cybersecurity industry.
Skills Needed in the Automotive Industry: A Comparison of IT and Automotive Cybersecurity Resumes
In the dynamic landscape of cybersecurity, it is important to understand the distinct skill sets required for different domains. To provide another picture of the contrasting demands between traditional IT cybersecurity and automotive cybersecurity, let’s examine two resumes side by side. We will analyze a traditional IT cybersecurity engineer resume alongside a connected vehicle cybersecurity engineer resume.
By comparing these two examples, we can gain insights into the specific skills and expertise that may be desired in each role. Please keep in mind that the following example resumes serve as illustrations. Actual job requirements may vary, with employers looking for specific skills and qualifications.
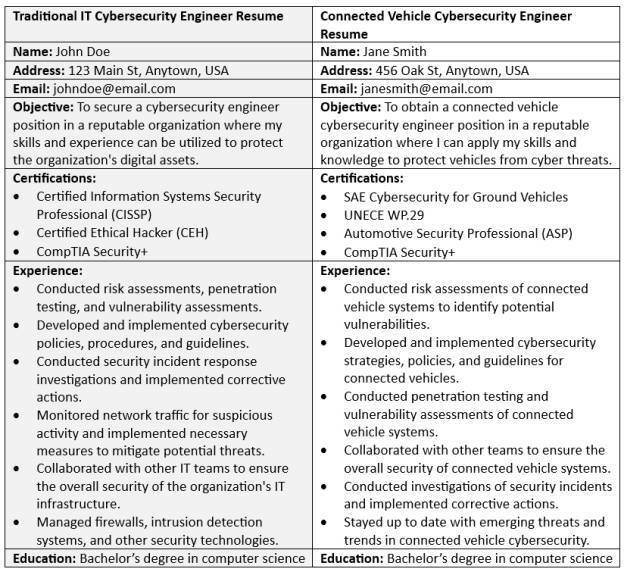
Both resumes showcase a similar set of skills and certifications related to cybersecurity. Additionally, both candidates have experience identifying potential vulnerabilities and developing risk mitigation strategies.
However, the connected vehicle cybersecurity engineer resume emphasizes experience in conducting risk assessments and vulnerability testing specifically for connected vehicle systems, and includes a set of certifications more tailored to the automotive industry. The traditional IT cybersecurity engineer resume highlights experience in developing and implementing cybersecurity policies and guidelines for an organization’s IT infrastructure, and a set of certifications more aligned with general IT security. Overall, both resumes demonstrate a strong background in cybersecurity and a commitment to staying up to date with emerging threats and trends in the industry.
Cybersecurity Training for Connected and Autonomous Vehicles
The automotive industry faces unique cybersecurity challenges. Professionals in this field need to have specialized knowledge and skills to protect vehicles and their systems from cyber threats. The following scenario demonstrates how an individual can begin to transition into automotive cybersecurity.
Scenario
Leverage existing cybersecurity knowledge, skills, and professional networks.
Meet Eunice. Eunice is an experienced IT cybersecurity professional who wants to shift her focus to the automotive industry.

Eunice is eagerly looking to broaden her professional horizons by pursuing automotive cybersecurity certifications to augment her current resume. In order to identify the certifications that align with her career aspirations, she conducts comprehensive research within the automotive cybersecurity industry. Throughout her exploration, Eunice compiles a list of recommended certifications, taking note of the requisite experience necessary to succeed in the exams and perform the associated work.
Much to her delight, Eunice discovers that the skills she honed to obtain her existing IT cybersecurity certifications possess significant transferability to automotive cybersecurity. With newfound confidence, she plans to highlight the following existing training, certifications, knowledge, and skills on her resume, showcasing her readiness and suitability for a career in automotive cybersecurity.
Automotive Cybersecurity Training/ Certifications |
Requires Demonstrated Experience in… |
Eunice’s Existing IT Certifications |
Eunice’s Transferable Knowledge, Skills, and Experience |
|---|---|---|---|
|
UL Solutions:
UL Certified Cybersecurity Professional in Automotive (UL-CCSP)
|
Cybersecurity policy, threat analysis and risk assessment (TARA), product development, vulnerability analysis and management |
International Information System Security Certification Consortium (ISC)²: Certified Information Systems Security Professional (CISSP)
|
Security and risk management, communication and network security, security operations, asset security |
|
Society of Automotive Engineers SAE International: Automotive Cybersecurity Certification
|
Risk management, threat and risk analysis, security specification and verification |
International Council of E-Commerce Consultants (EC-Council):
Certified Ethical Hacker (CEH)
|
Ethical hacking techniques penetration testing, vulnerability assessment, and network security |
|
The Linux Foundation:
Software Engineering Basics for Embedded Systems
|
Secure software development for embedded systems, software engineering, risk management, product integration |
International Information System Security Certification Consortium (ISC)²:
Certified Secure Software Lifecycle Professional (CSSLP)
|
Secure software development and secure coding practices |
In addition to mapping her existing IT security skills to desired skills in automotive cybersecurity, Eunice participates in the following activities to build a new and different skill set for her career transition.
-
Conducts threat assessments: Eunice volunteers at her friend’s dealership to conduct free threat assessments of customer vehicles. Eunice uses the Threat Assessment and Remediation Analysis (TARA) methodology to assess and identify cyber threats and select countermeasures effective at mitigating the vulnerabilities.
-
Conducts security assessments: Eunice works with a mentor skilled in the automotive industry to conduct security assessments of local automotive companies and suppliers to evaluate their cybersecurity readiness. Eunice uses the ISO/SAE 21434 standard for automotive cybersecurity to evaluate their policies, procedures, and security controls, and identify potential areas for improvement.
-
Develops secure coding practices: Eunice contributes to Automotive Grade Linux, an open-source project focused on developing a common platform for automotive software development. She contributes to the project by developing and implementing secure coding practices for the platform.
-
Stay up-to-date with the latest developments: Eunice volunteers with the Automotive Information Sharing and Analysis Center (Auto-ISAC), an industry-led organization focused on sharing cybersecurity information and best practices in the automotive industry. She participates in groups and committees focused on different aspects of automotive cybersecurity, such as threat intelligence, incident response, and best practices.
-
Participate in interactive competitions and exercises: Eunice joins several teams to participate in various automotive cybersecurity events (for example, SAE CyberAuto Challenge, CyberTruck Challenge, HackerDom Capture the Flag (CTF) Competition) to test and enhance her cybersecurity skills and knowledge specific to the automotive industry.
Creating New Professional Networks
To expand her knowledge and understanding of the unique training, certifications, regulations, and job opportunities in the automotive industry, Eunice engages in the following activities to create new professional networks.
-
Contacts professionals in the automotive industry: Eunice requests a connection to professionals in the automotive industry who she discovers on a large social network for the business community. Eunice sends messages to introduce herself, asking for advice on transitioning into the industry and exploring potential job opportunities.
-
Joins social media groups focused on automotive cybersecurity: Eunice researches and joins several social media groups focused on automotive cybersecurity. These groups provide opportunities for her to connect with other professionals, share knowledge and expertise, and stay up-to-date with the latest developments in the field.
-
Builds a personal brand around automotive cybersecurity: Eunice begins to build a personal brand related to automotive cybersecurity on a business focused social media platform. She creates and shares content related to the industry, engaging with other professionals, and showcases her skills and experience.
-
Follows companies and thought leaders in the industry: Eunice follows companies and thought leaders in the automotive industry on social media. This provides insights into the latest trends and developments in the field, and potential job opportunities.
By participating in these activities, Eunice broadens her network of contacts in the automotive industry, gains insights into the industry’s unique requirements and practices, and identifies potential job opportunities.
Develop a Career in Automotive Cybersecurity
In addition to implementing the strategies that Eunice used, for those looking to work in automotive cybersecurity, whether or not you are currently in an IT cybersecurity role, the following steps can help.
Action |
Resources/Activities |
|---|---|
Learn about and practice securing automotive systems |
|
Master embedded systems |
|
Attend conferences/ workshops |
|
Obtain certifications/join organizations |
|
Network/seek mentorship |
|
Apply for internships/jobs |
|
In conclusion, starting a career in the automotive cybersecurity field requires a well-structured plan that encompasses acquiring relevant knowledge, developing technical skills, and engaging with the industry community.
By following the steps outlined in the table, individuals can progressively build a strong foundation in automotive systems, communication protocols, and embedded systems, while also participating in conferences, training programs, and networking events. Obtaining industry-specific certifications and joining professional organizations will further enhance one's credibility and expertise in the field.
With dedication and persistence, aspiring professionals can successfully transition into the automotive cybersecurity domain and contribute to safeguarding the present and future of connected and autonomous vehicles.
Sum It Up
In this module, you've learned how to develop relevant skills and create a plan of action to enter the automotive cybersecurity industry.
Interested in learning more about cybersecurity roles and hearing from security professionals? Check out the Cybersecurity Career Path on Trailhead.
Resources
-
External Site: NHTSA: Automated Vehicles for Safety
-
External Site: McKinsey & Company: Autonomous Driving’s Future: Convenient and Connected
-
External Site: NXP: Here’s How the Auto Industry Is Taking Cybersecurity Seriously
-
External Site: Auto-ISAC: Automotive Cybersecurity Training (ACT)
-
External Site: ISA: Industrial Internet of Things (IIoT) Cybersecurity Explained
-
External Site: SAE International: Learn