Get to Know Automotive Cybersecurity
Learning Objectives
After completing this unit, you’ll be able to:
- Explain and differentiate connected and autonomous vehicle (CAV) cybersecurity and IT cybersecurity.
- Identify common attacks and vulnerabilities in connected and autonomous vehicles.
Connected and Autonomous Vehicles
Connected and autonomous vehicles (CAVs) are revolutionizing transportation by combining the intelligence, connectivity, and data of smartphones, tablets, PCs, and TVs.
A connected vehicle has internet access and communication capabilities, enabling data sharing with other devices, vehicles, and infrastructure. Connected vehicles offer real-time traffic updates, remote diagnostics, infotainment, and vehicle-to-vehicle (V2V) or vehicle-to-infrastructure (V2I) communication.
An autonomous vehicle, or self-driving vehicle, navigates without human intervention using sensors, cameras, radar, lidar, and artificial intelligence (AI) for steering, acceleration, and braking decisions. Though often connected, the main difference is their ability to operate without human input.
CAVs offer numerous features. But concerns remain among users of connected autonomous vehicles about the data collected, the data’s use by manufacturers, and the risk of unauthorized access by malicious actors.
Automotive vs. Traditional IT Cybersecurity
It’s important to recognize the difference between traditional IT security and the specific security challenges presented by connected and autonomous vehicles (CAVs). One key distinction is that CAVs are considered operational technology (OT) because they use hardware and software to control and monitor physical processes and devices. Understanding this difference is crucial because OT systems, like those in CAVs, have unique security requirements and face specific challenges that need to be addressed.
IT cybersecurity, also known as computer or network security, involves safeguarding computers, servers, mobile devices, electronic systems, networks, and data from digital attacks, damage, unauthorized access, or theft. The goal is to ensure the confidentiality, integrity, and availability of information and systems.
Automotive cybersecurity focuses on protecting vehicle systems, components, and networks from malicious attacks, damage, unauthorized access, and other security issues. It involves securing vehicle communication protocols, software, and hardware crucial for safe and reliable operation. The goal is to prioritize availability and reliability over confidentiality because the safety of vehicles depends on their ability to operate reliably and without interruption. However, prioritization of availability and reliability over confidentiality can pose challenges when implementing effective security measures. Here are some examples.
-
Limited resources for encryption: Allocating resources for robust encryption mechanisms may be limited, as encryption can require significant computational power and potentially impact real-time operations. Encrypting all communication channels and data within the vehicle systems is crucial for strong confidentiality measures but can pose challenges in terms of resource allocation and real-time performance.
-
Access to diagnostic and maintenance interfaces: To ensure availability and reliability, manufacturers and service providers often require access to diagnostic and maintenance interfaces within vehicles. This access can introduce potential security risks, as unauthorized individuals or malicious actors may exploit these interfaces to manipulate vehicle systems, compromising confidentiality.
-
Over-the-air updates and remote access: To maintain availability and reliability, automotive systems frequently utilize over-the-air updates and remote access capabilities. While these functionalities are essential for system maintenance and improving performance, cybercriminals can also target them to gain unauthorized access to vehicle systems and compromise the confidentiality of sensitive information.
-
Balancing privacy concerns: The collection and processing of vehicle and driver data are essential for enhancing vehicle performance and enabling advanced features. However, prioritizing availability and reliability may require the transmission and storage of certain data, potentially raising privacy concerns.
Building upon the challenges posed by prioritizing availability and reliability over confidentiality, it becomes evident that automotive cybersecurity diverges from traditional IT cybersecurity in significant ways. Understanding these distinctions is crucial for professionals operating in the automotive cybersecurity domain. Several key areas differentiate automotive cybersecurity from traditional IT cybersecurity:
Key Area |
Traditional IT Cybersecurity |
Automotive Cybersecurity |
|---|---|---|
Real-time constraints and safety-critical systems |
Can handle occasional delays without immediate harm. |
Operate in real-time environments, demanding immediate responses and minimal latency for safety-critical functions (for example, braking, steering, acceleration). |
|
Architecture
|
Often use a client-server architecture, where clients initiate requests to servers for data or services. |
Typically employ a distributed architecture, where multiple devices communicate directly with each other on a shared network. |
|
Communication
|
Typically rely on point-to-point or client-server communication, where messages are sent directly between specific endpoints. |
Messages are broadcast on the network, meaning that all connected devices receive the messages. |
|
Potential for physical harm
|
Cybersecurity incidents, while damaging, typically do not pose an immediate physical threat. |
Breaches can lead to physical harm to passengers, pedestrians, and property. |
|
Supply chain complexity
|
Often rely on a wide range of electronic components sourced from multiple suppliers |
Typically involves a more extensive and diverse array of components, including specialized hardware, sensors, control units, and software, sourced from a complex network of global suppliers making it more difficult to track and manage the entire supply chain |
Regulations |
Often issued by general regulatory bodies, such as the Federal Trade Commission (FTC), the European Union Agency for Cybersecurity (ENISA), or the Information Commissioner’s Office (ICO) in the UK. Address a wide range of systems and technologies such as servers, networks, databases, and cloud services. |
Typically developed and enforced by organizations and agencies specializing in transportation or automotive safety, such as the National Highway Traffic Safety Administration (NHTSA) or the European Union's European Automobile Manufacturers Association (ACEA). Focus on technologies unique to automotive systems, such as in-vehicle networks (for example, CAN, LIN, FlexRay), Electronic Control Units (ECUs), embedded systems, and vehicle-to-everything (V2X) communications. |
Exploring Vulnerabilities in Connected and Autonomous Vehicles
With vehicles becoming increasingly connected and digitized, it is essential to understand the vulnerabilities that arise with each function and capability. Let’s explore the emerging vulnerabilities by understanding CAV capabilities along with the required knowledge and skill involved in securing and protecting them.
-
Car subscription services: These services offer special car features but require drivers to share personal information. For instance, when signing up for a car subscription, personal details like name, address, and credit card information are provided. In the event of a data breach, attackers can steal this information and gain access to online banking accounts. Mitigating this vulnerability requires implementing data privacy measures during the signup process. This includes practices such as encryption, secure data storage, and access control mechanisms to safeguard personal information.
-
Car-related mobile apps: These apps enhance the driving experience but often require personal and vehicle information that attackers seek. For instance, a parking finder or fuel tracking app may need personal and vehicle details. In the event of a data breach, attackers can exploit this information for phishing scams. To address this vulnerability, expertise in implementing robust authentication and authorization mechanisms is essential. Measures like multi-factor authentication and secure session management help prevent unauthorized access to personal information, enhancing overall security.
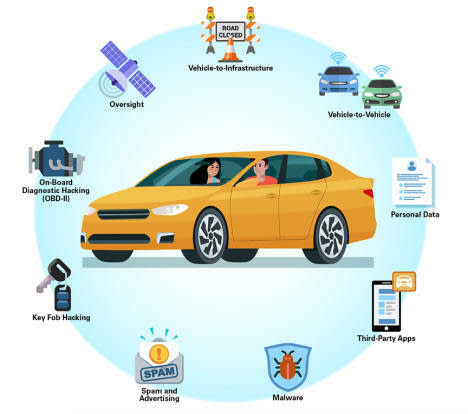
At the same time, there is one specific capability/vulnerability in cars, called the Controller Area Network (CAN) protocol, which allows different parts of the car to talk to each other. The CAN has helped make cars better and safer, but it also has vulnerabilities that attackers can target, which include:
-
No built-in security: The 1980s’ creation of the CAN system prioritized simplicity, reliability, and speed over security. Consequently, it lacks built-in encryption, authentication, and access control, enabling eavesdropping, device impersonation, and unauthorized access. Addressing this vulnerability requires designing secure automotive cybersecurity architectures that incorporate encryption, authentication, access control, and other security measures to prevent unauthorized access and device impersonation.
-
Accessible system messages: The CAN system’s messaging structure allows all connected devices to view messages, creating vulnerabilities for eavesdropping, message spoofing, and alteration. To address this, expertise in implementing secure communication protocols within the CAN system is crucial. This involves incorporating encryption algorithms, message authentication mechanisms, and secure message transmission techniques to prevent unauthorized access, spoofing, and message tampering.
-
Challenges with add-on security: Implementing security features such as encryption and authentication in the CAN system poses challenges due to its simple design, high-speed communication requirements, and compatibility with older systems. Enhancing system security may involve modifying the CAN system itself or introducing additional hardware and software components. To address this vulnerability, expertise in implementing network segmentation and access control mechanisms within the CAN system is vital. This approach helps segregate critical components from less secure ones, minimizing the impact of potential attacks and restricting an attacker's ability to interact with all devices within the network.
-
Multiple access points: Modern vehicles offer multiple access points to the CAN system, including diagnostic ports, wireless connections (Bluetooth, Wi-Fi), and entertainment systems. These additional entry points provide attackers with more opportunities to infiltrate the CAN system. To address this vulnerability, expertise in developing secure hardware and firmware for interconnected network devices within the CAN system is essential. This involves implementing secure boot processes, firmware integrity checks, and hardware-based security measures to mitigate the associated risks and enhance the overall security posture of the system.
As connected and autonomous vehicles (CAVs) become more prevalent, it is crucial to identify and address the vulnerabilities they introduce. By addressing these vulnerabilities, we can ensure the continued advancement of CAV technology while safeguarding user data and protecting against potential cyber threats.
Knowledge Check
Ready to review what you’ve learned? The knowledge check below isn’t scored—it’s just an easy way to quiz yourself. To get started, drag the automotive industry vulnerability in the left column next to the matching description on the right. When you finish matching all the items, click Submit to check your work. If you’d like to start over, click Reset.
Great job! Now that we’ve reviewed information about connected and autonomous vehicles and their common vulnerabilities while also identifying the skills needed to secure and protect against those vulnerabilities, let’s explore the automotive cybersecurity learning environment and plan a strategy to start a career in the industry.
Resources
- External Site: Red Hat: What Is Operational Technology (OT)?
- Trailhead: Active Cyber Defense in the Energy Sector
- External Site: Upstream: 2023 Global Automotive Cybersecurity Report (registration required)
- External Site: Upstream: Automotive Cybersecurity Standards and Regulations
- Blog: Praetorian: Anatomy of an Automotive Security Assessment
- PDF: NHTSA: Cybersecurity Best Practices for the Safety of Modern Vehicles
- External Site: SAE International: Enhanced Penetration Testing for Automotive Cybersecurity
- External Site: Auto-ISAC: Security Development Lifecycle: Best Practice Guides