Understand Network Security
Learning Objectives
After completing this unit, you’ll be able to:
- Describe what a network is.
- Identify ways people and assets access a network.
- Explain network security engineering.
What Is a Network?
A network is a fabric of interconnected elements that are related to each other. We encounter a variety of networks on a daily basis. Networks allow us to travel, to connect with other people, to view entertainment content, to collect and disburse information, and so much more. Similarly, a computer network connects two or more computers with various devices in order to share resources among people and other computers. Computer networks consist of many devices: servers, routers, computers, printers, scanners, and so on. We access computer networks to check social media, read email, review our bank account balance, and perform countless other functions.
In this module, we get to know Jim and Florence who are network security professionals. We learn about their job responsibilities, plus the skills they need and the tools they use to protect computer networks from potential security threats.
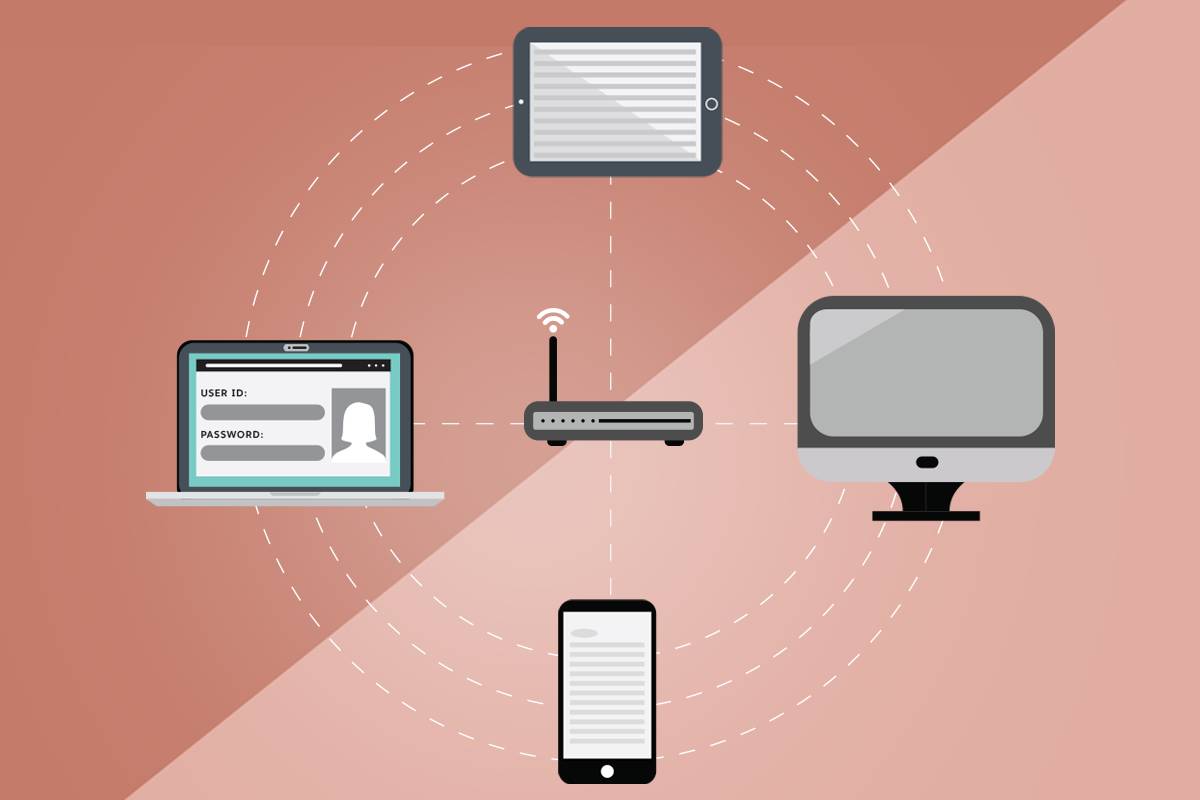
How People and Devices Access a Network
Because we live in an interconnected world, it’s important to understand how computer network access works. It’s also imperative that we protect these networks since we rely on them every day. Let’s look at how encryption and authentication help to protect networks.
Some computer networks are public and some are private. A public computer network allows anybody to connect to it. You access a public computer network whenever you connect to a Wi-Fi hotspot at a coffee shop or inside an airport. A private computer network has restricted access. It allows only certain people and devices to connect to it. In this way, a private network regulates who and what can access its resources. Businesses operate private networks that allow their employees to communicate with each other and access internal, company-related information.
Since we don’t want just anybody to access our personal information, like our bank account balance, websites use authentication and encryption to protect network access and data transfers. To check your account balance, your bank requires that you prove who you are—this is authentication.
Encryption converts data from standard text into coded data that is not humanly readable. This ensures that nobody else can retrieve your private data that is being transmitted across a public computer network. Websites use encryption to protect the information that’s passed between your device, for example, your cell phone and your bank. Many websites use the Hypertext Transfer Protocol Secure (HTTPS) to encrypt data.
Now let’s check in with Florence. She’s a network security engineer at a large bank that serves customers in multiple countries. Part of Florence’s job is to ensure that only an authorized account holder can access his or her account. Her bank adopted an authentication process that requires the account holder to provide a username and password, or a debit card and a PIN (personal identification number), to log in to their account.
Florence also implemented multi-factor authentication, known as MFA. To access their account with MFA, a customer provides their username/password and is then required to verify their identity with an additional authentication factor, such as an authenticator app or security key. MFA provides an added layer of security that helps prevent unauthorized access to bank accounts.
Understand Network Security
We expect computer networks to be available and secure 24 hours a day so we can access them whenever and wherever we want. When computer networks are unavailable, it affects how we conduct our daily lives. If your bank’s computer system is unavailable, you may be unable to pay your bills (ouch!) or transfer funds to the appropriate account.
Because of the massive amount of personal, health, financial, and other data stored on computer networks, securing public and private computer networks is essential. As a result, network security professionals build multiple layers of security into their computer systems to provide what is commonly referred to as CIA: confidentiality, integrity, and availability.
Many types of people may try to gain unauthorized access to a computer network. These range from hackers who want to gain access for fun or fame, to cybercriminals who want to steal money and information, to cyberterrorists who want to disrupt and damage.
As a network security engineer at a medical clinic, Jim knows health records are a prime target for cybercriminals. Any security breach can have legal and regulatory ramifications resulting in fines and sanctions. To minimize those risks, Jim uses hardware and software tools that provide added layers of protection for patients.
While Jim is aware that external cybercriminals want to attack his systems, he knows that threats can also arise internally from intentional and unintentional actions by employees or other authorized users. This can arise from a malicious insider (like a disgruntled employee) or accidental deletion by an uninformed user. Because of this, it’s critical that he knows his system configuration and typical usage patterns so he can recognize potential security threats. In many cases, internal attacks are often accidental occurrences, so the best way to deal with them is through cybersecurity education and awareness for all employees.

In the end, it’s the network security professional’s job to ensure a computer system’s CIA by keeping out unwanted intruders while providing authorized access to those who need it. Network security professionals are not always the most popular people in an organization because the security measures that they employ can make network access a bit of a challenge. Think of their job as being similar to a stadium ticket taker. This person causes a slowdown in the stadium entry process that can result in ticket holders having to wait in line. But the ticket takers fill an important role by ensuring that each person who enters the stadium has a valid ticket.
Knowledge Check
Ready to review what you’ve learned? The knowledge check below isn’t scored—it’s just an easy way to quiz yourself. To get started, drag the function in the left column to the matching category on the right. When you finish matching all the items, click Submit to check your work. If you’d like to start over, click Reset.
Great job! Network security is critical to the safety and security of the data (customer data, financial information, health records, intellectual property, and so on) that is stored on a network. It’s a big job, but somebody needs to do it. Are you up for the task?