Integrate Service Providers with Salesforce
Learning Objectives
- Discuss how connected apps can integrate service providers with your Salesforce org.
- Describe how to integrate a service provider with your Salesforce org, using a connected app that implements SAML 2.0 for user authentication.
- Describe how to integrate a service provider with your Salesforce org, using a connected app that implements OpenID Connect for user authentication.
A Quick Review of SSO
Single sign-on (SSO) lets users access other applications without logging in separately to each one—and without having to create (and remember) different user credentials for each app. With SSO, you can connect your users to external applications. For example, a call center rep can click the Customer Support tile in their Salesforce org’s portal and access the Customer Support org without reentering their credentials.
Identity Providers and Service Providers
To understand SSO flows, it’s important to be familiar with the roles that identity providers and service providers play.
| Provider Type | Role |
| Identity Provider | A trusted service that enables users to access other external applications without logging in again. |
| Service Provider | A service that accepts identity on behalf of the external application from an identity provider. |
When Salesforce acts as your identity provider, you can use a connected app to integrate a service provider with your org. For this type of SSO flow, the connected app implements SAML 2.0 or OpenID Connect for user authentication.
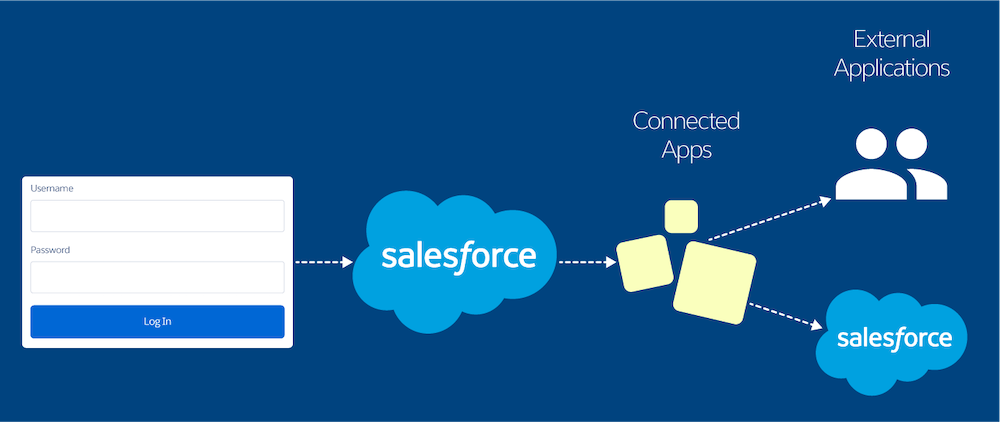
Integrate a Service Provider with SAML
To integrate a service provider with your Salesforce org, you can use a connected app that implements SAML 2.0 for user authentication. Use this option if your org already uses the SAML protocol.
Let’s say you’ve built a custom Your Benefits web app that implements SAML 2.0 for user authentication. You want your users to be able to log in to this app with their Salesforce credentials. To set up this SSO flow, configure the Your Benefits web app as a connected app. Because your org implements the SAML protocol, your Salesforce org is already configured as the identity provider. When users log in to their Salesforce org, they can access the Your Benefits web app without separately logging in.
- A Sales employee logs in to their Salesforce org and opens the Your Benefits web app.
- Salesforce sends a SAML response to the service provider, which you defined when configuring the connected app.
- The service provider identifies the user, and validates the digital signature sent by Salesforce in the SAML response.
- The user is logged in to the Your Benefits web app.
Integrate a Service Provider with OpenID Connect
Like SAML, OpenID Connect is a protocol that enables SSO between two services. Unlike SAML, OpenID Connect is built for today’s API economy. It adds an authentication layer on top of OAuth 2.0 to enable secure exchange of ID tokens that contain user information alongside OAuth access tokens.
To integrate a service provider with your Salesforce org, you can use a connected app that implements OpenID Connect for user authentication. To use this option, the service provider must accept OpenID Connect tokens. Configure a connected app with the OpenID Connect scope for your service provider. The OpenID Connect scope passes user information in an ID token. Users can then log in to the external app with their Salesforce or Experience Cloud credentials.
For example, you want your users to sign on directly from your Salesforce org to an external Wellness Tracker app that accepts OpenID Connect. So you create a connected app for the Wellness Tracker app. For the connected app, you enable OAuth settings, select the “Allow access to your unique identifier (openid)” scope, and configure an ID token. This configuration enables the SSO flow for your Wellness Tracker app by integrating the service provider with your Salesforce org.
- A user opens the Wellness Tracker app.
- Salesforce sends the connected app’s client ID and secret to the Wellness Tracker service, along with additional authentication data.
- The Wellness Tracker service validates the request to access the app. It then returns the information to the Salesforce server in exchange for tokens to access user data.
- Salesforce sends the tokens to the Wellness Tracker service.
- The Wellness Tracker service authorizes access to the user’s Wellness Tracker account.
- The user is logged in to the Wellness Tracker app.
Keep Trekking
You’re doing great! You’ve learned about connected apps, how to use them to integrate external apps with the Salesforce API, and how to use them to integrate service providers with Salesforce. Now let’s talk about using connected apps to provide authorization for external API gateways.
Resources
- Salesforce Help: Integrate Service Providers as Connected Apps with SAML 2.0
- Salesforce Help: Integrate Service Providers as Connected Apps with OpenID Connect