Audit Account Activity with AWS CloudTrail
Learning Objectives
After completing this unit, you will be able to:
- Describe the features and benefits of AWS CloudTrail.
- Use CloudTrail to audit user activity.
If you have only one user in your AWS account and that user is you, getting visibility into what’s happening inside your AWS account is easy. However, it gets more complicated when you add other users, especially when those users are AWS services, applications, and people authenticating themselves through a role from another AWS account or identity provider.
If one of them deletes a resource, or if they start bitcoin mining in your AWS account, how do you find out? How do you get insight into the types of actions that all these users are performing inside your account?
In this unit, you learn how to get visibility into account activity to determine if users have the right level of permissions, if any illegal actions are occurring, and to make sure users are doing what they’re supposed to do.
Monitor Activity in Your AWS Account
CloudTrail is an AWS service that tracks all actions taken by a user, role, or AWS service in your AWS account. It records them in an ongoing record of activity. When any API call is made in your AWS account, you can use CloudTrail to view, search, download, and analyze that activity. For example, if your database is deleted within your AWS account, you can view that activity and see information such as who deleted the database, when they deleted it, which database they deleted, and more.
- Log in to the AWS Console.
- Find and click AWS CloudTrail.
- Then, click Event History to view past activity in your account.

Filter Your Event History to Home in on Specific Activity
With CloudTrail, you can view the last 90 days of event history. Depending on the number of users and AWS services in your account, this may be a lot of activity to sift. Thankfully, CloudTrail lets you filter through this event history, using the resource name, the event type, the type of resource, and more.
For example, if you’re on a whodunnit mission to find out who deleted your cat photo database, you can filter this history by the database resource and see all the API calls that took place against that service.
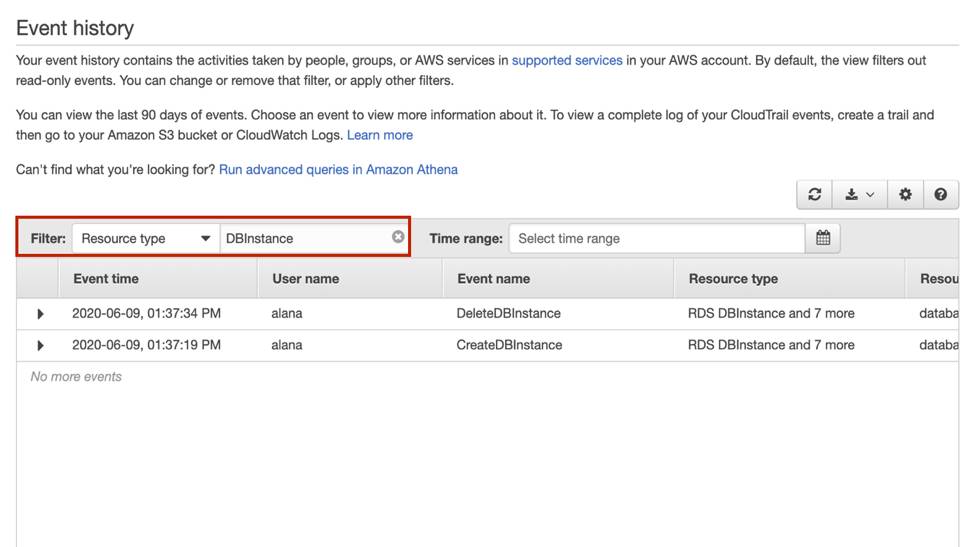
View Event Details
If you click any of these events, you see expanded details about the activity that took place. For example, if you click the event line that shows the DeleteDBInstance event, you see details like what access key was used, the AWS Region, the time of the event, source IP address, user name, and more.
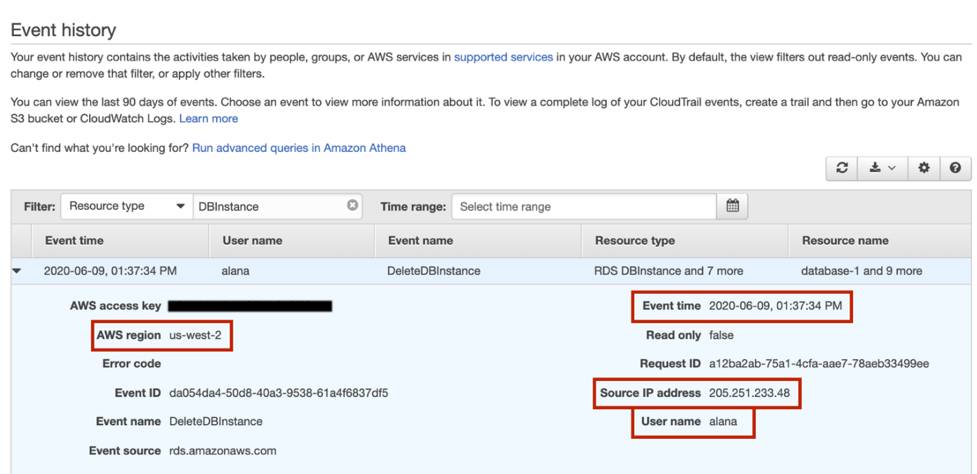
You can answer the following questions.
- Who deleted the database? You can see the user named alana deleted it.
- When did Alana delete the database? She deleted it at 1:37:34 PM on June 9, 2020.
- Where did Alana delete the database from? Alana deleted the database from the IP address 205.251.233.48.
- Which region did Alana delete the database from? The database resided in us-west-2 and Alana deleted it in that region.
Wrap Up
When you create an AWS account, CloudTrail is already enabled and begins to track activity within your AWS account, enabling you to govern and audit who is doing what. In the next module, you begin building your cat photo application using AWS compute services.