Use Multi-Factor Authentication
Learning Objectives
After completing this unit, you will be able to:
- Explain how to protect the AWS root user through multi-factor authentication (MFA).
- Choose the right AWS-supported MFA device for your root user.
The Case for Multi-Factor Authentication
When you create an AWS account and first log in to that account, you use single-factor authentication. Single-factor authentication is the simplest and most common form of authentication. It only requires one authentication method. In this case, you use a username and password to authenticate as the AWS root user. Other forms of single-factor authentication include a security pin or a security token.
However, sometimes a user’s password is easy to guess. For example, your coworker Bob’s password, IloveCats222, might be easy for someone who knows Bob personally to guess, because it’s a combination of information that is easy to remember and describes certain things about Bob (1. Bob loves cats, and 2. Bob’s birthday is February 22).
If a bad actor guessed or cracked Bob’s password through social engineering, bots, or scripts, Bob might lose control of his account. Unfortunately, this is a common scenario that users of any website often face.
This is why using MFA has become so important in preventing unwanted account access. MFA requires two or more authentication methods to verify an identity, pulling from three different categories of information.
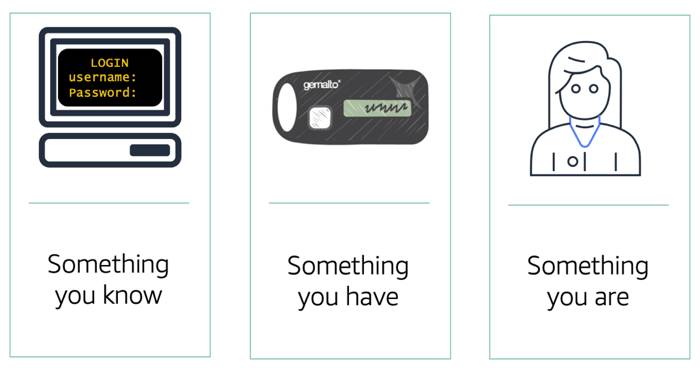
- Something you know, such as a username and password, or pin number
- Something you have, such as a one-time passcode from a hardware device or mobile app
- Something you are, such as fingerprint or face scanning technology
Using a combination of this information enables systems to provide a layered approach to account access. Even though the first method of authentication, Bob’s password, was cracked by a malicious user, it’s very unlikely that a second method of authentication, such as a fingerprint, would also be cracked.
This extra layer of security is needed when protecting your most sacred accounts, which is why it’s important to enable MFA on your AWS root user.
Use MFA on AWS
If you enable MFA on your root user, you are required to present a piece of identifying information from both the something you know category and the something you have category. The first piece of identifying information the user enters is an email and password combination. The second piece of information is a temporary numeric code provided by an MFA device.
Enabling MFA adds an additional layer of security because it requires users to use a supported MFA mechanism in addition to their regular sign-in credentials. It’s best practice to enable MFA on the root user.
Review Supported MFA Devices
AWS supports a variety of MFA mechanisms, such as virtual MFA devices, hardware devices, and Universal 2nd Factor (U2F) security keys. For instructions on how to set up each method, check out the Resources section.
| Device | Description | Supported Devices |
|---|---|---|
|
Virtual MFA |
A software app that runs on a phone or other device that provides a one-time passcode. Keep in mind that these applications can run on unsecured mobile devices, and because of that, may not provide the same level of security as hardware or U2F devices. |
Authy, Duo Mobile, LastPass Authenticator, Microsoft Authenticator, Google Authenticator |
|
Hardware |
A hardware device, generally a key fob or display card device that generates a one-time six-digit numeric code |
Key fob, display card |
|
U2F |
A hardware device that you plug into a USB port on your computer |
YubiKey |
Wrap Up
As a best practice in AWS, you should enable MFA on your AWS root user to increase your account security. Because MFA requires you to submit multiple forms of authentication to prove your identity, your account is less likely to be compromised or breached.
Continue to the next module to deepen your understanding about security and permissions in AWS with roles, groups, and IAM.