Guard Data Transmission
Learning Objectives
After completing this unit, you’ll be able to:
- Define transport layer security (TLS).
- Identify how public key infrastructure (PKI) secures data transmission.
Encrypting Data Transmission with TLS
One critical link in securing data transmission is to use transport layer security (TLS) to encrypt it. TLS is a cryptographic protocol designed to secure communications over a computer network. A protocol describes how the cryptographic algorithms should be used to secure information. Cryptographic protocols are used to secure transferred messages during application-level data transport. They are widely used in applications such as email, instant messaging, and voice over IP (VoIP). But their use as the security layer in Hypertext Transfer Protocol Secure (HTTPS) remains the most publicly visible instance for secure web browsing.
Using a PKI Service
Many organizations use internal services to simplify the process of getting certificates for TLS. If your organization has such a service, you should use it for provisioning and delivering the short-lived certificates to hosts and services upon which TLS relies. If your organization does not have an internal service, you should consider planning for or adopting a public key infrastructure (PKI) service. A PKI service simplifies the process of encryption by setting up a system for acquiring the certificates that TLS uses to authenticate identity.
Let’s start by looking at how a PKI service works. PKI is a set of roles, policies, hardware, software, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates and manage public-key encryption. Digital certificates establish your credentials when doing business or other transactions on the web. They are issued by a certification authority (CA) who vouches for their authenticity.
In cryptography, a PKI is an arrangement that binds public keys with respective identities of entities (like people and organizations). A public key is the key your web browser uses to encrypt or scramble data into ciphertext, which is sent to a website. The data is then decrypted with a private key held by the entity that is authorized to view the data. The binding is established through a process of registration and issuance of certificates at and by a CA. A CA confirms the validity of a website's certificate and, therefore, verifies that the website itself is valid.
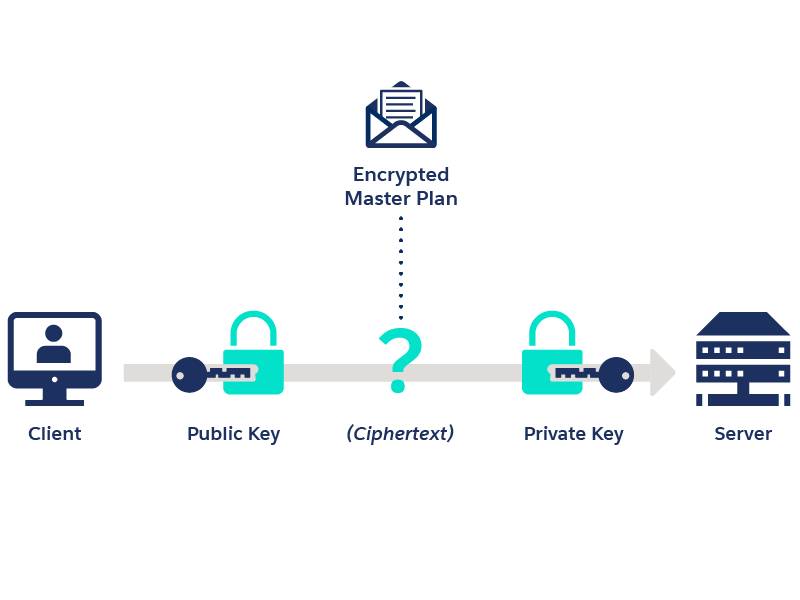
In general, PKI provides “trust services.” Trust services is the process of ensuring the electronic identification of signatories and services. Trust service objectives respect one or more of the following capabilities: confidentiality, integrity, and authenticity.
Confidentiality: Ensures that no entity can maliciously or unwittingly view your data in cleartext. Data is encrypted to make it secret so that even if it is read, it appears as gibberish. This is why the most common use of PKI for confidentiality purposes is in the context of TLS.
Integrity: Ensures that if transmitted data is tampered with in any way, there is clear evidence that it happened. This traceability is a key trust objective of PKI systems.
Authenticity: Ensures that you have connection certainty for authentication of data in transit on both the server-side and the client-side of the transmission.
These trust services are why organizations use PKI services to generate certificates for data encryption over TLS. A certificate service is basically an organization of services surrounding a CA that allows it to issue, renew, and revoke certificates. Certificates are what pass a public key to computers that need to communicate securely using the PKI system.
Your organization most likely has its own customized PKI service to generate the certificates you need to securely encrypt your data in transit using TLS. You should use that system to encrypt data in transit, so that you do not risk exposing yourself and your organization to attackers on the open internet who might wish to do you harm.
Resources