Apply Threat Hunting Techniques to Business Systems
Learning Objectives
After completing this unit, you’ll be able to:
- Describe a threat hunter’s activities on the job.
- Apply threat hunting techniques for a business.
A Day in the Life of a Threat Hunter
Imagine yourself as a threat hunter, responsible for protecting the operational systems of a large ecommerce organization. You develop effective threat modeling strategies to identify potential risks and vulnerabilities in the ecommerce platform. Additionally, you actively engage in threat hunting, proactively searching for and responding to threats that could compromise the system’s security. Together, these efforts contribute to the overall protection and resilience of the ecommerce platform.
Analyzing the Platform
As you begin your day, you dive into threat modeling activities by analyzing the ecommerce platform’s intricate system architecture. You draw upon your knowledge and experience to apply a range of specialized skills, including:
- Network and system architecture analysis
- Understanding of common attack vectors and techniques
- Proficiency in using threat intelligence sources and tools
- Familiarity with security frameworks and models
- Ability to conduct thorough vulnerability assessments
Your experience is what enables you to expertly assess critical components, such as customer databases, payment gateways, and order processing systems, evaluating them for signs of weakness and potential threats (for example, hackers, malware, botnets). Additionally, the following certifications validate your skills.
- Certified Information Systems Security Professional (CISSP)
- GIAC Certified Forensic Analyst (GCFA)
- GIAC Certified Incident Handler (GCIH)
- GIAC Cyber Threat Intelligence (GCTI)
- eLearnSecurity Certified Threat Hunting Professional (eCTHP)
- Offensive Security Certified Professional (OSCP)
Building Your Expert Team
No threat hunter stands alone. You collaborate closely with your team of highly skilled experts to address a wide range of challenges and fortify the platform’s defenses against cyberattacks.
As a team, you use the following tools and technologies to enhance your capabilities and support your specific roles.
Team Members |
Primary Tool/s |
Tool Description |
|---|---|---|
Incident response analysts and security operations center (SOC) analysts |
Security information and event management (SIEM) platforms |
SIEM platforms centralize collection and analysis of security event logs from various sources. |
Cybersecurity analysts |
Intrusion detection systems (IDS), intrusion prevention systems (IPS), vulnerability scanning tools |
IDS and IPS tools monitor network traffic to facilitate detection and prevention of unauthorized access attempts and malicious activities. Vulnerability scanning tools allow identification of vulnerabilities in systems and networks. |
Digital forensics investigators |
Forensic analysis tools |
Forensic analysis tools provide the means to collect, preserve, and analyze digital evidence in a meticulous and legally admissible manner. |
Threat intelligence analysts |
Threat intelligence platforms |
Threat intelligence platforms provide actionable insights into the tactics, techniques, and procedures (TTPs) that threat actors employ. |
By leveraging your team’s collective expertise and using advanced tools, you quickly address challenges from all angles to strengthen the platform’s defenses against cyberattacks.
Engaging in the Hunt
The threat hunting loop is a cyclical process that threat hunters follow to proactively identify and respond to potential threats. Threat modeling provides the foundation for guiding threat hunting activities and helps threat hunters focus on specific risks and potential threats. It involves several iterative steps that help guide their investigation and mitigation efforts, ensuring a comprehensive approach to security. The process unfolds through the following stages:
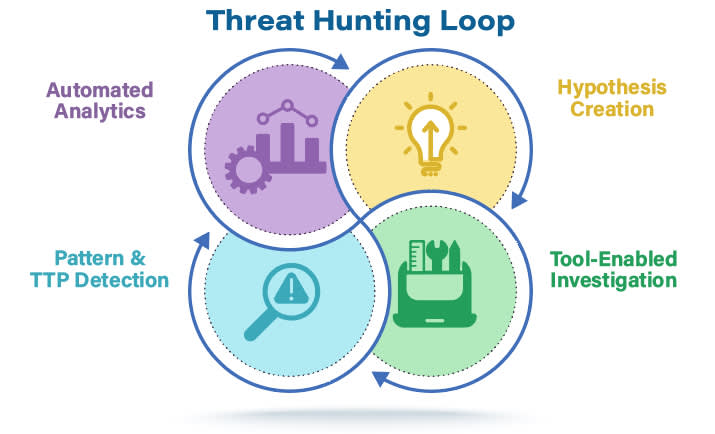
-
Hypothesis creation: Armed with environmental knowledge and threat intelligence, threat hunters develop educated hypotheses regarding potential threats and their behaviors. For example, “A certain threat actor group is likely to target our organization using this specific technique.” These assumptions form the basis of their investigation.
-
Tool-enabled investigation: Leveraging an array of cutting-edge tools and technologies, threat hunters gather and analyze data from diverse sources. This data exploration lets them delve deep into potential indicators of compromise (IOCs) and suspicious activities.
-
Pattern and TTP detection: Through meticulous data analysis and pattern recognition, threat hunters identify noteworthy patterns, trends, or anomalies that sometimes signify the presence of threats. Their focus lies in uncovering the TTPs that threat actors employ to gain unauthorized access or engage in malicious activities.
-
Automated analytics: Equipped with advanced analytics tools and technologies, threat hunters process vast volumes of data more efficiently. Automated analysis aids in correlating events, detecting established patterns, and highlighting potential risks, which empowers the team with valuable insights.
Threat hunting also feeds back into the threat model. As you and your team discover new attack patterns or identify weaknesses in the organization’s defenses, you update the threat to enhance its accuracy and relevance. By carefully executing each phase in the hunting loop, you and your team identify, analyze, and address the specific threats and vulnerabilities that affect the ecommerce platform, which enables a more proactive and effective security posture.
Harnessing the Power of MITRE and CrowdStrike
To navigate the complex world of threat hunting, you and your team harness the MITRE ATT&CK® framework, the MITRE Engage framework, MITRE’s list of adversary groups, and CrowdStrike’s Adversary Universe. These tools provide a comprehensive set of resources that categorize and catalog a wide range of adversary groups and commonly used TTPs.
During your investigation, you and your team uncover several concerning TTPs that could potentially pose a threat to the ecommerce platform. These include targeted spear phishing campaigns, attempts at credential harvesting, and suspicious lateral movement within the system.
Additionally, based on your thorough threat modeling process and analysis using resources such as CrowdStrike’s Adversary Universe and MITRE’s list of adversary groups, you suspect that the ecommerce organization is being targeted by the following advanced persistent threat (APT) groups known for their sophisticated techniques and persistent targeting of high-value organizations.
You and the threat hunting team take immediate action to mitigate the potential risks. This includes intensifying monitoring efforts, enhancing security controls, and implementing targeted threat hunting activities. You and your team also collaborate with other teams within the organization, such as incident response and IT operations, to immediately respond to active threats and promptly address vulnerabilities in the network.
By quickly responding to these threats, you and the threat hunting team provide the ecommerce platform users with a secure and trustworthy online shopping experience. Your threat hunting expertise ensures the company stays one step ahead in the race against cyber criminals.
As we conclude this glimpse into a day in the life of a threat hunter, it becomes clear that the threat hunter’s role is crucial in cybersecurity. As a threat hunter, you protect organizations, customer data, and the integrity of the digital world. If you’re ready for an exciting career that involves problem-solving, creativity, and continuous learning, embrace the role of a threat hunter and make a significant impact in cybersecurity.
Sum It Up
Now that you’ve learned more about a threat hunter’s tools, skills, and responsibilities, let’s explore the future implications for threat modeling and threat hunting.
Resources
- Trailhead: Get Started with Threat Intelligence
- Trailhead: Active Cyber Defense in the Energy Sector
- Trailhead: A Career in Cybersecurity
- External Site: Infosec: Threat Hunter
- External Site: CrowdStrike Adversary Universe
- External Site: MITRE: Adversary Groups
- External Site: MITRE Engage
- External Site: MITRE ATT&CK