Examine the Human Side of Social Engineering
Learning Objectives
After completing this unit, you’ll be able to:
- Analyze patterns in digital body language.
- Identify vulnerabilities in online habits.
What Is Digital Body Language?
According to a National Institute of Health study, by the end of today, each of us will have spent about 5.5 hours (or 55%) expressing ourselves through body language. This means we're constantly observing and interpreting subtle signals from others: a slight shift in posture, a quick glance away or a warm smile. These nonverbal signals are very important aspects of our face-to-face communication. Most of us have naturally developed the ability to read body language. But something fascinating is happening in our modern world: We're developing an entirely new language of interaction—our digital body language.
Digital body language might sound like a strange concept at first—after all, how can we have body language in a space where our physical bodies don't exist? However, every time we log in to a website, check our email, send a text message, or browse social media, we're sending nonverbal cues and signals. These digital cues create a complex web of communication that informs how others perceive us in cyberspace.
Consider your own digital habits. When you join a video call, do you immediately turn on your camera or do you wait to gauge the situation? How quickly do you typically respond to text messages? Do you answer video calls from numbers you don't recognize, or do you always pick up? Does your willingness to answer depend on the time of day? These aren’t just random decisions—they're part of your unique digital body language.
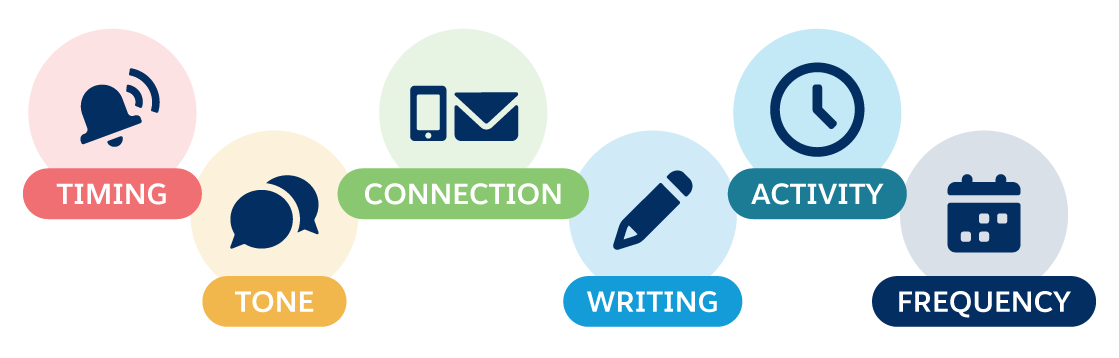
Our digital body language shows up in numerous ways, including:
- How quickly we respond to texts and emails
- The tone we use in our emails
- The ways we prefer to connect with others (for example, text, emailing, video calls)
- Our use of punctuation, capitalization, and emojis
- The time of day when we are most active online
- How often we’re online
Understanding our specific digital habits and the reasons behind them is crucial for our online security. Why, you might be wondering? Because just as skilled observers can read physical body language to understand our thoughts and emotions, cyberattackers can interpret our digital body language to identify patterns in our online behavior—especially now that AI-based attacks are becoming more prevalent. This information can provide attackers with insight to predict how we'll respond to certain situations, which makes us easier to manipulate. By becoming aware of these patterns and intentionally breaking them, we can disrupt their strategies and regain control over our online security.
Social Engineering in Action
Social engineering is the practice of exploiting natural human traits like trust, curiosity or fear by influencing the decisions we make around those traits. For example, imagine receiving an email about an upcoming and unexpected payment. You get excited about this unexpected payment. This email captures your curiosity because it gives you just enough information to make you feel or hope that it's directed to you, so you need to act. Your next step after reading the email, the cyberattacker hopes, is for you to click a link or download a document because you want to learn more.
The problem here isn't your excitement or curiosity—it's how your decision-making is being influenced. When you act on emotion, especially in cyberspace, you’re often acting on incomplete information. In the previous scenario, it’s the feelings of excitement and curiosity that should be the trigger for prudence and to ask yourself more questions. For example:
- Who is the sender?
- Have you communicated with this sender before?
- Is the email coming from a legitimate address? How would you find out?
By pausing to ask these questions, you begin to uncover the gaps in the story the email is telling–and this is exactly what cyberattackers using social engineering try to prevent. Their goal is to use emotion–urgency, fear, trust–to push you into immediately acting.
This doesn't make us careless or gullible. It simply highlights how human decision-making can be influenced when emotion and lack of information are at play. This lack of information or “knowledge failure” is the absence of required action when knowledge falls into any of these categories.
- Unknown
- Known but not used
- Underutilized
- Misapplied
- Not available when and where needed.
Managing knowledge risk (the probability and possible impact of knowledge failure) by first understanding our own digital habits and patterns can help to mitigate the threat of social engineering.
For example, imagine you're a manager who consistently checks your email at 7:15 AM, typically responding immediately to time-sensitive messages and messages from your chief information security officer (CISO) and direct reports. You’re also more active on LinkedIn during your lunch break. You often travel to conferences for work, and you enjoy posting pictures of yourself attending these conferences.
Attackers look for these digital behavioral clues:
- Timing (clues about when you are most likely online): The email arrives at 7:15 AM, during your regular morning check.
- Sender (clues about who you quickly respond to): It appears to come from your CISO.
- Content (clues about what grabs your attention): You need to verify conference booking details.
- Context (clues about your habits): An urgent request about an actual conference that you’re registered to attend.
- Pressure (clues about how you react in high-stakes situations): The conference is tomorrow, and you have less than a day to resolve this issue.
Using these insights, they can craft a perfectly timed phishing email like this one:
|
Subject: Urgent: Action Required for Conference Travel Booking From: [CISO Name]@yourcompany.com To: [Your Name]@yourcompany.com Sent: 7:10 AM Hi, [Your Name], I’m sending this message so early because we have a slight issue with your flight and hotel booking for tomorrow’s Tech Conference in Phoenix, AZ. The travel agency flagged a system error, and your reservation is at risk of being cancelled. To avoid losing your spot, please verify your booking details (see link). [Verify Booking Details Here] If this is not resolved quickly, you may not be able to attend and I really need you to represent the company at this conference. Please let me know immediately once it’s done. Best regards, [CISO Name] Chief Information Security Officer |
|---|
By exploiting your schedule, habits and preferences, an attacker creates a message that looks and feels natural, increasing likelihood of success.
How to Manage Knowledge Risk
Knowing that successful social engineering attacks thrive on triggering emotions like curiosity, fear, and excitement to bypass critical thinking, you take note of your anxiety. This leads you to immediately verify the email before acting. For example:
-
Access the original source: Instead of clicking the link in the email, you log in directly to the travel agency website to check your booking information.
-
Check for consistency: You look for subtle inconsistencies in the email, such as typos in the email address, unusual formatting, or language that your CISO would not typically use.
-
Check the destination: You hover over the email link (without clicking) to check its destination. If the email is directed to an unexpected or unrelated site, it’s a red flag.
-
Verify the sender: Instead of replying to the email directly, you call or email your CISO using a known good number, rather than the number given in the email, and ask whether they sent the email.
The information you collect by taking these steps better equips you to make a decision regarding whether to click the link in the email. Because you now have a more complete picture of the situation, you've determined this is a phishing email and you report it to the cybersecurity team.
The Human Element: Cyberpsychology
Have you ever wondered why so many people are still victims of online scams? The answer lies in cyberpsychology—the study of how we think and act in digital spaces. Most security measures focus on technology like firewalls and encryption, but they miss a crucial piece: human behavior. Cyberpsychology addresses this gap by sharing research that reveals how our minds and decision-making processes can become vulnerabilities.
Natural human responses to acting on information while stressed, anxious, or rushed can make us and, by association, our organizations vulnerable to attacks, no matter how many technical safeguards are in place.
Cybersecurity leaders are starting to catch on. Instead of just adding more policies and regulations, they're creating security measures that work with human nature, not against it. For example, measures like password managers and two-factor authentication prioritize human nature by simplifying tasks and seamlessly integrating them into everyday workflows. This means using tools and processes that align with actual behaviors.
Looking ahead, cyberpsychology is only going to become more important as our digital and physical lives continue to merge. With technologies like augmented reality (AR) and artificial intelligence (AI) becoming more common, understanding why we do the things we do online will be most important to our overall security.
Sum It Up
In this unit, we discussed how developing a deliberate awareness of our digital body language can strengthen our security. This understanding of human behavior in digital spaces naturally leads us to our next critical topic: the human firewall. As we've seen, recognizing these patterns is the first step in building a strong and resilient human firewall—one that combines technical knowledge with human awareness to create truly effective security practices.