Protect Apps with Shield
Learning Objectives
After completing this unit, you’ll be able to:
- Explain how Shield protects business-critical apps.
- Describe Event Monitoring best practices.
Salesforce Shield
Salesforce Shield is a set of security products admins and developers can use to protect business-critical apps with enhanced encryption, event monitoring, historical data retention, and data classification capabilities. Shield allows you to build a new level of trust, transparency, compliance, and governance with simple point-and-click tools. Those tools include Platform Encryption, Event Monitoring, Field Audit Trail, and Data Detect.
As more customers use Salesforce to store personally identifiable information, including sensitive, confidential, or proprietary data, it’s critical to ensure the privacy and confidentiality of that data. The tools included in Shield allow you to meet both external and internal data compliance policies.
Platform Encryption
Platform Encryption is designed to let you retain critical app functionality—like search, workflow, and validation rules—so you maintain full control over encryption keys. You can set encrypted data permissions to protect sensitive data from unauthorized users. Platform encryption allows you to natively encrypt your most sensitive data at rest across all of your Salesforce apps.
Shield: Platform Encryption builds on the data encryption options that Salesforce offers out of the box. Data stored in many standard and custom fields, files, and attachments is encrypted using an advanced key derivation system based on a hardware security module. So, your data is protected even if other lines of defense have been compromised.
Your data encryption key material is never saved or shared across orgs. You can choose to have Salesforce generate key material for you, or upload your own key material. By default, the Shield Platform Encryption Key Management Service derives data encryption keys on demand from a primary secret and your org-specific key material, and stores that derived data encryption key in an encrypted key cache. You can also opt out of key derivation on a key-by-key basis or store your final data encryption key outside of Salesforce and have either the External Key Management service or the Cache-Only Key Service fetch it on demand from a key service you control. No matter how you choose to manage your keys, Shield Platform Encryption secures your key material at every stage of the encryption process.
Event Monitoring
Event Monitoring gives you access to detailed performance, security, and usage data on your Salesforce apps.
Event Monitoring is like a window that shows all the granular details of user activity in your organization. We refer to these user activities as events, which are captured in something called an event log. You can view information about individual events or track trends in events to identify abnormal behavior and safeguard your company’s data swiftly.
So, what are some of the events you can track? Event Monitoring provides tracking for many types of events, including:
- Who viewed what data and when
- Where data was accessed
- When a user makes a change to a record by using the UI
- Who is logging in and from where
- Who in your org is performing actions related to Platform Encryption administration
- Which admins logged in as another user and the actions the admin took as that use.
- How long it takes a Lightning page to load
All of these events are tracked and accessible via the API, so you can view them in the data visualization app of your choice. You can also see who is accessing critical business data, when, and from where. Event Monitoring data can be easily imported into any data visualization or application monitoring tool, such as Tableau, Einstein Analytics, Splunk, or New Relic. To learn more, see the Event Monitoring module which walks you through the process of setting up and monitoring your API connection..
Field Audit Trail
Field Audit Trail lets you know the state and value of your data for any date at any time. You can use it for regulatory compliance, internal governance, audits, or customer service.
Field Audit Trail lets you define a policy to retain archived field history data indefinitely from when the data was archived. This feature helps you comply with industry regulations related to audit capability and data retention.
You can use the Salesforce Metadata API to define a retention policy for your field history. You can enable tracking for specific fields and then use REST API, SOAP API, and Tooling API to work with your archived data.
When enabled, field history data is copied from the History-related list into theFieldHistoryArchive big object. To specify the Field Audit Trail retention policies for the objects you want to archive, you need to define a HistoryRetentionPolicy for your related history lists, such as Account History. Then, use the Metadata API to deploy the big object.
You can update the retention policy on an object as often as you like. Field Audit Trail allows you to track up to 60 fields per object in contrast to the 20 fields per object tracking that comes standard with Salesforce.
Field Audit Trail also allows you to retain archived field history data indefinitely. Without it, you can only retain archived data for 18 months.
Implementing Health Check and Shield into your Salesforce app development workflow helps you develop securely. Secure app development processes are the best way to protect your company and customer data.
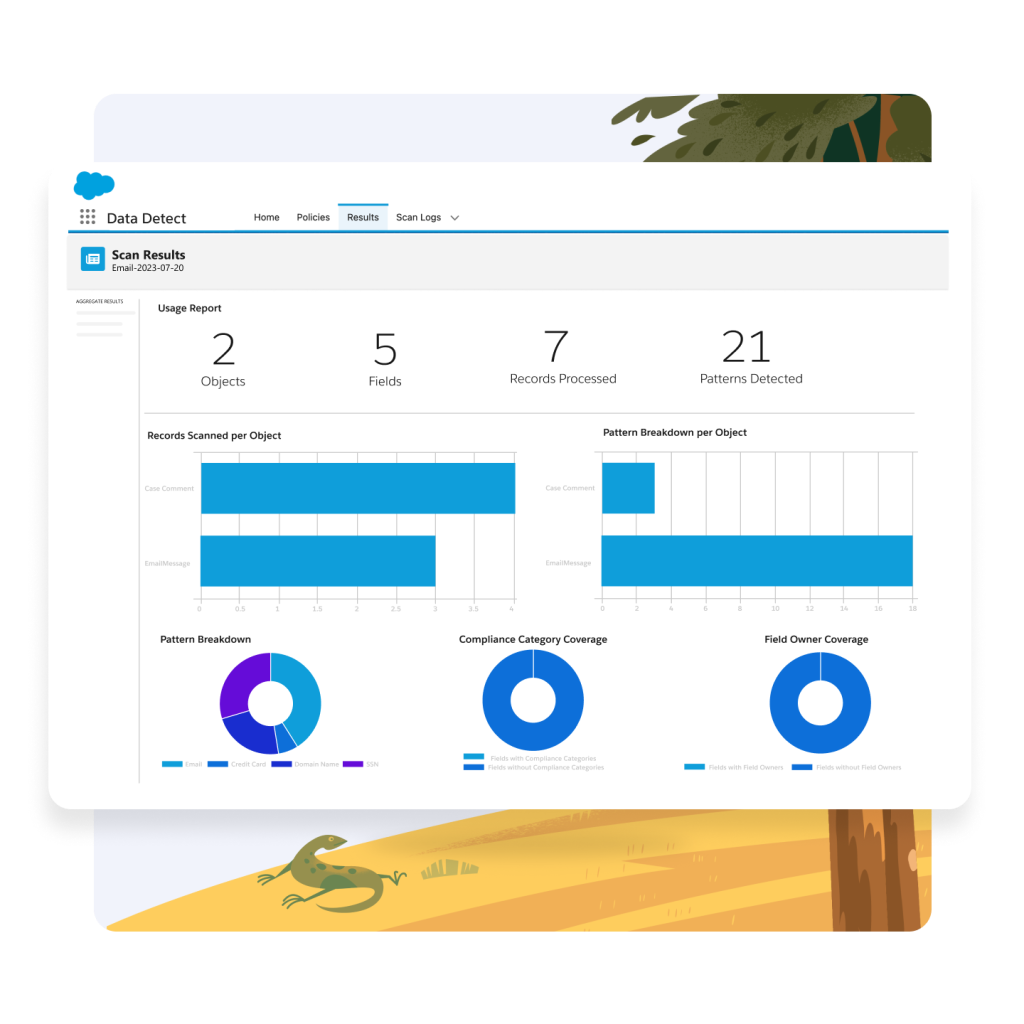
Data Detect
Data Detect allows you to quickly find sensitive data across your org and take appropriate actions to classify it. You can use Data Detect to define policies that categorize the types of information you consider sensitive, scan the data in your org and identify where critical data like credit card numbers and social security numbers are stored, and apply data classification categories from an intuitive UI. Pair Data Detect with other security and privacy features to comply with data protection laws and security best practices.
Upon identifying sensitive data, Data Detect enables you to explore matched patterns and gain a granular understanding of what type of data lives where. From there, you can swiftly take action to protect customer information by updating data classification tags. Using platform-native technology, Data Detect eliminates the need for third-party services or cloning your data outside of Salesforce for processing. Use Data Detect to expedite data categorization by aligning sensitivity levels and categories to actual field data.
Data Detect integrates seamlessly with native Salesforce software and identifies sensitive data regardless of what field it’s in, allowing you to take action to safeguard it quickly. Use a convenient UI to update data classifications as you discover and review fields containing sensitive data.
Data privacy and security laws mean you must ensure that certain PII or sensitive data is not exposed. As a Salesforce Shield product, Data Detect empowers you with the capability to discover sensitive information you might not even know exists, so you can take the necessary steps to protect it and maintain industry-specific and regulatory compliance.
Now you understand what tools are available to help you correctly configure and monitor the security settings in your Salesforce org(s). To learn how to start building applications with security in mind, see the Secure Client-Side Development module.
Resources
- Trailhead: Secure Your Apps with Salesforce Shield
- Salesforce Help: Salesforce Shield
- Salesforce Help: Field Audit Trail