Differentiate Between Inbound and Outbound Connections
Learning Objectives
After completing this unit, you’ll be able to:
- Name the Salesforce Private Connect components.
- Understand Private Connect use cases.
Basic Architecture
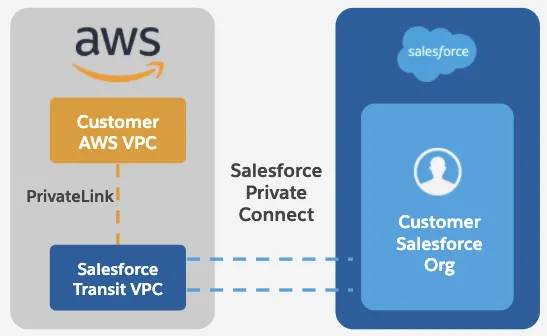
Now that you understand the broader advantages of Private Connect, let’s delve into the details of its architecture. First, to create a secure backbone with Salesforce first-party data centers, we created the cloud native interface (CNI) layer that can operate between various cloud environments. The CNI layer consists of several components, the most important one being virtual private clouds (VPCs).
VPCs are isolated sections of the larger AWS Cloud in which Salesforce hosts managed resources. They can also be referred to as Transit VPCs, as they act as proxies for HTTP/s traffic to flow through. For each supported AWS region, there is an inbound transit VPC and an outbound transit VPC.
First, customers connect their own VPCs to the Transit VPCs using an AWS feature called PrivateLink. Then, customers create a private connection in Salesforce to connect their orgs to the Transit VPCs. This results in a neat telephone line flowing all the way from your VPC to the Transit VPC and finally to your Salesforce org.
The private connection setup is done directly in the Salesforce Setup page. Under the Security node, there’s a new Setup user experience specifically for Private Connect. If you need to connect to multiple VPCs, you can create multiple private connections to do so.
You might be wondering what the differences between inbound and outbound VPCs are. Shouldn’t the setup be the same for both directionalities? Why can’t a single link allow traffic to flow both ways?
The simplified explanation is that sending traffic into Salesforce requires a different setup process than sending traffic out of Salesforce, even though some aspects are the same. The configuration requires that the receiving end of the connection be properly configured to accept and allow the incoming traffic to make sure that it’s coming from a verified source. Therefore, the configuration for an outbound connection, in which AWS is the receiving end, differs from the configuration of an inbound connection, in which Salesforce is the receiving end.
Inbound
Let’s talk about the inbound direction first. Suppose you have an enterprise resource management (ERP) software in AWS. When your company’s warehouse staff takes inventory in the ERP of a potential new product, you want them to be able to push those changes to Salesforce as soon as possible so that your sales team can sell that new product. This is where an inbound connection matters, as you want to call the Salesforce REST API from AWS to populate the products object. The HTTP/s traffic is sent securely through the inbound connection.
In your Amazon VPC, make sure that your org’s My Domain is mapped to the IP address of the endpoint in your VPC using Amazon Route53. Amazon Route53 is an AWS service that redirects VPC traffic to infrastructures outside of AWS, so any changes within your VPC that are sent through the registered endpoint are directed straight to your Salesforce org. You can then use existing Salesforce APIs, and the routing of the calls happens automatically.
Outbound
Let’s say you have a marketing app in AWS. In order to build the marketing campaign, you need account and contact data that’s stored in your Salesforce org. You can securely make a callout to an endpoint service running in AWS through the outbound connection to add members to the campaign.
To support this direction, Salesforce creates PrivateLink endpoints on behalf of the customer within the outbound transit VPC. The customer needs to grant access to their endpoint service running in their VPC using a provided IAM role. The IAM role is an AWS identity with permission policies that grants the Salesforce managed PrivateLink endpoint access to the PrivateLink endpoint service running in the customer VPC. Depending on how your endpoint service is configured, you may still need to accept the PrivateLink endpoint within the PrivateLink endpoint service before traffic can be sent through it.
Wrap Up
Salesforce has invested heavily with Amazon to bring to market purpose-built solutions between Amazon Web Services and the Salesforce platform. One of the key successes of our strategic partnership with AWS is to deliver a truly integrated solution for our customers. Salesforce Private Connect is the solution that keeps communications private by allowing for bidirectional connections between Salesforce and Amazon Web Services. Private Connect delivers on the partnership commitment to help customers find their fastest path from idea to impact.
Resources
- External Site: AWS PrivateLink
- External Site: Amazon VPC
- External Site: Amazon Route53
- External Site: AWS IAM Roles