Secure Your Users' Identity
Learning Objectives
After completing this module, you’ll be able to:
- Set up multi-factor authentication for your users.
- Use the Salesforce Authenticator app for MFA logins.
- Get login information about users who log in to your org.
Secure Account Access with Multi-Factor Authentication and Salesforce Authenticator
On their own, usernames and passwords aren’t sufficient protection against cyberthreats like phishing attacks. An effective way to enhance the security of your login process and protect your org's data is to require that users provide additional evidence to prove their identity when logging in. Security experts call this multi-factor authentication, or MFA for short. At Salesforce, we believe MFA is so important that we require it for everyone accessing our products and services. To learn about the MFA requirement, check out the Salesforce Multi-Factor Authentication FAQ.
What Is Multi-Factor Authentication?
Sounds like a mathematical equation, right? Whether math thrills you or fills you with dread, just know that MFA has nothing to do with high school algebra. It has everything to do with making sure that your users are who they say they are.
By the way, you may be more familiar with the terms two-factor authentication or 2FA. Not to worry! While 2FA is a subset of MFA, we’re effectively talking about the same thing.
So, what exactly are the multiple factors? They’re different types of evidence that users provide when logging in to confirm their identity.
- One factor is something users know. For Salesforce logins, that's a username and password combination.
- Other factors are verification methods that a user has in their possession, such as a mobile device with an authenticator app installed or a physical security key.

You might not have known what it’s called, but you’ve probably already used multi-factor authentication. Every time you get cash from the ATM, you use something you have (your bank card) plus something you know (your PIN).
Requiring another factor in addition to a username and password adds an extra, important layer of security for your org. Even if a user’s password is stolen, the odds are very low that an attacker can guess or impersonate a factor that a user physically possesses.
Sound cool? Let’s see how it works.
How Multi-Factor Authentication Works
MFA adds an extra step to your Salesforce login process.
- A user enters their username and password, as usual.
- Then the user is prompted to provide one of the verification methods that Salesforce supports.
You can allow any or all of these verification methods.
Salesforce Authenticator |
A free mobile app that integrates seamlessly into your login process. Users can quickly verify their identity via push notifications. We talk more about this app in a bit. |
Third-party TOTP authenticator apps |
Apps that generate unique, temporary verification codes that users type in when prompted. This code is sometimes called a time-based one-time password, or TOTP for short. Users can pick from a wide variety of options, including Google Authenticator, Microsoft Authenticator, or Authy. |
Security keys |
Small physical tokens that look like a thumb drive. Logging in with this option is fast and easy; users simply connect the key to their computer then press the key’s button to verify their identity. Users can use any key that’s compatible with the FIDO Universal Second Factor (U2F) or FIDO2 WebAuthn standards, such as Yubico’s YubiKey or Google’s Titan Security Key. |
Built-in authenticators |
Biometric readers, such as fingerprint or facial recognition scanners, that are built into a user’s device. In some cases, built-in authenticators can leverage a PIN or password that users set up on their device’s operating system. Common examples include Touch ID, Face ID, and Windows Hello. |
When Are Users Prompted for Multi-Factor Authentication?
Users are required to provide multiple factors every time they log in. As part of the Salesforce terms of service, all customers must use MFA for user interface logins. Doing so ensures every Salesforce org is protected with adequate security from the get-go.
To step up security even more, you can require MFA for additional circumstances.
- When users access Salesforce APIs. To learn about configuring MFA for API access, check out the help article Set Multi-Factor Authentication Login Requirements for API Access.
- When users access a connected app, dashboard, or report. This process is known as step-up or high-assurance authentication.
- During a custom login flow or within a custom app, for example, before reading a license agreement.
Your Options for Turning on MFA
As we mentioned earlier, Salesforce requires everyone to use MFA when logging in to a product’s UI. To help users with this requirement, MFA is a default part of the login process for Salesforce production orgs. Ordinarily you don’t need to take any special steps to turn it on.
That said, admins of a new production org can temporarily disable MFA if they need some time to educate their users about registering for, and logging in with, MFA. So it’s a good idea to know how to reenable MFA when everyone’s prepared. And you can easily turn on MFA for other types of orgs too, including sandboxes, developer orgs—even Trailhead Playgrounds!
Turning on MFA is as simple as selecting a checkbox in Setup. We show you how in just a little bit.
Verify That the Session Security Level Is Set for MFA
In most production orgs, the security level associated with the MFA login method is set up appropriately. But we recommend double-checking, just to be safe.
- From Setup, enter
Session Settingsin the Quick Find box, then select Session Settings.
- Under Session Security Levels, make sure that Multi-Factor Authentication is in the High Assurance category.
Now you’re ready to start your MFA journey.
Turn on MFA
Suppose you’re a Salesforce admin for Jedeye Technologies, a company not located in a galaxy far, far away. When Jedeye Technologies’s production org first launched, MFA was disabled to give Jedeye users a little time to get ready for logging in with it. Now your chief security officer has handed you a mission: It’s time for all employees to supply more than their username and password every time they log in to the company’s production org.
Oh, and a new employee, Sia Thripio, has just joined the company. Start out by creating a Salesforce user for Sia, and then enable MFA for Jedeye Technologies’s Salesforce org.
Ready to Get Hands-On?
Launch your Trailhead Playground now to follow along and try out the steps in this module. To open your Trailhead Playground, scroll down to the hands-on challenge and click Launch. You also use the playground when it's time to complete the hands-on challenges.
As we mentioned, you also need a mobile device running either Android or iOS to complete some of the tasks.
Step 1: Create a User
- From Setup, enter
Usersin the Quick Find box, then select Users.
- Click New User.
- For the first name and last name, enter
SiaandThripio, respectively.
- Enter your email address in the Email field. This setting is to get user notifications for Sia.
- Create a username for Sia and enter it in the Username field. It must be in email address format, but it doesn’t have to be a working email address. Make sure the email address is unique in your Trailhead Playground. You enter this username to log in as Sia later on, so we suggest making it short and easy to remember. Need ideas? Try using Sia's first initial, last name, and the current date, like this: SThripio.12202020@trailhead.com.
- Edit or accept the nickname value.
- For User License, select Salesforce Platform.
- For Profile, select Standard Platform User. While you’re here, deselect the options to receive Salesforce CRM content alerts. No need to clutter your inbox with unnecessary email from Salesforce.
- Make sure that Generate new password and notify user immediately is selected—it’s way down at the bottom of the page. Salesforce emails you about Sia’s new user because you entered your email address in the Email field.
- Click Save. Salesforce emails you a link to verify the user and set Sia’s password. Note: If you get an error that the username exists, create a user with a different name.
- Log in as Sia, and reset the password.
After you set the password, it’s time to enable MFA for Jedeye users.
Turn on MFA for Everyone in Your Org
You can quickly enable MFA for all users in an org with a single checkbox.
- From Setup, enter
Identityin the Quick Find box, then select Identity Verification.
- Select the Require multi-factor authentication (MFA) for all direct UI logins to your Salesforce org checkbox.

- Click Save.
Yep, that’s all it takes. Everyone in your org is now required to complete MFA when logging in. The next time users log in (including your new employee, Sia) they’re prompted to provide a verification method as a second factor, in addition to their Salesforce username and password.
At this point, you may have a burning question: What if some user accounts in my real-life org, such as test automation tool accounts, are exempt from the MFA requirement? Does the MFA setting affect them too?
It’s true that the MFA requirement from Salesforce doesn’t apply to some types of users. If you have any exempt users, there’s a user permission that you can apply to exclude them from MFA. To learn which user types are exempt and how to exclude them, see Exclude Exempt Users from MFA in Salesforce Help.
How Users Register Salesforce Authenticator for MFA Logins
Like making an unannounced visit to a city in the clouds, it’s a bad idea to require multi-factor authentication without helping your users get at least one verification method. You probably won’t get frozen and taken prisoner, but you might get lots of calls when you least want them, like when you’re watching an epic motion picture. Fortunately, Salesforce makes it easy for you to help your users. Just have them download an authenticator app onto their mobile device and connect it to their Salesforce account.
If users don’t download an app right away, it’s not a disaster. They’re automatically prompted to register a verification method for MFA when they log in.
Sia Thripio, your new employee, wants to use the Salesforce Authenticator mobile app so she can take advantage of the cool push notification feature for fast authentication. Let’s see how the registration and login process works. Get your Android or iOS mobile device and pretend it’s Sia’s phone. You’re going to download the Salesforce Authenticator app and connect it to Sia’s Salesforce account.
Heads up that you’ll be jumping back and forth between two devices in the following steps. When you’re on your PHONE, you’re working as Sia in the Salesforce Authenticator app. When you’re on your DESKTOP, you’re logged in as Sia in your Trailhead Playground in a web browser.
- PHONE: Download and install Salesforce Authenticator for iOS from the App Store or Salesforce Authenticator for Android from Google Play.
- PHONE: Tap the app icon to open Salesforce Authenticator.
- PHONE: In the app, page through the tour to learn how Salesforce Authenticator works.
- DESKTOP: If you’re still logged in to your Trailhead Playground as a system administrator, log out.
- DESKTOP: Use Sia’s username and password to log in.

- DESKTOP: Salesforce prompts you to connect Salesforce Authenticator to Sia’s account.
- PHONE: In Salesforce Authenticator, tap Connect Your Account. The app displays a two-word phrase.
- DESKTOP: Enter the phrase in the Two-Word Phrase field.
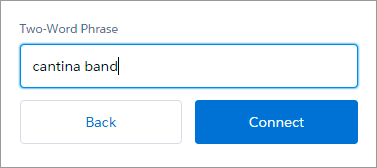
- DESKTOP: Click Connect.
- PHONE: Salesforce Authenticator shows details about Sia’s account: her username and the name of the service provider—in this case, Salesforce.

- PHONE: Tap Connect.
- DESKTOP: Sia has successfully registered Salesforce Authenticator and she’s logged in to her Salesforce account! She can go about her business.
Now, whenever Sia logs in to her Salesforce account, she gets a notification on her phone. She opens Salesforce Authenticator and checks the activity details. If everything looks right, she taps Approve and finishes logging in.
What if someone else tries to log in with Sia’s username and password? You guessed it—she gets a notification about that too, and can tell Salesforce Authenticator to deny the login request. Phew!
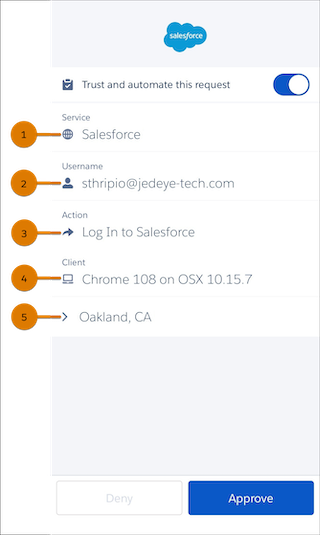
Let's take a closer look at the data Salesforce Authenticator keeps track of.
- The service the user is attempting to access. In addition to Salesforce, you can use Salesforce Authenticator with the LastPass password manager and other services that require stronger authentication.
- The user who’s trying to log in.
- The action that Salesforce Authenticator is verifying. Other actions could show up here if you set up even tighter security. For example, you can require authentication when someone tries to access a record or dashboard. This process is called “step up” authentication.
- Information about the browser or app from which the login attempt is taking place, including the device that’s being used.
- Where the phone is located.
Back Up Connected Accounts
Now that Sia’s account is connected to Salesforce Authenticator, she can enable account backups by verifying her email address. This way, she can restore her connected accounts if she changes or loses her mobile device.
- PHONE: In Salesforce Authenticator, tap the settings icon in the upper-left corner.
- PHONE: Tap the Back Up Accounts toggle switch.
- PHONE: Enter Sia’s (your) email address and tap Send Code so the app emails you a verification code.
- PHONE: Check Sia’s (your) email and enter the code in Salesforce Authenticator.
- PHONE: The app then prompts Sia to set a passcode. She can use this code if she ever needs to restore her connected accounts.
Verify That Salesforce Authenticator Can Send Notifications
Salesforce Authenticator makes MFA easy through the magic of push notifications. But Sia should make sure the app has permission to send these types of notifications!
- PHONE: In Salesforce Authenticator, tap the settings icon to go back to the settings page.
- PHONE: Make sure the Push Notifications section is set to Enabled. If not, tap Change in Settings to switch to the mobile device’s settings. From there, update Salesforce Authenticator’s permissions to allow notifications.
Automate the Authentication Process
Suppose Sia regularly logs in from the same place, such as the office, her home, or her favorite, dimly lit cantina. Tapping Approve on her phone could get old after a while. If she lets Salesforce Authenticator use her phone’s location services, she can tell the app to verify her activity automatically when it recognizes all the details. In other words, if she logs in from a particular spot using the same device and the same browser or app, she doesn’t even have to pull her phone out of her pocket. Salesforce Authenticator can handle MFA login challenges for her automatically!
Let’s try it out.
- DESKTOP: Log out of Sia’s account and then log in as Sia again.
- PHONE: At the prompt, select Trust and automate this request. And then tap Approve.
- Salesforce Authenticator saves those details as a trusted request.
- DESKTOP: Log out of Sia’s account and log in again. Voila! You’re not prompted for approval. Salesforce Authenticator recognizes that all the details match the trusted request you saved before. Access granted automatically!
Any time Sia tries to log in with a different browser or device, or from a new location, she can add the new details to the Salesforce Authenticator list of trusted requests. She can save as many trusted requests as she likes, including ones for other accounts and actions. To view the trusted requests for an account, Sia taps the arrow icon, which opens the account details page.

The account details page lists trusted requests and login activity history. Verified Activities shows how many times Salesforce Authenticator has verified Sia’s login to Salesforce. Automations shows how many times Salesforce Authenticator logged Sia in automatically with a trusted request.

What if Sia no longer trusts a request? Simple. She swipes left. She can clear all trusted requests at once by selecting  and then Remove All Trusted Requests.
and then Remove All Trusted Requests.
Sometimes an automated verification may not work, like when the data connection drops off. Not a problem. Sia just types in the TOTP code that Salesforce Authenticator displays.
Want to restrict users’ automated verifications to trusted IP addresses only, such as your corporate network? Or prevent them entirely? You can. When logged in as an admin, go to your org's Identity Verification Settings and change what’s allowed.

To learn the ins and outs of automation with Salesforce Authenticator, check out Salesforce Help: Automate Multi-Factor Authentication with Salesforce Authenticator and Optimize and Troubleshoot Automation in Salesforce Authenticator.
What Happens If Sia Loses Her Mobile Phone?
Good question. As you know, users crash or get marooned on desert planets and lose their phones. Happens all the time. If Sia loses her phone, gets a new one, or accidentally deletes Salesforce Authenticator, she has a few options. Sia can either restore her accounts from the backup she made earlier, or you can disconnect her account from Salesforce Authenticator and then she can reregister the app.
If Sia enabled account backups in her Salesforce Authenticator app, she’s in great shape. All she has to do is reinstall Salesforce Authenticator on her new phone. When she opens the app, she’ll see the option to restore her accounts from her backup. Sia enters the passcode she used when she backed up her accounts, and her accounts reappear on her phone.
What if Sia didn’t back up her accounts? Here’s what you can do to help.
- Log in as an administrator.
- From Setup, enter
Usersin the Quick Find box, then select Users.
- Click Sia’s name.
- On Sia’s user detail page, click Disconnect next to App Registration: Salesforce Authenticator.
The next time Sia logs in, if she doesn’t have another verification method connected, she’s prompted to connect Salesforce Authenticator again.
Monitor Who’s Logging In to Your Org
An important part of an admin’s job is to know who’s logging in to your org. That’s what Identity Verification History is for.
- Log in as the system administrator of your Trailhead Playground.
- From Setup, enter
Verificationin the Quick Find box, then select Identity Verification History.
Check out the Location column. It defaults to the user’s country, but you can get more detail by creating a custom view.

Congratulations, administrator! You’ve seen how easy it is for your users to set up and log in with MFA. We encourage you to explore other options for your MFA implementation, such as enabling security keys or built-in authenticators as alternative verification method options. Both of these options are a great choice if users don’t have a mobile device or if cell phones aren’t allowed on the premises. Now let’s learn how to get even more control over your login process in the next unit.
Resources
- Salesforce Help: Enable MFA for Direct User Logins
- Salesforce Help: Decide How Users Select a Verification Method During the Registration Process
- Salesforce Help: Salesforce Authenticator
- Salesforce Help: Requirements for Salesforce Authenticator (Versions 2 and 3)
- Salesforce Help: Register Salesforce Authenticator as an Identity Verification Method
- Salesforce Help: Register a Third-Party Authenticator app as an Identity Verification Method
- Salesforce Help: Enable U2F or WebAuthn Security Keys for Identity Verification
- Salesforce Help: Register a Security Key as an Identity Verification Method
- Salesforce Help: Enable Built-In Authenticators for Identity Verification
- Salesforce Help: Register a Built-In Authenticator for Identity Verification
- Salesforce Help: Custom Login Flows
- Salesforce Help: Monitor Identity Verification History
- Salesforce Help: Back Up Your Connected Accounts in the Salesforce Authenticator Mobile App
- Salesforce Help: Salesforce Multi-Factor Authentication FAQ
