Develop a Cybersecurity Maturity Plan
Learning Objectives
After completing this unit, you’ll be able to:
- Explain cybersecurity maturity.
- Develop a cybersecurity maturity plan.
In the previous unit we read about Zena and the challenges she faced after deciding to expand her family's artisanal soap business into the digital marketplace. In this unit we’re going to use a unique, community-based cybersecurity maturity model to help Zena respond to the cybersecurity risks she’s experiencing. But before we assist Zena, let’s review important concepts from the previous unit.
Knowledge Check
Ready to review what you’ve learned? The following knowledge check isn’t scored—it’s just an easy way to quiz yourself. To get started let’s review what you’ve learned by matching each statement in the left column to the corresponding aspect of inequity in the right column. When you finish matching all the items, click Submit to check your work. If you’d like to start over, click Reset.
The Community Cyber Security Maturity Model
The Center for Infrastructure Assurance & Security (CIAS), developed at the University of Texas at San Antonio, is a leading research center dedicated to enhancing the nation’s cybersecurity posture. The CIAS receives funding through grants from the Department of Defense (DoD) and the Department of Homeland Security (DHS) to support its research, outreach, and innovative cybersecurity initiatives.
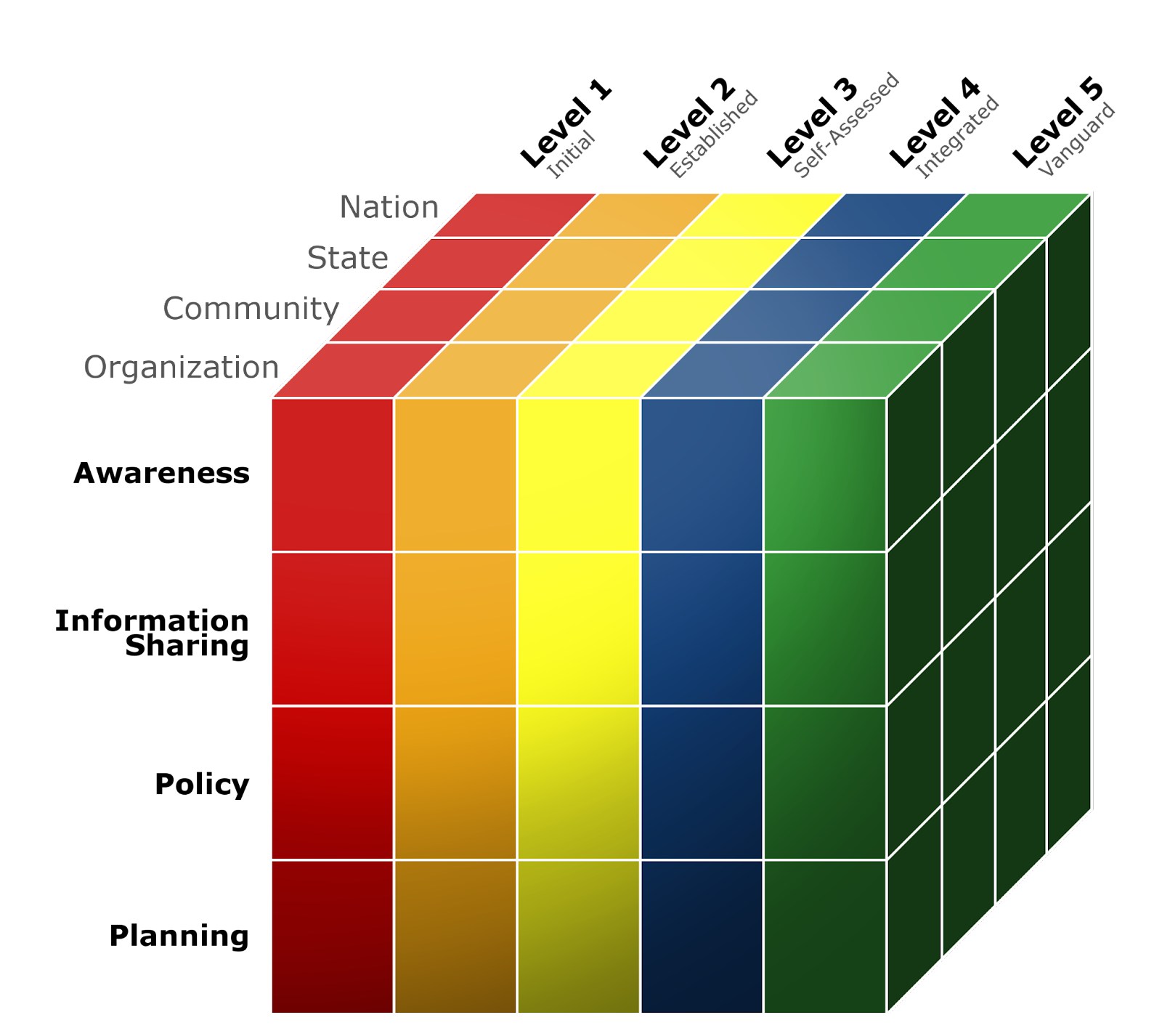
One of CIAS's notable contributions is the Community Cyber Security Maturity Model (CCSMM), a tool designed to enhance the cybersecurity stance of both communities and organizations, regardless of size. This model serves as a structured guide to:
- Evaluate and enhance cybersecurity measures in a systematic manner.
- Cater specifically to the distinct needs and challenges faced by communities and organizations.
- Emphasize the importance of teamwork, awareness, and actionable steps for continuous improvement in cybersecurity.
- Highlight that effective cybersecurity isn’t about expensive technology but about establishing strong, practical defenses.
© 2024 The Center for Infrastructure Assurance and Security. This work is licensed under a Creative Commons Attribution-NonCommercial 3.0 Unported License
The CCSMM outlines five progressive levels of cybersecurity maturity:
-
Level 1–Initial: Minimal awareness or action toward cybersecurity.
-
Level 2–Established: Recognition of cyberthreats and the need for cybersecurity measures.
-
Level 3–Self-Assessed: Active efforts to promote cybersecurity awareness and collaboration on training initiatives.
-
Level 4–Integrated: Comprehensive integration of cybersecurity practices into organizational processes.
-
Level 5–Vanguard: Prioritization of cybersecurity as a critical component of business strategy.
Organizations, communities, and others can determine where they stand by aligning their practices with the model’s dimensions on awareness, information sharing, policy, and planning.
Other Cybersecurity Maturity Models
Several cybersecurity maturity models exist alongside the CCSMM, each with its unique focus and approach. For example, the Cybersecurity Capability Maturity Model (C2M2) developed by the Department of Energy in collaboration with the Department of Homeland Security is designed to help organizations, particularly those in critical infrastructure sectors, evaluate and improve their cybersecurity programs and practices. The NIST Cybersecurity Framework provides guidelines on managing and reducing cybersecurity risk for organizations, emphasizing continuous improvement.
The ISO/IEC 27001 standard offers a systematic approach to managing sensitive company information so that it remains secure. The Australian Cyber Security Centre (ACSC) Essential Eight outlines eight critical mitigation strategies to protect systems from cyberattacks, and offers maturity levels for their implementation. Finally, the European Union Agency for Cybersecurity (ENISA) Computer Security Incident Response Teams (CSIRT) Maturity Framework provides recommendations to CSIRTS on how to improve, become more mature and be better prepared to protect their constituencies.
While these models offer valuable guidelines and are often sector-specific or focus on organizational risk management and continuous improvement, the Community Cyber Security Maturity Model distinguishes itself with its broad, community-centric approach.
How the CCSMM Addresses Inequity Risk Factors
You’ll recognize the following table from unit 1, but with an additional column describing how the CCSMM addresses each risk factor.
|
Risk Factor
|
How the CCSMM Addresses It
|
|---|---|
Digital divide |
Limited access to technology: Raises awareness, encourages resource sharing, and tailors solutions through community assessments. Digital literacy deficit: Provides free resources, promotes partnerships for subsidized solutions, and advocates for affordable internet access. |
Economic constraints |
Cost of cybersecurity: Emphasizes free tools, supports partnerships for subsidies, and advocates for broader policy changes. It also addresses competing priorities by highlighting long-term benefits, connecting cybersecurity to broader business and community goals, and advocating for targeted funding programs. |
Infrastructure and resources |
Lack of skilled workforce: Fosters local expertise through collaboration, supports training programs, and encourages local innovation. Weak regulatory frameworks: Advocates for inclusive policies that consider diverse cultural perspectives and privacy values. |
Cultural and social factors |
Low awareness of cyber threats: Delivers culturally relevant awareness campaigns and builds trust through partnerships with trusted organizations. Cultural norms: Raises awareness about responsible online behavior, addresses specific cultural concerns through partnerships, and advocates for inclusive policies. |
The CCSMM is a flexible framework. By adapting its principles and collaborating with relevant stakeholders, communities can use it to address specific inequities and build a more inclusive and secure digital landscape for all.
Create a Cybersecurity Maturity Plan
Zena’s story illustrates the struggles many small businesses, especially those from underserved communities, face in navigating the digital landscape while vulnerable to cyber inequity. Let’s use the CCSMM as a roadmap to help Zena build resilience and secure her online business beginning from her current level of knowledge and skill.
Initial Level
Focus: To acknowledge cybersecurity as a critical aspect of her business by building her essential awareness and basic security measures.
|
Zena’s Actions
|
Resources
|
|---|---|
Assessment: Complete a cybersecurity assessment to understand gaps in digital and cyber practices |
CIS Controls Self Assessment Tool: Free assessment to improve cyberdefense regardless of organization size or resources. |
Basic digital literacy: Take online courses or workshops to understand technology along with online safety practices and common threats. |
National Cyber Security Alliance: Offers free online courses and resources. Google Digital Garage: Free online training on various digital skills, including online safety. Cybersecurity Career Path: Offers a variety of free online cybersecurity modules. Mobile-friendly websites: Access websites designed for smaller screens, which usually load faster on slower connections. Text-based resources: Access guides, articles, and tutorials at community centers or local libraries. |
Password hygiene: Create strong and unique passwords for all accounts and enable two-factor authentication wherever possible. |
Password manager (for example, LastPass, Google Password Manager): Free password manager for creating and storing strong passwords. Authenticator apps (for example Authy, Duo Mobile, Google Authenticator): Free authenticator to add an extra layer of protection like two-factor or multifactor authentication. |
Antivirus and anti-malware: Install a reputable security software on her computer and mobile devices. |
Microsoft Defender: Free antivirus software preinstalled on Windows 10 and 11. MacOS Antivirus: Antivirus option for Mac users. |
Data backups: Regularly back up critical business data to an external hard drive or cloud storage. |
Google Drive: Free cloud storage with up to 15 GB. External hard drive: Physical storage device for additional backup |
Established Level
Focus: To begin formalizing cybersecurity efforts by implementing core security practices and collaborating with the community.
|
Zena’s Actions
|
Resources
|
|---|---|
Secure website: Upgrade her ecommerce platform with security plugins and explore website security offerings by her hosting provider. |
Wordfence Security: Free security plugin for WordPress websites. Cloudflare: Free website security and performance tool. |
Community collaboration: Attend local tech support groups or forums to connect with other small businesses and share experiences. |
International Telecommunication Union (ITU): Provides global resources and programs related to cybersecurity capacity building and awareness. LinkedIn: Provides connections with other small businesses in related areas for networking on cyber practices. |
Local resources: Explore free or low-cost cybersecurity resources offered by libraries, community centers, or government initiatives. |
CISA Cyber Essentials Toolkit: Free resources and tools for building cybersecurity awareness. GCA Cybersecurity Toolkit: Free tools to reduce cyber risk. |
Basic security policies: Create basic policies for password management, data access, and incident response. |
SANS Security Policy Templates: Offers sample security policies for small businesses. CIS Policy Templates: Free policy templates for basic cyberhygiene. Cybersecurity industry regulations: Consult with local government bodies, legal experts, industry associations, and official government websites to understand and manage risks according to specific cybersecurity industry regulations. |
Self-Assessed Level
Focus: To enhance cybersecurity resilience by partnering with the community, conducting regular assessments, and refining security practices based on identified gaps.
|
Zena’s Actions
|
Resources
|
|---|---|
Assess online presence: Work with a community resource to conduct a vulnerability scan of her website to identify potential weak spots. |
PenTest Tools: Free website vulnerability scanner with recommended mitigations. Qualys Free SSL Labs: Free website security checker. ImmuniWeb: Free website security and privacy checker. |
Review assessment: Revisit the initial assessment to document progress against identified vulnerabilities. |
The initial assessment (see Initial Level). |
Seek feedback: Ask trusted customers or community members for feedback on the website's security features and privacy practices that have been implemented so far. |
Customers, family, and friends (for example, Do they receive errors or warnings related to the site’s security certificate? Are the password requirements unclear or overly complex?). |
Adapt and improve: Based on assessments and feedback work with a community resource to update security measures and address identified gaps. |
Revisit the previous levels to address identified gaps. |
Integrated Level
Focus: To become an active cybersecurity collaborator by continuously improving security, integrating it into all business processes.
|
Zena’s Actions
|
Resources
|
|---|---|
Invest in training: Attend basic cybersecurity workshops or webinars to enhance knowledge. |
Cybersecurity Career Path: Offers a variety of free online cybersecurity modules. NIST Online Learning Content: Offers free and low-cost cybersecurity training. Global Cyber Alliance Learning Portal: Access a library of free training courses and guided resources for small businesses. Cyber Readiness Institute: Sign up and complete this free program to strengthen security against cyberthreats. |
Consider professional help: Consult with a cybersecurity professional for a more comprehensive assessment and tailored recommendations. |
CISA International: Offers free and readily available services, tools, and resources |
Data sensitivity: Identify and classify sensitive customer data to implement appropriate security controls. |
Data Classification Guidance: Helps identify and classify sensitive data. Cybersecurity Framework (CSF): Develop processes to identify, classify, securely handle, retain, and dispose of data. |
Incident response plan: Create a basic plan outlining steps to take in case of a security breach. |
Incident Response Plan Templates: Easy to follow template to create a personalized incident response plan. Business Continuity Plan: A comprehensive, step-by-step plan to equip you to quickly respond, resolve, and learn from a cyber incident. |
Vanguard Level
Focus: Pioneer innovative community-based cybersecurity solutions by advancing cybersecurity within the community and possibly beyond.
|
Zena’s Actions
|
Resources
|
|---|---|
Mentor others: Share knowledge and experience with other small businesses in the community. |
Local Meetups or Events: Look for cybersecurity meetups or events in your community to connect with other small businesses and share knowledge. |
Advocate for change: Support initiatives that promote digital equity and address cyber inequities within and outside the community. |
Internet Society (ISOC): Join advocacy efforts and contribute to policy discussions on digital equity and cybersecurity globally. |
Stay informed: Continuously follow cybersecurity news and updates to adapt her practices to evolving threats. |
National Cyber Security Alliance (NCSA) Daily News Wire:Get daily updates on the latest cybersecurity threats and vulnerabilities. Reuters:Read expert insights and analysis on emerging cybersecurity trends and challenges. |
Invest in advanced solutions: As business grows, explore advanced security solutions based on professional recommendations. |
International Organization for Standardization (ISO): Explore international cybersecurity standards like ISO 27001 to guide the selection of advanced solutions. Cloud Security Alliance (CSA): Leverage cloud security best practices and certifications to evaluate and choose secure cloud-based solutions. |
Using the Community Cyber Security Maturity Model as a roadmap, Zena is successfully moving toward cybersecurity maturity. Each level provides achievable steps she can take within her existing knowledge and skill level. At each level, the emphasis is on increasing the depth and breadth of collaboration and integration with the community to enhance cybersecurity resilience for the individual business, and for the community as a whole.
As Zena’s business grows, this model encourages her to tap into community resources and build partnerships. This allows her to access skilled support and higher levels of maturity evident as:
- Integrating cybersecurity into all business decisions and processes
- Rapidly containing and recovering from security incidents
- Providing regular training and awareness to her staff
- Actively participating and leading in community cybersecurity
This comprehensive approach not only protects Zena’s business but also inspires others to prioritize cybersecurity within their businesses and communities.
Building a More Equitable Digital and Cyber Landscape
As you’ve seen here, digital and cyber inequity are not just technical problems; they’re social and economic issues with far-reaching consequences. Recognizing some of the root causes of inequity—limited access, digital literacy gaps, economic constraints, and infrastructure limitations—is the first step in creating a more equitable cyber landscape.
The CCSMM framework, while not designed to solely address inequity, offers a solid foundation for building resilience and improving cybersecurity posture. By adapting its principles and collaborating with relevant stakeholders, communities can use it to address specific inequities and empower individuals and organizations regardless of their resources or background.
Remember, progress, not perfection, is key. Small steps, whether it’s attending a local workshop, sharing resources with neighbors, or advocating for better policies, all contribute to the bigger picture. By working together, we can bridge the digital divide, enhance cybersecurity awareness, and create a secure and inclusive online environment for everyone.
Resources
- External Site: Humanities and Social Sciences Communications: Beyond structural inequality: a socio-technical approach to the digital divide in the platform environment
- External Site: Security Journal: Effects of socioeconomic and digital inequalities on cybersecurity in a developing country
- PDF: IEEEAccess: Cyber Security Maturity Assessment Framework for Technology Startups: A Systematic Literature Review
- External Site: Global Cyber Alliance (GCA): The GCA Cybersecurity Toolkit for Small Business
- External Site: Center for Infrastructure Assurance and Security (CIAS): Research
- External Site: CIAS: The Community Cyber Security Maturity Model
- Trailhead: Cybersecurity Risk Protection During Key Events
- Trailhead: The Center for Internet Security Critical Security Controls
- Trailhead: Cyber Resilience Program Development