Build Your Cyber Resilience Program
Learning Objectives
After completing this unit, you’ll be able to:
- Explain the Cyber Resilience Framework.
- Create a cyber resilience program.
The Cyber Resilience Framework
“Organizations need to work more closely with ecosystem partners and other third parties to make cybersecurity part of an organization’s ecosystem DNA, so they can be resilient and promote customer trust.” —Julie Sweet, Chair and CEO, Accenture
How does one build a cyber resilience program? The Cyber Resilience Framework is a good place to start. In collaboration with the Cyber Resilience Index working group and Accenture, the World Economic Forum Centre for Cybersecurity developed the Cyber Resilience Framework (CRF), a guide for building holistic cyber resilience in an organization. The Cyber Resilience Index (CRI) is an accompanying tool to help organizations quantitatively determine their cyber resilience using measures of performance against best practice.
The CRF serves as a standard, industry-agnostic framework with defined outcomes that can serve as a baseline to all organizations, regardless of geography or size. The CRF consists of the following six key principles.
- Principle 1: Regularly assess and prioritize cyber risk.
- Principle 2: Establish and maintain core security fundamentals.
- Principle 3: Incorporate cyber-resilience governance into business strategy.
- Principle 4: Encourage systemic resilience and collaboration.
- Principle 5: Ensure design supports cyber resilience.
- Principle 6: Cultivate a culture of resilience.
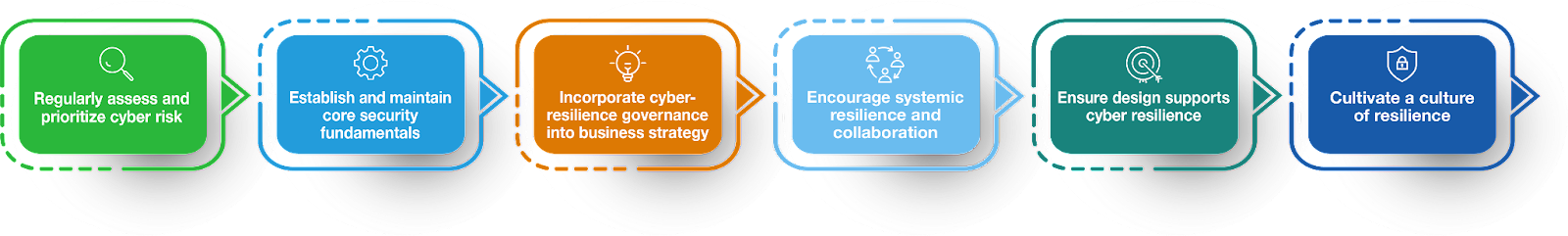
Each of the CRF principles is accompanied by a set of practices and sub-practices to further enable cyber leaders to develop and assess their cyber resilience.
According to the report, only 19% of cyber leaders are confident in the cyber resilience of their organizations. Such a low percentage is likely influenced by the following four key challenges to organizational cyber resilience, as identified by the working group.
- Overemphasis on security response and recover
- Undefined criteria for complete cyber resilience
- Difficulties in measuring and expressing the value of cyber resilience
- Transparency issues regarding cyber-resilience gaps and disruptive events
Addressing the crisis of confidence among cyber leaders requires a multifaceted approach, but implementing robust cyber-resilient governance can be the linchpin. Cyber-resilient governance refers to the management and oversight of an organization's cyber security efforts, with the goal of achieving a state of resilience in the face of cyber threats. This includes the development of policies, procedures, and controls to protect against cyberattacks, and the ability to quickly detect and respond to incidents when they occur.
The key activities to implement cyber-resilient governance include:
-
Cyber resilience strategy: Building a comprehensive strategy that establishes the capacity (for example, budget, staff) to manage all aspects of cyber risk for the organization’s critical assets.
-
Cyber resilience design: Appointing the appropriate leadership to oversee resilience efforts and identifying a reputable cybersecurity framework to protect critical assets.
-
Cyber resilience operation: Collaborating with business unit leaders to implement and test controls (administrative, operational, and technical), refine controls, and regularly update and advise decision makers.
-
Cyber resilience evolution: Maturing cyber-resilience culture by documenting lessons learned, sharing best practices, and modifying policies, procedures, awareness training, design and strategy when necessary.
Cyber-resilient governance is an ongoing process that requires constant attention, monitoring, and adaptation in order to effectively protect an organization from cyber threats. A governance structure is integral in creating a cyber resilience program that can circumvent these key challenges. Here are recommendations on how businesses overcome these challenges.
Strategy |
Challenge |
Solution |
|---|---|---|
|
Proactive defense and preparation
|
Overemphasis on security response and recovery |
Regularly update threat intelligence, employ predictive analytics, and invest in proactive monitoring tools. While response and recovery are essential, they should be components of a larger, holistic strategy. |
|
Develop clear guidelines and benchmarks
|
Undefined criteria for complete cyber resilience |
Define and document what cyber resilience means for your organization. This should include benchmarks, KPIs, and tangible goals. Make sure to cover aspects like system availability, data integrity, and business continuity. |
|
Demonstrate value through metrics
|
Difficulties in measuring and expressing the value of cyber resilience |
Establish clear metrics to measure cyber resilience. This could include visual aids like dashboards that clearly demonstrate metrics like downtime reduction and cost savings from avoided breaches. |
|
Foster a culture of openness
|
Hesitation in being transparent about resilience gaps and disruptive events |
Establish regular communication channels, like internal newsletters or meetings, where cyber incidents, gaps, and improvements are discussed. |
By addressing the challenges head-on, businesses are more likely to create a robust and effective cyber resilience program.
Build a Cyber Resilience Program
“You have the power, the capacity, and the responsibility to strengthen the cybersecurity and resilience of the critical services and technologies on which Americans rely.” —Statement by President Biden on [U.S.] Cybersecurity
Now that you’ve been introduced to the cyber resilience framework and ways to address challenges to cyber resilience, using the CRF as a guide, let’s use a scenario to build a cyber resilience program.
Scenario
With an expanding client base and increasing reliance on digital operations, the CEO of TechNova Industries, a midsize tech company with 2,000 employees, has recognized the need to fortify its digital infrastructure by developing a comprehensive cyber resilience program. The CEO appoints the CISO to lead the planning and implementation.
Below are the key steps taken by the CISO, and appointed team members, to begin a successful program.
- Pre-assess the current state: Perform a preliminary assessment of the organization’s current cybersecurity posture to identify existing gaps and vulnerabilities.
- Develop a plan: Outline a plan that includes timelines, milestones, responsibilities, and alignment with business objectives.
- Engage stakeholders: Engage key stakeholders across the organization to ensure alignment with business strategies and to garner support.
- Create a progress plan: Regularly report back to the CEO and other stakeholders on the progress of the program, including any key findings or obstacles.
These preliminary steps lay the groundwork for the next, more detailed steps to guide you in creating a cyber resilience program that will enhance your organization’s defenses while leading to a more resilient and secure environment.
Step 1:Regularly assess and prioritize cyber risk.
- Risk assessment: The IT department, in collaboration with an external cybersecurity consultant, undertakes a thorough analysis to pinpoint potential vulnerabilities and threats.
- Risk prioritization: The Risk Management team categorizes the identified risks based on potential impacts and prioritizes them.
- Update regularly: The Chief Technology Officer (CTO) schedules quarterly review meetings to keep the risk assessments updated.
Step 2. Establish and maintain core security fundamentals.
- Identify core functions: Department heads provide insights on mission-critical functions and related systems.
- Basic cyberhygiene: The IT department mandates regular software updates, backups for critical systems, strong password policies, and multi-factor authentication across all systems.
- Incident response plan: A cross-functional team, led by the CISO, develops a response plan for potential cyberattacks.
Step 3.Incorporate cyber-resilience governance into business strategy.
- Governance structure: The CEO establishes a Cybersecurity Committee that includes leaders from various departments.
- Strategic alignment: The Strategy team integrates cyber resilience objectives into the company's overarching strategy.
- Regular reporting: The CISO ensures monthly reports on cybersecurity measures are sent to the board and relevant stakeholders.
Step 4. Encourage systemic resilience and collaboration.
- Map interdependencies: The IT team collaborates with the Procurement and Sales departments to map third-party connections.
- Collaboration forums: TechNova Industries joins industry-specific cybersecurity forums to exchange knowledge.
- Joint exercises: The IT department organizes bi-annual cybersecurity drills in collaboration with their major partners and vendors.
Step 5. Ensure design supports cyber resilience.
- Flexible architecture: The IT team and external consultants redesign the existing system architecture to allow more flexibility and agility.
- Feedback loops: An internal portal is set up where employees can provide feedback on cyber resilience measures.
- Regular Reviews: Departmental heads and the IT department conduct semi-annual reviews of IT systems and processes.
Step 6. Cultivate a culture of resilience.
- Training and awareness: HR schedules quarterly cybersecurity awareness sessions for all employees.
- Reward and recognize: The leadership introduces a Cyber Champion of the Month award for active participation in resilience initiatives.
- Open communication: A confidential whistleblower policy is implemented where employees can anonymously report cyber concerns.
In a world increasingly vulnerable to cyberthreats, building a robust cyber resilience program is paramount. Real-world examples and tools such as a RACI chart and a self-assessment survey offer actionable guidance to begin to build your program.
Cyber resilience is not just about recovery; it’s about proactive defense, business alignment, and adaptability. This module provides a foundational roadmap to navigate the complex challenges and invest in resilience to safeguard the integrity and future of your organization.
Sum It Up
In this module, you’ve explored insights into the importance and principles of cyber resilience, distinguished it from traditional cybersecurity measures, and taken practical steps to develop a cybersecurity resilience program for your organization.
Interested in learning more about cybersecurity roles and hearing from security professionals? Check out the Cybersecurity Career Path on Trailhead.
Resources
- External Site: Journal of Cybersecurity: Development of a New Human Cyber-Resilience Scale
- External Site: NIST: Developing Cyber-Resilient Systems: A Systems Security Engineering Approach
- External Site: World Economic Forum: The Cyber Resilience Index: Advancing Organizational Cyber Resilience