Get Acquainted with Salesforce's Critical Incident Response
Learning Objectives
After completing this unit, you’ll be able to:
- Describe at a high level how Salesforce responds to critical incidents.
- Outline where you can find critical incident information.
- Explain how to sign up for critical incident webinars and Trust notifications.
- Update your admin contact information to ensure you receive important notifications.
About the Salesforce Critical Incident Center
Now that you know all about critical incidents, it’s time to learn about how the Salesforce Critical Incident Center responds to them.
The Critical Incident Center team is highly specialized and composed of professionals whose job is to serve as incident commanders during critical incidents. They are well-trained and experienced. They’re skilled organizers, communicators, and collaborators who swarm incidents moments after they are declared to engage all departments and decision-makers from Engineering, Support, Legal, Accounts, Public Relations, Security, Executives, and so on, to ensure a quick, holistic response.
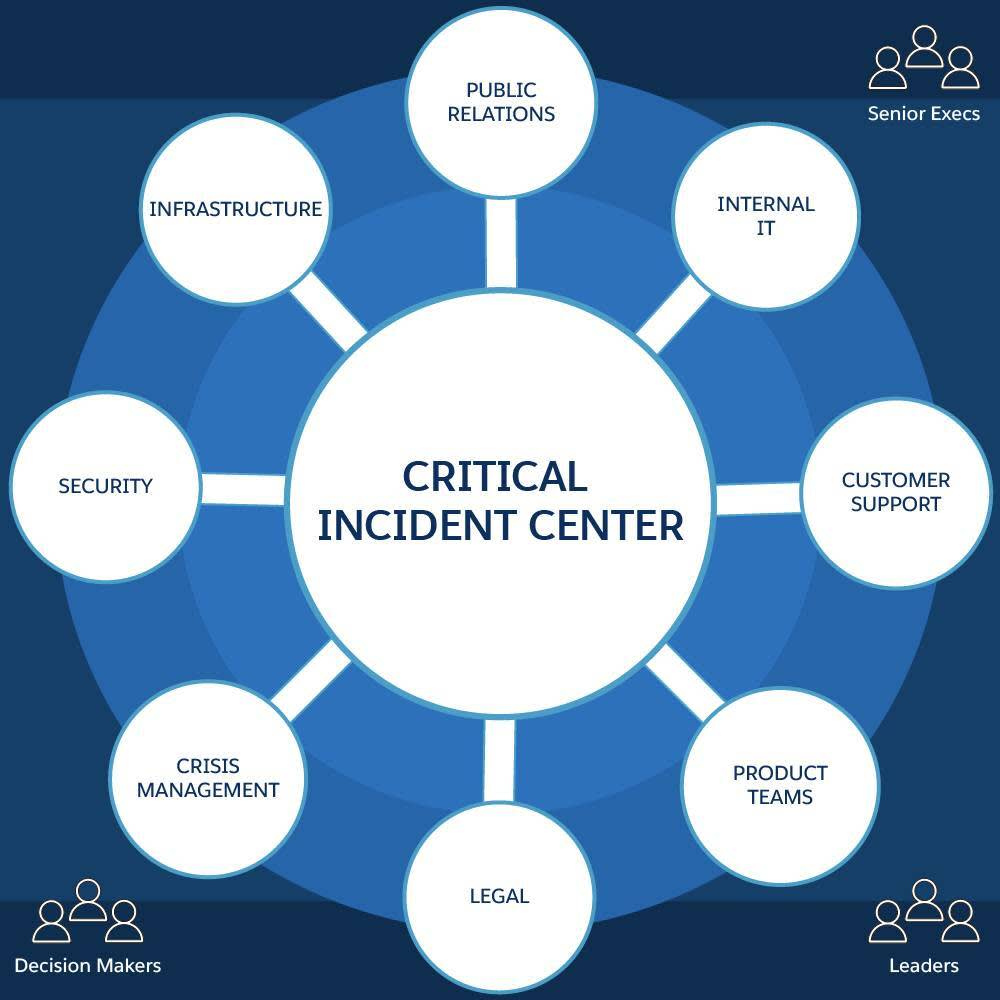
Key CIC Responsibilities
- Be the central point for all stakeholders during critical incidents.
- Lead the incident response until service is restored to Salesforce products and platforms.
- Manage the communications between the teams actively resolving an incident.
- Assemble additional teams and resources to drive incident resolution.
- Communicate with customers and partners through email and webinars.
- Lead communication internally for customer-facing teams, executives, and other Salesforce employees throughout an incident.
- Act as the voice of the customer to protect Trust and promote transparency during an incident.
Specialist Teams for Different Services
In simple terms, the Critical Incident Center ensures the correct teams are engaged to restore service and to ensure all parties are informed. This requires specialists with specific focus areas. Our services can be broken down into three areas. Depending on the critical incident category, members execute different plays detailed in the playbook.

1. Severity 1 Escalations (one customer affected)
- Drive service restoration of customer-reported or proactively identified incidents.
- Ensure the appropriate resources are engaged, and the executives and account teams are kept informed.

2. Severity 1 and 2 Incidents (more than one customer affected)
- Notify staff of the incident, specifically customer-facing teams and executives.
- Drive service restoration of incidents by ensuring the appropriate resources are engaged.
- Coordinate executive outreaches when required.

3. Severity 0 Incidents (Unified Command)
- Host the unified command bridge, providing a call to action for our business leaders where the high-level incident response is orchestrated.
- Notify customers of the incident, follow up with webinar invitations, and an incident closure notification.
- Host live customer webinars to share incident updates.
- Notify staff of the incident, specifically customer-facing teams and executives.
- Drive service restoration of incidents by ensuring the appropriate resources are engaged.
- Coordinate executive outreaches when required.
Unified Command for Severity 0 Responses
Our unified command service is our “secret sauce” when responding to incidents affecting multiple Salesforce customers. It is the unique leadership function of our corporate incident response. This is a formal, practiced top-level incident command that brings key stakeholders and business leaders needed to lead and direct service restoration of a Sev0 critical incident.
The goals of unified command are as follows.
- Improve the information flow between the teams involved.
- Develop a single collective approach to the management of the incident.
- Optimize the efforts of all teams.
- Reduce or eliminate duplications of effort.

Unified Command Bridge
The unified command bridge is a communications bridge running in parallel to technical bridges and it is where the unified command service is executed. For example, even before some incidents become Sev0, a unified commander discusses the incident with engineering teams to assess customer impact and whether it should be escalated to Sev0. If it is escalated to Sev0, the unified command bridge is launched to bring leaders from across the organization together to collectively restore service as quickly as possible.
Unified command provides high-level coordination for the customer-facing and technical teams, ensuring they have the resources and information they need to get the incident resolved. The bridge runs like a well-oiled machine, due to regular companywide exercises that ensure that all responses are practiced and current.

Critical Incident Drills
“By failing to prepare, you are preparing to fail.” —Benjamin Franklin
Drills and skills assessments focused on muscle memory are the core tenet of our competency model. A trained mind requires numerous hours of correct practice to ensure that plays are executed effortlessly when needed. Weekly exercises and monthly drills help teams deliver the most appropriate and effective, repeatable incident response. They also help identify process gaps and improvement opportunities. These drills are managed and graded so effectiveness and improvements can be measured.
Incident Communications

Similar to how you must go to the right channel or streaming service before you can binge your favorite show, Salesforce provides you with information on different channels during an incident. Updates are pushed through some channels, while other channels allow you to pull information as you need it. Familiarizing yourself with the channels now enables you to quickly locate the information you need during a fast-moving incident.

What Information Is on Which Channel?
Customers and partners can find out about critical incidents through these channels.
Channel |
Type of Content |
Details & Update Schedule |
|---|---|---|
Salesforce Trust (trust.salesforce.com) |
Updates for critical incidents that affect more than one customer |
The one-stop-shop to check the status of incidents impacting your orgs or platforms. Salesforce Trust is updated approximately every 30 minutes during an incident. Sign up for Salesforce Trust notifications so you can stay informed. (See below for details.) |
Email* |
Critical incidents—initial notification |
An incident notification is sent to potentially affected customers as soon as an incident is confirmed. |
Email* |
Critical incidents—webinar invitation |
An invitation is sent to potentially affected customers within 30 minutes to attend a webinar where a senior technical subject matter expert who is working on the incident provides an incident update and answers questions. |
Email* |
Critical incidents—final customer notification |
A service restoration notification is sent to potentially affected customers as soon as service has been restored. |
Customer webinars |
Critical incidents—customer webinar |
The customer webinar will be launched within 30 minutes and will be repeated periodically until the incident is resolved. |
*Trust notification emails are sent to subscribers. (See below for details).
**Incident notification emails and webinar invitations are only sent to the email addresses of Salesforce org admins. (See below for details).

Here are your self-service sources of information.
- The Salesforce Trust website where you can see the current and historic status of all our products. It is also your go-to location for product security and compliance information.
- Knowledgebase articles.
- The Salesforce Help website.

How to Stay Informed During Incidents
Here are two important things you should do to make sure that you can stay informed during Salesforce critical incidents.
-
Update admin contact details—Update your admin contact details to ensure the correct people in your org receive incident email notifications and webinar invitations.
-
Subscribe to Trust notifications—Navigate to the subscriptions page of the Trust site (link below) and subscribe to notifications for the instances that host your services. If you don’t know your instance name(s), refer to the Knowledge Article below to find it.
Hopefully, you’ve now got a better understanding of what a critical incident response team does, so in the next unit, we’ll show you how to create your own.
Resources
-
Website: Salesforce Trust home page
-
Website: Salesforce Trust status page (includes links to the status page for all our products)
-
Website: Salesforce Trust subscriptions page (to sign up for notifications)
-
Website: Salesforce Trust security page (to find security-related information)
-
Website: Salesforce Trust compliance page (to find Certifications, Standards, and Regulations related information)
-
Knowledge Article: View instance information for your Salesforce Organization
