Provide Authorization for External API Gateways
Learning Objectives
- Describe OpenID Connect dynamic client registration and token introspection.
- Describe how Salesforce uses connected apps to provide authorization for external API gateways.
OpenID Connect Dynamic Client Registration and Token Introspection
In the first unit, we talked about the use case in which Salesforce can act as an independent OAuth authorization server to protect resources hosted on an external API gateway. This connected app use case is enabled by OpenID Connect dynamic client registration and token introspection.
Dynamic client registration enables resource servers to dynamically create client apps as connected apps. The client apps are external applications requesting access to the protected resources. To dynamically create client apps as connected apps, the resource server sends the authorization server a request to create a connected app for the client app. The authorization server verifies the resource server’s request and creates the connected app, giving it a unique client ID and client secret.
Token introspection allows all OAuth connected apps to check the current state of an OAuth 2.0 access or refresh token. The resource server or connected apps send the client app’s client ID and secret to the authorization server, initiating an OAuth authorization flow. As part of this flow, the authorization server validates (or introspects) the client app’s access token. If the access token is current and valid, the client app is granted access.
How External API Gateway Authorization Flows
OpenID Connect dynamic client registration and token introspection might seem a bit complex. So let’s walk through its flow using the following example.
You want your Salesforce partners to be able to access order status data independently. So you build a service that exposes order status across multiple systems by fronting it with an API gateway, which is deployed on MuleSoft’s Anypoint Platform. To enable protected access to this data, you take the following steps.
- Apply an OpenID token enforcement policy on the API gateway.
- Configure Salesforce as a client management provider on Mulesoft’s Anypoint Platform.
With this configuration, the API gateway uses Salesforce as its authorization provider in the OpenID Connect dynamic client registration and token introspection flow.
- The API gateway registers a client app with the Salesforce dynamic client registration endpoint.
- The API gateway sends a request to the Salesforce authorization endpoint to approve a client app based on the authorization grant type associated with it.
- With a successful validation, Salesforce generates an access token for the client app.
- The API gateway sends a request to the Salesforce token introspection endpoint to validate the access token.
- After a successful validation, the API gateway allows the client app to access the protected data.
Now let’s put it all together.
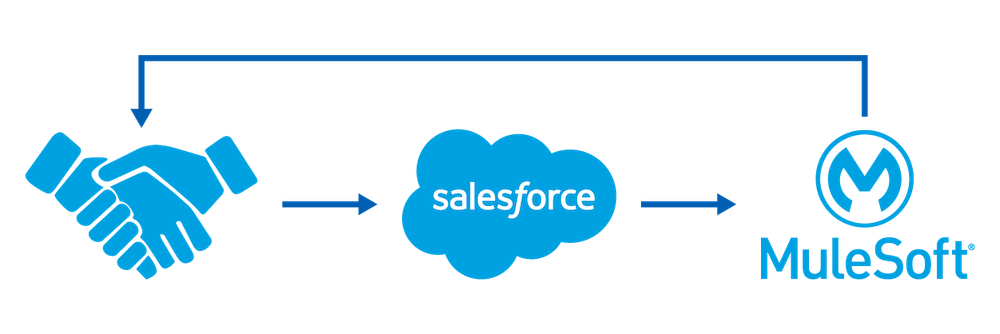
- Your Order Status API is available on MuleSoft’s API portal.
- Your partners log in to MuleSoft and create a client application to access the Order Status API.
- The new client app automatically sends a request to the Salesforce dynamic client registration endpoint to create a connected app for the client app.
- After a successful registration, Salesforce returns a client ID and client secret for the connected app, which is shared with the partner.
- The partner sends a request with the client credentials to the API gateway by specifying the grant type (authorization code) to approve the client with.
- The partner is redirected to a browser to log in to Salesforce, and to authorize access to data. This authorization is based on scopes associated with the corresponding connected app in Salesforce.
- With a successful authorization code grant flow, Salesforce sends an access token to the client app.
- The client app sends its access token to the API gateway, requesting access to the protected order status data.
- The API gateway extracts the access token and sends it to the Salesforce token introspection endpoint.
- Salesforce validates the access token.
- The API gateway grants the client app access to the data protected by your Order Status API hosted on MuleSoft.
You’ve Arrived at Base Camp
Congratulations! You’ve completed the Connected App Basics module. You should now feel comfortable knowing how you can use connected apps. In future connected app modules and projects, we show you how to create and configure connected apps for these use cases. In the meantime, know that you are well on your way to becoming a connected apps ace.