Explore Capture the Flag Events
Learning Objectives
After completing this unit, you’ll be able to:
- Describe Capture the Flag (CTF) competitions.
- List the various domains in CTF events.
- Explain the benefits of CTF challenges for different work roles.
Practice Capturing the Flag
One day you find yourself in a dusty attic, surrounded by old boxes and forgotten treasures. A worn leather-bound journal catches your eye. Inside, you find a handwritten message stating:
“To the seeker of secrets, 57elcome to your first challeng450d0a. A hidden word 4cies within these pages, waiting to be de43iphered. The keys are curiosity and 4fbservation, two critical skills that you will need to unlock this and 4dany other secrets to come. Good luck on your journ45y!”

The Challenge
Examine the message carefully. A hidden flag (solution) is embedded in the text. Once you find the flag, format it as follows.
CTF{flag}
This is a Capture the Flag challenge, a type of problem-solving task where points are awarded for correct solutions. Notice that the challenge is like a puzzle or riddle—a common CTF trait. If you feel a bit unsure of where to begin, this is normal too!
The Solution
The solution, or flag, is CTF{WELCOME}. There are characters in the message written in hexadecimal, a base-16 number system. Use any online hex to text tool to translate those characters (for example, 57 is hexadecimal for W).
Congratulations on completing this introductory CTF challenge! Regardless of whether you found the flag, you've gained valuable insight into the world of CTFs.
In this module we explain the purpose and benefits of a CTF activity and why these are great activities to participate in as you sharpen your cybersecurity skills.
What Is Capture the Flag?
Capture the Flag is a competitive cybersecurity game inspired by a traditional outdoor game, similar to football and soccer, where two teams compete to capture each other’s flag. The flag is typically a hidden text string (similar to our previous example). But flags have evolved to include various forms of valuable data. These include a sequence of bytes hidden in a file, images, hashes, decrypted information, and even proof of access demonstrating the ability to exploit a vulnerability.
CTF events serve as training exercises to develop and enhance cybersecurity skills, promote teamwork, and foster a deeper understanding of offensive and defensive strategies in a simulated environment.
The challenges within CTFs require strategy, teamwork, and quick decision-making, mirroring the skills needed in real-world cybersecurity scenarios. Due to this, CTFs have become a popular tool for training and recruitment in various professions. They’re created and hosted by individuals and organizations from diverse fields, including education, government agencies, businesses, and IT vendors.
CTFs can be played both online and in-person, offering a variety of challenges for beginners to seasoned experts. Anyone with an interest in cybersecurity can participate in CTFs, but you typically find the following groups at competitions.
- Students (middle school to university level)
- Cybersecurity professionals (entry level to experienced) from various industries
- Academic researchers
- Military and government personnel
Many CTFs offer cash prizes for winning teams, adding an extra layer of excitement and competition.
This broad participation promotes a collaborative environment. Aspiring and current cybersecurity professionals from different backgrounds come together to learn, compete, and share knowledge, ultimately strengthening the cybersecurity community as a whole. Many well-known CTFs can be found on the CTFtime website.
Capture the Flag Categories and Domains
CTF competitions are popular with seasoned and aspiring cybersecurity professionals due to their immersive, hands-on approach to practicing security and defense within a controlled, risk-free environment.
Competitions primarily fall into three categories.
-
Jeopardy: This format requires participants to choose challenges from different cybersecurity domains and earn points for solving them.
-
Attack and Defense: Participants are divided into teams, each tasked with safeguarding their own systems while simultaneously attempting to breach their opponents’.
-
King of the Hill: A variant of Attack and Defense, this format challenges teams to establish and maintain control over the most computers possible within a designated network.
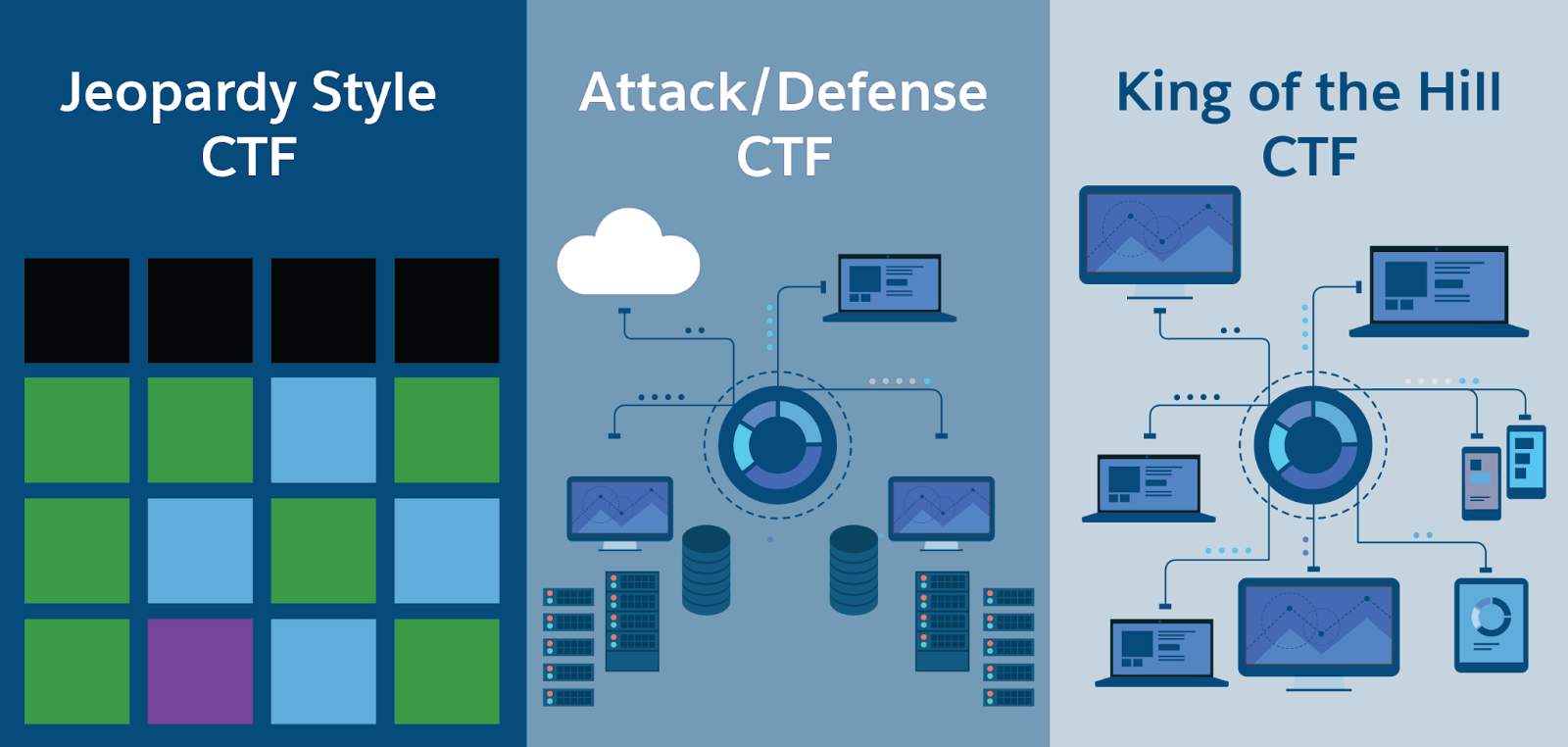
Within these three CTF categories, there are a variety of challenge types, each providing opportunities to apply and expand your knowledge and skill.
Domain |
Description |
Useful Knowledge and Skills |
|---|---|---|
Cryptography |
Involves bypassing encryption, decrypting messages, and implementing cryptographic protocols (like secure key exchange). |
|
Reverse engineering |
Requires translating a compiled program (machine code, bytecode) back into a format that's easier for people to read and understand. |
|
Web exploitation |
Focuses on testing websites and apps for vulnerabilities in code that would allow for things like SQL injection, or cross-site scripting (XSS). |
|
Forensics |
Involves analyzing digital evidence like files, logs, and even deleted data to figure out what happened during a cyber attack. |
|
Steganography |
Involves hiding and discovering information within other data, such as images or audio files, often used for covert communication. |
|
There are different levels of difficulty within each domain, ranging from beginner-friendly to highly advanced. The challenges you encounter will depend on the specific CTF competition and its intended target audience.
The Significance of the Flag
In capture the flag competitions, the flag is the solution that solves the challenge. However, in the real world the flag represents vulnerabilities within information systems and the data they process, transmit, and store.
For example, in a cryptography CTF, finding the flag (the solution) might involve decrypting a message to reveal a string of code or a secret phrase. However, in a real-world business environment, the same CTF scenario can represent a threat actor discovering a vulnerability, not a flag. This vulnerability could stem from issues like using outdated or weak encryption algorithms or insecurely storing encryption keys. These weaknesses could enable a threat actor to easily crack the encryption resulting in various negative consequences.
When you explore resources like the Common Vulnerability Scoring System (CVSS), Common Weakness Enumeration (CWE), and the Open Web Application Security Project (OWASP) Top 10, you'll find a multitude of these flag–real-world security flaws. If these flaws are discovered and maliciously exploited, it can lead to compromised personal privacy, the spread of misinformation, and even threats to public safety.
As cybersecurity professionals, it’s our responsibility to find and secure these vulnerabilities to prevent malicious actors from exploiting them in businesses, nonprofits, governments, and even in our homes.
The Evolving CTF Landscape
CTFs have been around for a long time–the first US-based CTF, DEFCON, was held in 1996. Today, CTFs continue to play a vital role in the global cybersecurity community. And their versatility and ability to quickly adapt to the landscape are especially useful as businesses continue to adopt and invest in emerging technologies. With the rise of social media, CTFs started to include challenges involving open source intelligence (OSINT), which is the practice of collecting information from publicly available sources.
The Internet of Things (IoT), cloud computing, and connected vehicles have expanded the landscape even further. This led to CTF challenges like Ph0wn, a CTF dedicated to smart devices and ESCRYPT CTF, an immersive environment where participants exercise their automotive cybersecurity skills. Finally, MITRE’s Embedded Capture the Flag sets itself apart from traditional CTFs by focusing on securing embedded systems, the specialized computers hidden inside devices like cars, medical equipment, and industrial control systems.
CTFs for Nontechnical Professionals
While CTFs have historically focused on technical skills like forensics, cryptography, and reverse engineering, the increasing prevalence of social engineering attacks that exploit human vulnerabilities has highlighted the need for a broader focus. Effective cybersecurity now demands not only technical expertise but also a deep understanding of risk management, policy, and the human factors that attackers exploit.
In response to this change, new CTF formats have emerged. For example, the DEFCON Social Engineering CTF (SECTF) has gained popularity, attracting a wider range of participants with diverse skill sets. The Cyber 9/12 Strategy Challenge is primarily a policy and strategy competition where participants analyze a fictional cyber crisis scenario and develop policy recommendations. For example, a team may analyze the technical details of an attack, identify the threat actor, and assess the potential impact to national security and the economy. The flag in this context could be the successful development of a policy response that addresses the various challenges of the cyberattack. This solution demonstrates their understanding of the technical, legal, and geopolitical issues involved.
These new formats are important because defending against attacks that target human weaknesses—such as curiosity, urgency, fear, overconfidence, or lack of awareness—and including administrative security controls (for example, cybersecurity policy and risk management practices) requires a different approach than traditional technical challenges. Participants in these CTFs must actively listen, communicate, persuade, critically think, understand policy and compliance, recognize psychological manipulation techniques, and possess knowledge of ethical frameworks and guidelines.
By incorporating social engineering and cyber governance scenarios into CTFs, participants can learn to identify and respond to technical threats more effectively, ultimately enhancing their overall cybersecurity awareness and resilience.

Beyond introducing nontechnical challenges into existing technical CTFs, it’s equally important to create an inclusive environment where nontechnical cyber professionals feel empowered to participate and contribute. The table illustrates how different CTF technical domains naturally align to the work of nontechnical professionals and how those domains can be enhanced to include nontechnical challenges.
Role |
CTF technical domains and relevance to the nontechnical role |
Benefits for nontechnical professionals |
Domain enhancements |
New and enhanced knowledge and skills |
|---|---|---|---|---|
Cybersecurity risk analyst |
Cryptography: Understand how encryption protects data. |
Gain insights into how technical breaches occur, improving risk assessment and management. |
Add challenges related to social engineering detection and policy analysis. |
|
Cybersecurity auditor |
Forensics: Analyze digital evidence of incidents. Web exploitation: Identify and understand vulnerabilities in web applications. |
Better understand technical details to improve audit accuracy and compliance checks. |
Incorporate policy evaluation and social engineering mitigation scenarios. |
|
Project manager |
Forensics: Understand the steps involved in digital investigations. Web exploitation: Gain insight into common vulnerabilities that need to be mitigated. |
Improve management of cybersecurity projects and communication with technical teams. |
Include scenarios requiring coordination of policy and governance during incidents |
|
Cybersecurity policy analyst |
Forensics: Understand the technical aspects of incidents that policies aim to address. |
Develop practical policies based on real technical incident analysis. |
Integrate policy development and social engineering countermeasure evaluation tasks. |
|
By promoting collaboration and knowledge exchange between technical and nontechnical participants, CTFs can better reflect the diverse skill sets needed to tackle the multifaceted challenges of modern cybersecurity in various business environments. By participating in these CTFs, nontechnical cybersecurity professionals can enhance their current skills and develop new technical and nontechnical competencies that are valuable for their roles.
In this unit, we defined CTFs, listed the various CTF types and domains, and explained the significance of the flag. We discussed how the landscape is evolving to be more inclusive. And we explored the potential benefits of introducing nontechnical challenges into technical domains. In the next unit, we create a step-by-step CTF success strategy to help you confidently navigate any CTF challenge.
Resources
- Trailhead: A Career in Cybersecurity
- External Site: SANS: Gamified Learning: Using Capture the Flag Challenges to Supplement Cybersecurity Training
- External Site: 7 Lessons Learned from Designing a DEF CON CTF
- External Site: Cybersecurity knowledge and skills taught in capture the flag challenges
- External Site: Why Playing Capture the Flag Will Make You a Cyber Elite
- External Site: CTFtime
- External Site: Top 10 Cyber Hacking Competitions–Capture the Flag (CTF)
- Video: Fortinet: MITRE eCTF