Learn the Business Impact of Data Loss
Learning Objectives
After completing this unit, you’ll be able to:
- Describe the importance of protecting data.
- Identify common data threats.
- Summarize the customer’s role in the Shared Responsibility Model.
- Explain the value of having a dedicated backup-and-recovery solution.
The Importance of Protecting Data
Today, as businesses seek to scale in the midst of constant technological transformation and increasing remote and hybrid work, they’re relying more on cloud-based tools to store and manage data. This data—including account records, sales opportunities, customer contact details, contracts, and employee information—is incredibly valuable, as it tells the entire story of a business and its customers.

But while data is becoming increasingly valuable, it’s also becoming increasingly vulnerable. According to a 2021 survey conducted by Forrester Research, a vast majority of organizations suffered a data loss or corruption incident in their software as a service (SaaS) application within the previous year. And to add insult to injury, that same study found that fewer than 50% of those organizations were able to recover their lost or corrupted data in a timely manner.
Data loss and corruption events—which sometimes go unnoticed or remain unresolved for days or even weeks—can have a devastating impact on an entire company, resulting in:
- Increased labor costs
- Reduced productivity
- Data-recovery fees
- Compliance fines
- Decreased revenue
- Loss of reputation
Businesses are now recognizing that it’s not a matter of if they’ll lose data, but when they’ll lose data. Because of this, they’re prioritizing proactive data protection and security to head off pervasive data threats.
So, what are the biggest threats to data? They’re probably not what you think.
Common Data Threats
Cyberattacks and data breaches usually make headlines, but you might be surprised to learn that many data loss and corruption events are not catastrophic or nefarious.

Let’s take a closer look at the top threats to SaaS data.
Threat |
Description |
|---|---|
Human Errors |
Simple mistakes—such as mass deletions, data overwrites, and excessive admin privileges—are one of the main causes of data loss and corruption. According to the Own 2021 State of SaaS Data Protection annual report, human error was one of the leading causes of Salesforce data loss, accounting for nearly half of all loss and corruption incidents. |
Integration Errors |
Default configurations or changes made to configurations while integrating other internal systems and applications can cause unexpected behavior that results in data loss or corruption. |
Migration Errors |
Migrations—for example, from one Salesforce instance to another—are ideal for moving and consolidating large volumes of data and completing complex transformations, but they often pose a risk of incorrect data overwriting. |
Bad Code |
While working on applications, workflows, and system updates, developers, and administrators can affect data across many different objects in a company’s Salesforce environment. Using poorly tested code or irrelevant test data can cause serious data and metadata corruptions in production. |
Cyberattacks/Malicious Intent |
Ransomware attacks, malware attacks, and identity theft certainly wreak havoc on data. But threats can be much closer to home—disgruntled employees can delete or overwrite live data and empty the recycling bin… leaving you high and dry when it comes to recovery. |
Despite the prevalence of these data threats and the steep consequences of data loss and corruption, many people still have a false sense of data security and wrongly assume that their cloud service provider (CSP) is solely responsible for protecting their data. Approximately 40% of survey respondents in the Own 2021 State of SaaS Data Protection annual report said that their SaaS provider was responsible—or that they weren’t sure who was responsible—for data protection and recovery.
The reality is that CSPs and customers are both obligated to protect data through what’s known as the Shared Responsibility Model.
The Shared Responsibility Model
The Shared Responsibility Model is a cloud-security framework that clearly defines the data-protection responsibilities of CSPs and customers.
- CSPs (like Salesforce) are responsible for security of the cloud; that is, they’re responsible for configuring, managing, and securing applications, network controls, and the host infrastructure.
- Customers are responsible for security in the cloud; that is, they’re responsible for configuring, managing, and securing all data stored in the cloud, devices, and account access and management.
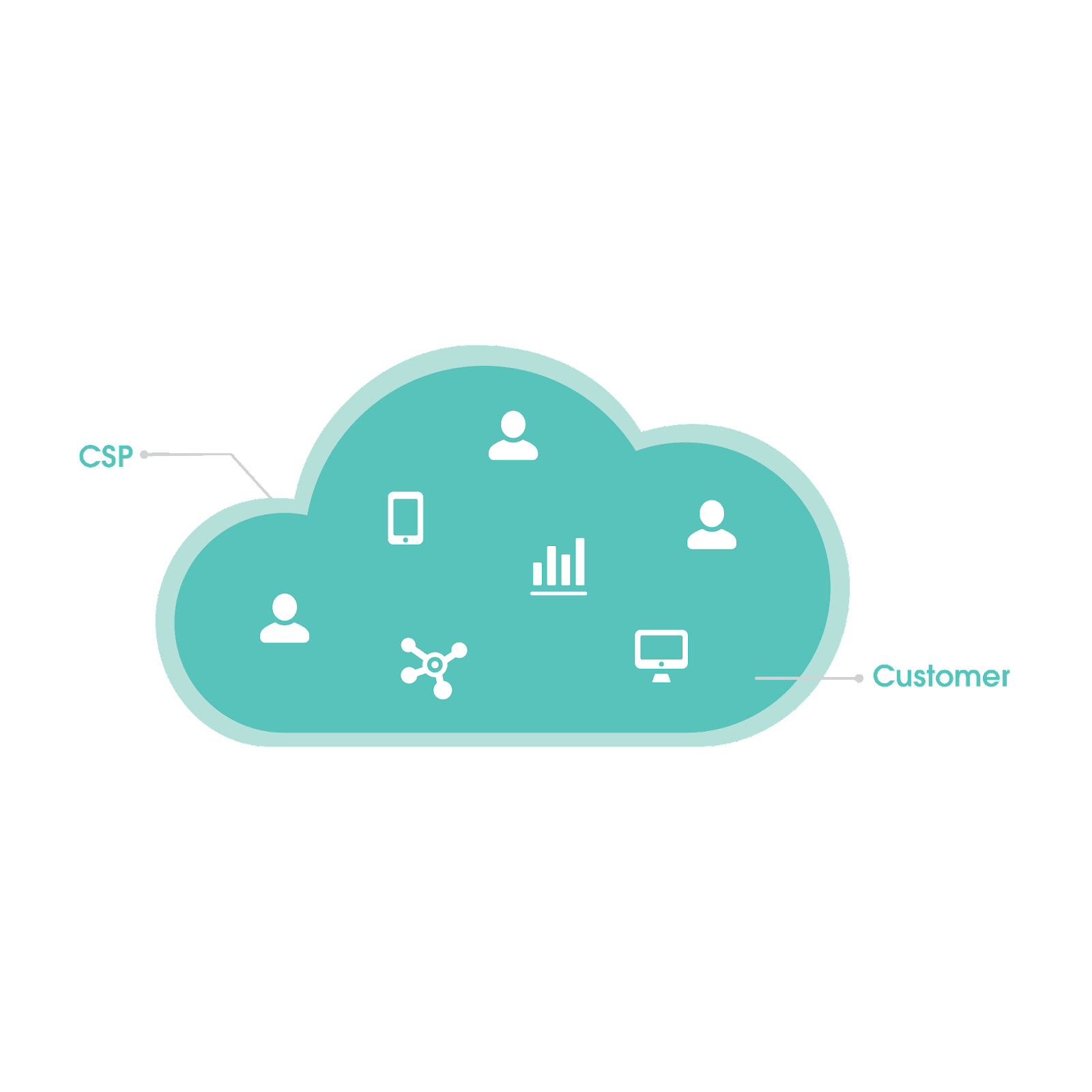
Although all CSPs adhere to the Shared Responsibility Model, the customer has varying levels of responsibility depending on whether the CSP provides infrastructure as a service (IaaS), platform as a service (PaaS), or software as a service (SaaS).
Salesforce, as an SaaS, provides a secure platform, but customers must understand their role in maintaining—and potentially jeopardizing—data security. According to Gartner, customers will be the cause of 99% of cloud-security failures and the resulting data loss through 2025! That’s why it’s so critical to have a dedicated backup-and-recovery solution.
The Value of Backup and Recovery
A backup-and-recovery solution not only helps an organization fulfill its data-protection obligations under the Shared Responsibility Model, but it also serves as a key element in an effective business continuity plan (BCP). A BCP proactively defines the process a company will follow to deal with any potential data threats and limit disruptions to operations.
One of the most important steps in creating a BCP for your Salesforce data is establishing your recovery point objective (RPO) and your recovery time objective (RTO).
-
RPO is a measurement of how much data your organization can afford to lose before it impacts business operations. It is an indicator of how often you should back up your data.
-
RTO is the timeframe in which you must restore your lost or corrupted data in order to prevent irreparable harm to the business. The timeframe takes into account tasks such as identifying, finding, preparing to restore, and actually restoring the lost data.
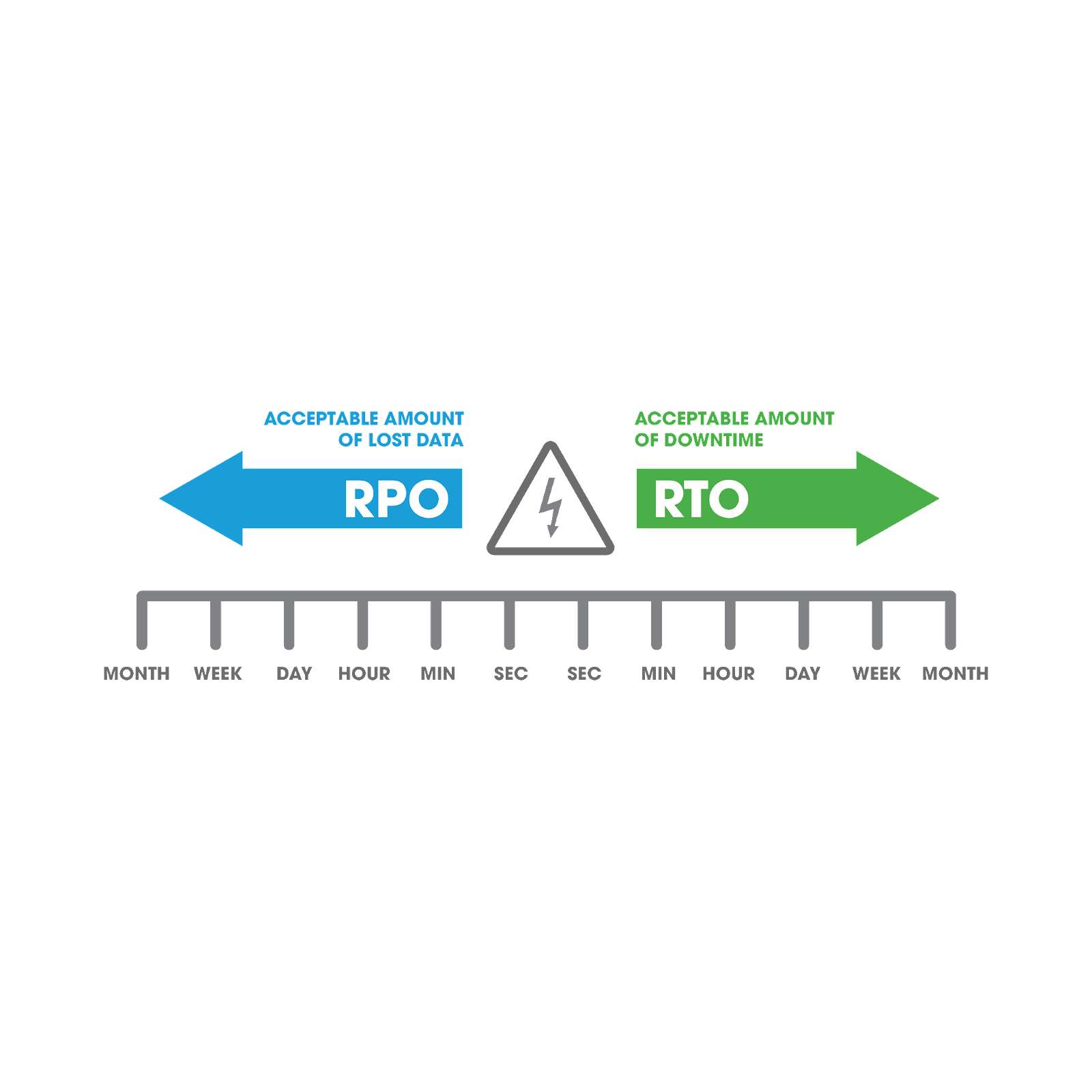
A comprehensive backup-and-recovery solution such as Own Recover helps minimize the amount of data your organization will lose (RPO) and the amount of time it will take to recover from that loss (RTO). Recover mitigates catastrophic incidents of data loss and corruption but also protects mission-critical SaaS data and keeps teams on track as they complete their day-to-day business.
In addition, having a dedicated backup and recovery third-party solution helps your organization establish data independence. Not only does it ensure backup data is always accessible to users (in the case of a service outage) but it also ensures that your backup data will live beyond your relationship with your SaaS vendor.
Want to learn more about the features of Recover and how they proactively empower teams to safely deploy changes to Salesforce? Then, keep reading! We cover it all in the next unit.
Resources
-
Data Sheet: Own: SaaS Data Loss by the Numbers
-
Trailhead Module: Sandbox Seeding with Own
-
Article: Gartner: Is the Cloud Secure?
-
Blog Post: Own: Backing Up Your Salesforce Data Using a Full Sandbox
-
Ebook: Own: Shared Responsibility Playbook
-
Blog Post: Own: Using RTO and RPO to Minimize Downtime for Your Organization
-
Ebook: Own: The Complete Data Backup and Recovery Guide for Salesforce
-
Ebook: Own: How Independent Backup Helps Mitigate The Impact of SaaS Data Loss
-
Article: Own: Why Back Up Your Salesforce Metadata?
