Learn About AI Threats and Defenses
Learning Objectives
After completing this unit, you’ll be able to:
- Identify AI risks and defense strategies for everyday applications.
- Describe the role of cyber defenders in protecting systems, users, and businesses.
As we advance further into the realm of artificial intelligence (AI), the understanding of its ethical considerations and security protocols becomes more important. Remember, AI not only offers revolutionary conveniences but also introduces potential risks.
Let’s briefly touch upon these dual dimensions before proceeding to a vital topic—AI cyberattacks and defenses.
AI Cyber Attacks and Defenses
As the role of AI expands into everyday life—like helping you choose a movie to watch, keeping an eye on your home security, or even assisting your kids with their homework—it’s important to know that this convenience comes with a set of risks. Just as we’ve seen technology evolve, so have the tactics of those looking to exploit it.
Understanding the Risks of Everyday AI Use
First, there are attacks on the AI systems themselves.
-
Poisoning the algorithm: Think of this as feeding the AI bad information to get wrong answers. Imagine if the GPS in your car was deliberately misdirected, sending you to the wrong location.
-
Data tampering: This would be like changing the ingredients in a recipe that your smart kitchen follows, potentially resulting in a meal that’s not what you expected—or wanted.
-
Unauthorized access: Imagine if someone could whisper secret commands to your voice-activated home assistant, controlling it without your permission.
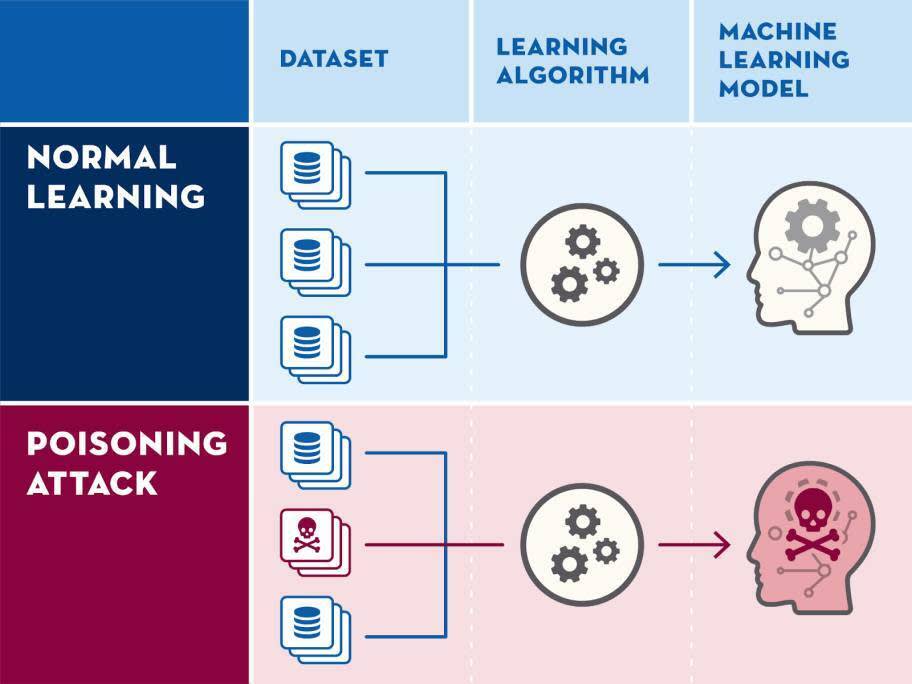
Second, there are risks that directly affect you.
-
Digital impersonation: You've probably heard of deepfakes, where someone's likeness and voice can be recreated with scary accuracy. It could be used to fake a message from a trusted friend or family member.
-
AI-driven scams: Ever received an email or text that seemed legit but felt a bit off? AI can generate very convincing scam messages designed to trick you into revealing sensitive information.
-
Smart malware: These are viruses or harmful software that can adapt and learn from your behavior. For example, if you frequently shop online, the malware might target your payment information.
And finally, risks that could affect your workplace or broader community.
-
Corporate data tampering: If a business relies on AI for operations, messing with that AI could result in actions that go against the company’s interests.
-
Reputation damage: For businesses that use AI to interact with customers, if that AI system gets compromised, it could lead to a loss of trust.
Users have a significant role to play in keeping AI safe and ethical. While some controls are beyond the end-user’s reach, there are actionable steps within your sphere of influence to keep your experience with AI both secure and ethically sound at home and at work. Here’s what you can do.
-
Be informed: Read the privacy policy and terms of service of any AI-driven application or service you use. Know exactly what data is being collected and how it's being used.
-
Update regularly: Keep your applications and software updated. By doing so, you receive not only the latest security patches, but also patches that address ethical considerations within the AI system.
-
Enable security settings: Use all available security options like two-factor authentication, especially for AI-driven services that have access to your personal data.
-
Review and audit: Periodically review the data you've shared with AI systems. Delete unnecessary information and adjust settings to limit data exposure.
-
Be skeptical: If a message or video seems off, it probably is. Be cautious and verify information before sharing or acting on it.
-
Educate others: Share your knowledge and insights about the ethical and security considerations of using AI with friends and family.
-
Report issues: If you come across biased or unethical behavior, report it. Reporting issues depends on the context in which you encounter the problematic AI behavior.
-
Service provider: The first point of contact should be the company or organization that provides the AI service. Most platforms have a reporting mechanism for security or ethical issues.
-
Regulatory bodies: For more severe cases, especially those involving privacy or discrimination, you may need to report the issue to relevant governmental or regulatory bodies like the Federal Trade Commission (FTC) or Equal Employment Opportunity Commission (EEOC) in the US or similar entities in international jurisdictions.
-
Internal channels: If the AI system is provided by your employer for workplace use, report the issue to the IT department or a designated ethics committee, if there is one.
-
Developer groups: If it’s open-source software, you can usually report issues directly to the developers through repositories like GitHub.
By taking these steps, you contribute to a culture of safety and ethical responsibility in the AI space. It’s not just about enjoying the perks of smart technology; it’s about using it wisely.
As we delve deeper into an AI-centric world, recognizing and mitigating these specific threats becomes paramount for safeguarding our digital future.
AI and Cyber Defense
For all the challenges AI brings, it also promises transformative solutions in cybersecurity. Equipped with AI, cyber defenders can actively defend against AI-based attacks by leveraging a host of techniques and technologies. Let’s dig a little deeper and review the ways AI can help in cyber defense practices.
|
Cybersecurity’s role
|
Protect and defend techniques and technologies
|
|---|---|
Protecting the AI system |
|
Safeguarding people |
|
Defending the business mission |
|
By harnessing the capabilities of AI, cybersecurity can actively and efficiently defend against the myriad threats posed by malicious attacks against and by AI. While the challenge is ever-evolving, the integration of AI into cybersecurity can produce a dynamic, adaptive, and robust defense mechanism tailored for the modern digital age.

Charting a Path Forward
The intersection of artificial intelligence and cybersecurity presents a paradigm shift that resonates deeply with every cybersecurity professional. The complexities and potential of AI not only redefine the technological landscape but also sculpt new avenues for skill enhancement, knowledge acquisition, and performance impact.
At the heart of this transition is the realization that AI’s capabilities are matched only by its vulnerabilities. For cybersecurity professionals, this translates to expansive opportunities like the following.
-
Education and training: As AI models become more intricate, so does the need for deepening our understanding. Tailored courses and certifications focusing on AI-centric cybersecurity will soon become not just desirable, but essential.
-
Skill augmentation: The tools and techniques that sufficed yesterday might not hold against tomorrow’s AI-driven threats. Continuous skills development in threat detection and analysis, automated incident response strategies, and ethical considerations when deploying AI, is paramount.
-
Amplified impact: With AI integration into industries, the role of cybersecurity expands from protecting systems to shaping business trajectories. A well-secured AI model can drive business growth, enhance user trust, and ensure ethical adherence.
The future, with its AI-driven advancements, requires adaptation and innovation. By embracing continuous learning, refining skills, and aiming for greater impactful contributions, cybersecurity professionals won’t just navigate the AI landscape—they’ll define it.
Sum It Up
In this module, you’ve been introduced to AI in our professional and personal lives and to the ethical and security implications of AI. You’ve also learned about AI cyberattacks and the ways we can defend against them. Equipped with this understanding, you are now able to both champion AI’s innovations and fortify its defenses!
Interested in learning more about cybersecurity roles and hearing from security professionals? Check out the Cybersecurity Career Path on Trailhead.
Resources
- External Site: The Digital World Is Changing Rapidly. Your Cybersecurity Needs to Keep Up
- External Site: OWASP AI Security and Privacy Guide
- External Site: Introducing Google’s Secure AI Framework
- External Site: Artificial Intelligence In Cybersecurity: Unlocking Benefits And Confronting Challenges
- External Site: Aspen Digital: Navigating Uncharted Waters